Microsoft Warns of ‘Ice Phishing’ Threat on Web3 and Decentralized Networks
Introduction:
Microsoft has warned emerging threats in the web3 landscape, including “phishing” campaigns, since a wave in the adoption of Block chain and Defi (Decentralised Finance) technologies emphasizes the need to create security on the decentralized web while still in their First stages.
(Web3: Web3 is an idea of a new iteration of the World Wide Web – based on block chain technology, which integrates concepts, including decentralization and the tokens-based economy.
Decentralization: Decentralization is the process that which an organization’s activities, particularly those concerning planning and decision-making, are distributed or delegated from a central place or group).
Main Concern:
Microsoft has issued a warning about growing risks in the Web3 ecosystem, including “ice phishing” operations. The Microsoft 365 Defender Search Team has identified a number of new ways that malicious actors could attempt to use cryptocurrency users to deliver on their private cryptographic keys and commit unauthorized financial transfers.
While attackers can utilize a similar tactic on web3 to get to your private key, given the current adoption, the likelihood of an email landing on the inbox of a cryptocurrency user is relatively low. Instead, different tactics can be employed to reach and trick cryptocurrency users into giving up their private key:
- Keeping an eye on social media for consumers contacting wallet software support and responding with direct messaging spoofing support in order to directly steal one’s private key.
- Giving out new tokens for free to a group of accounts (i.e., “Airdrop” tokens), then failing transactions on those tokens with an error message that redirects to a phishing website6 or a website that instals coin mining plugins that steal your credentials from your local device.
- Plagiarism and spoofing authentic smart contract front ends.
- Pretending to be wallet software and directly stealing private keys.
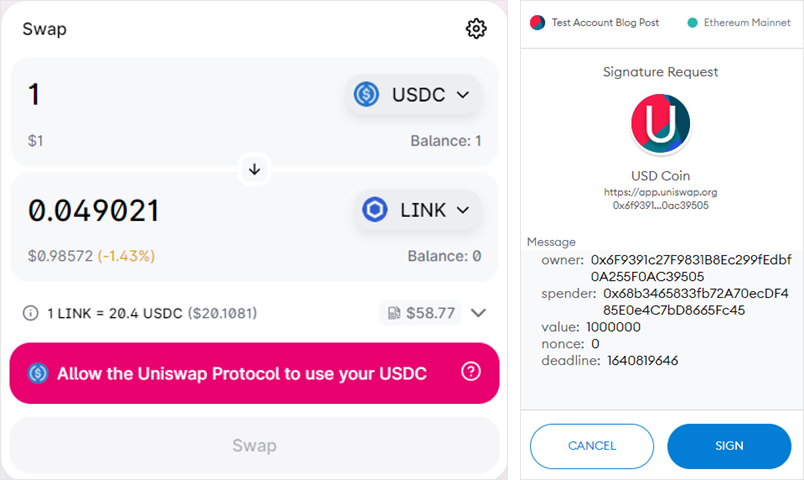
Researchers reported that, “The spender can access the cash once the permission transaction has been signed, filed, and mined. In the instance of a ‘ice phishing’ assault, the attacker can gather approvals over time and then swiftly drain all of the victim’s wallets.”
The script was designed to intercept Web3 transactions from wallets with a certain amount and inject a request for the victim’s tokens to be transferred to an address specified by the attackers.
Uniswap Transfer Flow:
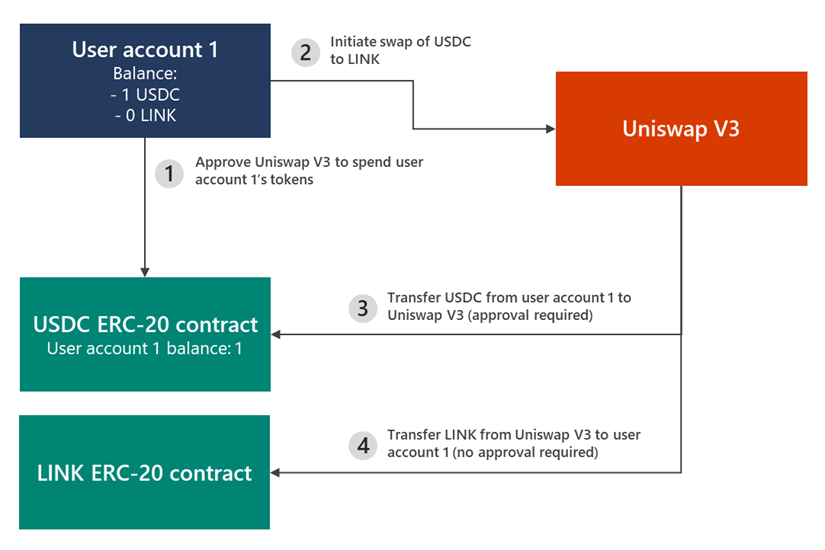
Our Recommendations:
For the threats influencing the block chain technology, users are required to:
- Evaluate and audit the clever contracts for suitable incident reaction or unexpected emergency abilities.
- Reassess and revoke the token allowances periodically.
For the threats prevailing from phishing, users are required to
- Keep Informed About Phishing Techniques.
- Install an Anti-Phishing Toolbar.
- Keep Your Browser Up to Date.
- Use Firewalls and Antivirus Software.
- Remain vigilant to all potential attacks while continuing to safeguard the sensitive information.
Organizations can get in touch with CyberSRC for raising phishing awareness among the employees through our “Phishing as a service’ campaigns.



