GIMMICK Malware Attacks MacOS to Attack Organizations across Asia
Introduction
An espionage threat actor from China known for attacking target organizations across Asia has been linked to a new malware implant for macOS devices.
According to cyber security firm Volexity, the malware, dubbed Gimmick, is associated with a group tracked as Storm Cloud, and is a “feature-rich, multi-platform malware family that takes advantage of public cloud computing services (such as Google Drive) for command and control (C2) communication.”
Security researchers recovered the sample from a compromised MacBook Pro running macOS 11.6 (Big Sur) as part of an intrusion campaign that took place in late 2021.
Gimmick Malware (MacOS Variant)
Its windows counterpart, which is coded in both .net and Delphi, while the newly identified macOS variant, GIMMICK is written mostly on Objective C. The choice of the programming languages aside, the two version of the malware are known to share the same C2 infrastructure and behavioral patterns.
Volexity tracks the malware under the same name, regardless of the programming languages used and the operating systems targeted. However this happened due to following factors: –
- Shared C2 architecture
- File paths
- Behavioral patterns used by all variants
The GIMMICK workflow
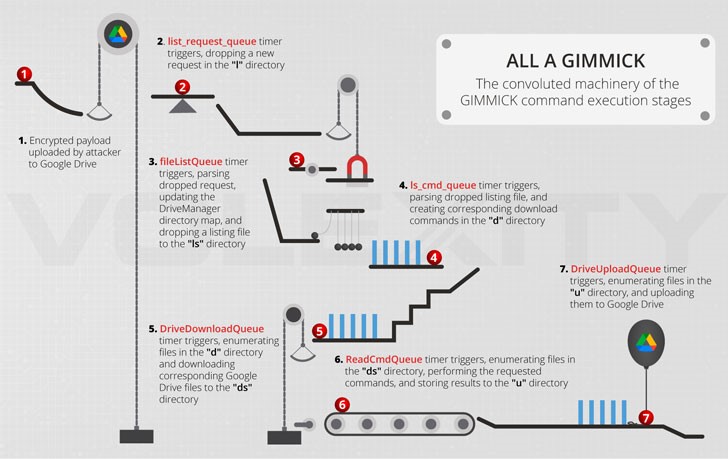
Volexity researchers Damien Cash, Steven Adair, and Thomas Lancaster said that “Storm Cloud is an advanced and versatile threat actor, adapting its toolset to match different operating systems used by its targets.”
To achieve their objective they make use of built-in operating system utilities, open source tools and custom malware. Utilizing cloud platforms for C2, like Google Drive, increases the probability of operating undetected by network monitoring solutions.
How the malware works?
Once it is installed, it can either run as an ‘application’ or a ‘daemon’ in the background. It is designed to mimic a program commonly used by the user.
The malware is configured to communicate with its Google Drive-based C2 server only on working days in order to further blend in with the network traffic in the target environment.
Besides retrieving arbitrary files and executing commands from the C2 server that comes with its own uninstall functionality that allow it to erase itself from the compromised machine.
To protect users from the malware, Apple has issued new signature to its built-in anti-malware protection suite known as XProtect that block and remove the infections via its Malware Removal Tool (MRT).
Custom Objective-C classes of GIMMICK
There are three custom Objective-C classes of GIMMICK malware, such as –
- Drive Manager
- File Manager
- GCDTimer Manager
Recommendations:
To prevent similar attacks Volexity has recommended the following mitigation:
- Ensure that persistence locations are always audited and monitored.
- Always monitor network traffic to identify anomalous proxy activity and internal scanning.
- Always use complex password.
- Make sure to enable a multi-factor security mechanism.
- Can use built-in anti-malware protection suite known as XProtect by Apple.



