To Amplify DDoS Attacks Hackers Abuse Mitel Device
Introduction
Mitel device are misused by hackers to amplify DDoS attacks for up to 14 hours. The amplification of attack breaks the record ratio of 4,294,967,296 to 1.
TP240PhoneHome (CVE-2022-26143) is used as a weapon by threat actor to launch significant DDoS attacks that targets the broadband access ISPs, financial institutions, logistics companies, gaming firms and other organizations.
According to Akamai researcher Chad Seaman in a joint advisory, “Approximately 2,600 Mitel MiCollab and MiVoice Business Express collaboration systems acting as PBX-to-Internet gateways were incorrectly deployed with an exploit system test facility exposed to the public Internet.”
Technique used in attack
To launch reflection/amplification DDoS attack of more than 53 million packets per seconds (PPS) the attacker actively force the system. DDoS reflection attacks involves spoofing the IP address of a victim to redirect response from a target such as DNS, NTP or CLADP server, where the replies are sent to the spoofed sender that are much bigger than the requests. This leads to the completely unavailability of the service.
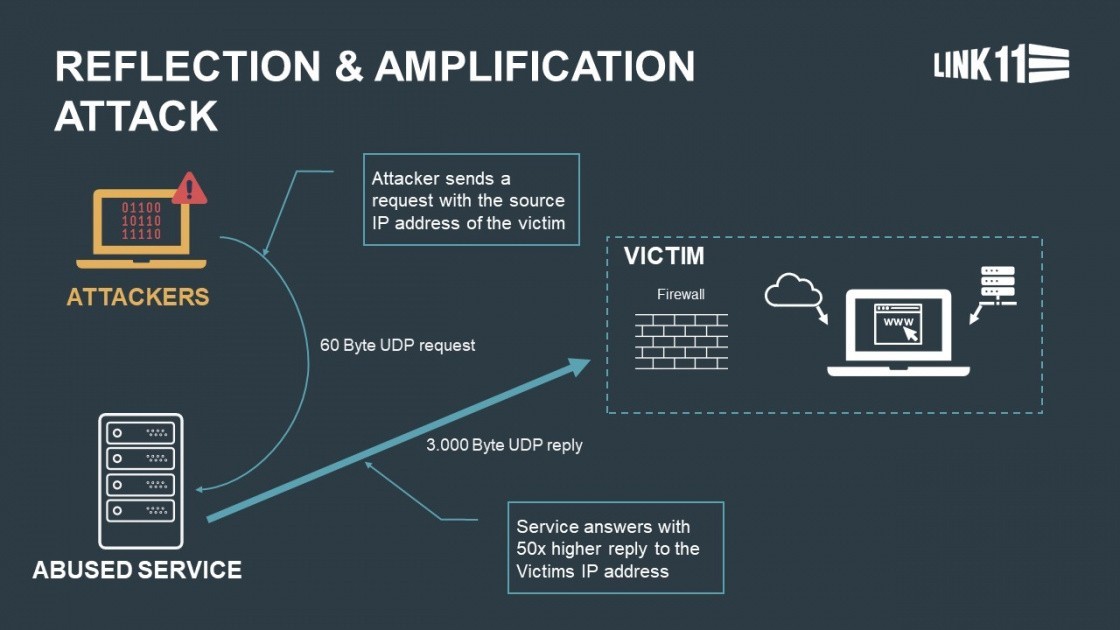
This attack is detected on February 18, 2022. Due to the inadvertent exposure of an unauthenticated test facility to the public internet. This type of attack is differ from most UDP attack methodologies that uses single spoofed attack initiated packet, that result in a record –setting packet amplification ratio of 4,294,967,296:1.
On Tuesday March 8, 2022, Mitel released software updates after the discovery, it disable the public access to the test feature, while describing the issue as an access control vulnerability that could be exploited to obtain sensitive information.
Abusing the TP-240
The abused service on affected Mitel system is called tp240dvr (“TP-240 driver”) that appears to run as a software bridge to facilitate interactions with TDM/VoIP PCI interface cards. The service listens for commands on UDP/10074 and is not meant to be exposed to the internet, as confirmed by the manufacturer of these devices. But somehow it gets the exposure to the internet that ultimately allows it to be abused.
The tp240dvr service exposes an unusual command that is designed to stress test its clients in order to facilitate debugging and performance testing. This command can be abused to cause the tp240dvr service to send this stress test to attack victims. The traffic consist of a high rate of short informative status update packets that can potentially overwhelm victims and cause the DDoS scenario.
Impact of TP-240
Mitel, MiCollab and MiVoice Business Express collaboration systems that are abused as DDoS reflectors/amplifiers. The impacts are as:-
- Partial or full interruption of voice communication
- Service disruption due to transit capacity consumption
- State-table exhaustion of network address translations
- Stateful firewalls
Remedies:
- Implement a DDoS attack response plan
- Secure the infrastructure with DDoS attack prevention solution
- Look for the warning signs of a DDoS attack.
- Adopt cloud based service provider
- Improve network security



