New Unix rootkit used to steal ATM Banking Data
Introduction
Threat analyst found a financially motivated group of hackers, report the discovery of a previously unknown Unix rootkit that is used to steal ATM banking data and conduct fraudulent transaction. The goal is to compromise ATM, switching networks and carry out unauthorized cash withdrawals at different banks using false/dishonest card.
Mandiant said in a report that researchers present evidence about the activities of LightBasin that focus on bank card fraud and the compromise of crucial system.
What are rootkits?
These are designed with unique ability to reside in the kernel of the operating system. A rootkit is always bundled with data-stealing malware, such as banking Trojans and Zeus viruses. It may also come with ransomware.
How they enter in the banking data?
The new new rootkit is a Unix kernel module that named as “Caketap”. It is deployed on servers running the Oracle Solaris operating system.
Caketap hides network connections, processes and files during loading and install several hooks into the system to receive remote commands and configurations.
The commands observed by the analyst are:
- Add the CAKETAP module back to the loaded modules list
- Change the signal string for the getdents64 hook
- Add a network filter
- Remove a network filter
- Set the current thread TTY to not be filtered by the getdents64 hook
- Set all TTYs to be filtered by the getdents64 hook
- Display the current configuration
Goal of Caketap
Caketap’s goal is to steal banking card information and PIN verification data from compromised ATM switch servers and then use the stolen data to facilitate unauthorized transactions.
The Caketap intercept messages that are destined for the Payment hardware Security Module (HSM), which are used in the banking industry for generate, manage, and validate cryptographic keys for PINs, magnetic stripes and EMV chips.
Caketap intercepts the card verification messages, stops them from matching fraudulent bank cards, and generates a valid response in their place.
It then saves valid messages that match non-fraudulent PANs internally and sends them to the HSM so that customer transactions do not get affected and the implant operations remain hidden.
In a larger operation, UNC2891 (LightBasin) successfully used fraudulent bank cards to withdraw unauthorized cash from ATM machines at several banks by leveraging CAKETAPE.
Slapstick, Tinyshell, Steelhound, Steelcorgi, Wingjook, Wingcrack, Binbash, Wiperight and Mignogcleaner are the other tools related to the actor in previous LightBasin attacks. All of these tools have been confirmed by Mandiant and are still being used.
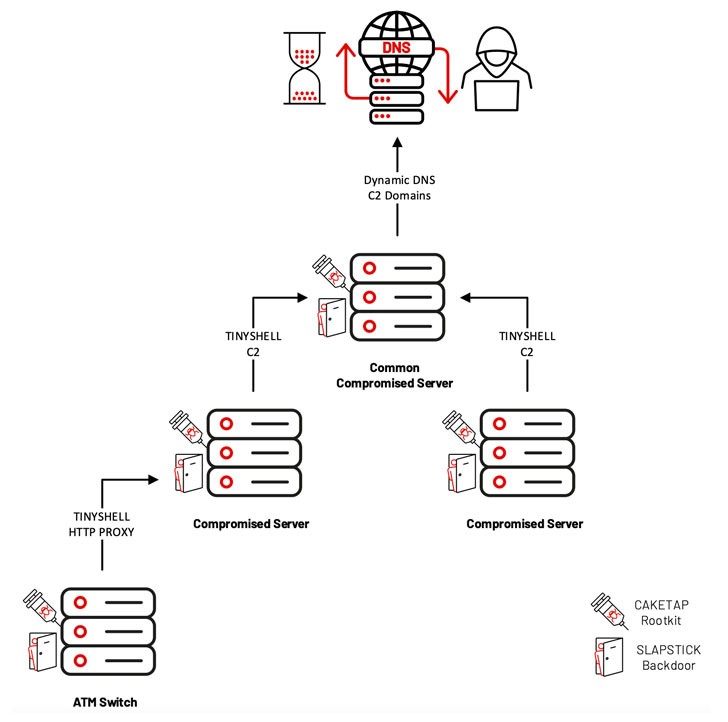
LightBasin uses Caketap, Slapstick and Tinyshell in every step (Mandiant)
LightBasin is a highly skillful threat actor that takes advantages of relaxed security in mission-critical Unix and Linux systems that are often treated as naturally secure or largely ignored due to their non-recognition.
Remedies:
Prevention is always better than cure. To avoid such kind of attacks try to follow these precautions:
- Avoid opening suspicious email
- Avoid downloading the cracked software
- Always keep the software updated
- Install anti malware software with rootkit detection



