Email Hacking Bug Uncovered in Horde Webmail Software
Introduction:
The users of Horde Webmail are being urged to disable a function that contain a security vulnerability which is a nine-year old patch in the software that could be abused to get the full access to email by simply avoiding an attachment. This gives the attacker access to all the sensitive and maybe secret information that a victim has stored in his email account and could allow them to gain more.
Main Concept:
The challenge of the Horde is a conversation sequence without charge that allows consumers to navigate, send and organize emails, as well as manage and share calendars, contacts, responsibilities, notes, information and markers.
The fault, which has been introduced as part of an improvement of the extensive code on November 30, 2012, concerns a circumstance of a “strange” reflected XSS website script that allows an attacker to create An OpenOffice document. In this kind when it is previewed, it mechanically performs the arbitrary JavaScript payload.
Impact:
The vulnerability triggers when the victim views an attached OpenOffice document in the browser,” Scannell explained. “As a result, an attacker can steal all emails the target has sent and received. Even worse, when an administrator account with a custom and malicious email is compromised, the attacker could abuse this privileged entrance to take around the whole webmail server.
Our Recommendations:
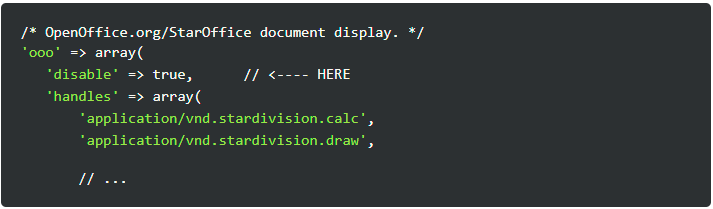
- Horde Webmail users are advised to disable the rendering of OpenOffice attachments by editing the config/mime_drivers.phpfile to add the ‘disable’ => true configuration option to OpenOffice mime handler as shown below:
2. If you have to open an attachment before you can verify the source, take the following steps:
a) Be sure the signatures in your antivirus software are up to date.
b) Save the file to your computer or a disk.
c) Manually scan the file using your antivirus software
d) If the file is clean and doesn’t seem suspicious, go ahead and open it.



