New python-based Ransomware Targeting JupyterLab Web Notebooks
Introduction
A new Python-based ransomware strain has been discovered, the first of its kind to specifically target Jupyter notebooks, a web-based interactive computing platform that allows editing and running programs via a web browser.
In a report, Aqua Security’s Assaf Morag said the attackers gained access to the server via misconfigured environments before running a ransomware script that encrypts every file on a given path on the server and deletes itself after execution to conceal the attack. If organizations do not properly back up Jupyter notebooks, this attack can cause a significant amount of damage to their data analytics.
What is Jupyter Notebook?
Jupyter Notebook is an open source web application for working with data, writing and executing code, and displaying the results. A token or password typically restricts access to the online application, as well as limiting incoming traffic. Some of these notebooks are left exposed to the Internet without authentication, so anyone can access them via a web browser. In addition, Jupyter notebooks come with a built-in feature that enables users to open a shell terminal with access to the server.
Breaking down the Jupyter Notebook ransomware attack
According to the cloud security firm, the latest ransomware sample was executed after the unnamed attacker gained access to the server and downloaded the encryption tools in order to carry out the process by opening a terminal. A honeypot is setup with a Jupyter notebook application that exposed the attack on the internet. Below is the kill chain of the attack:
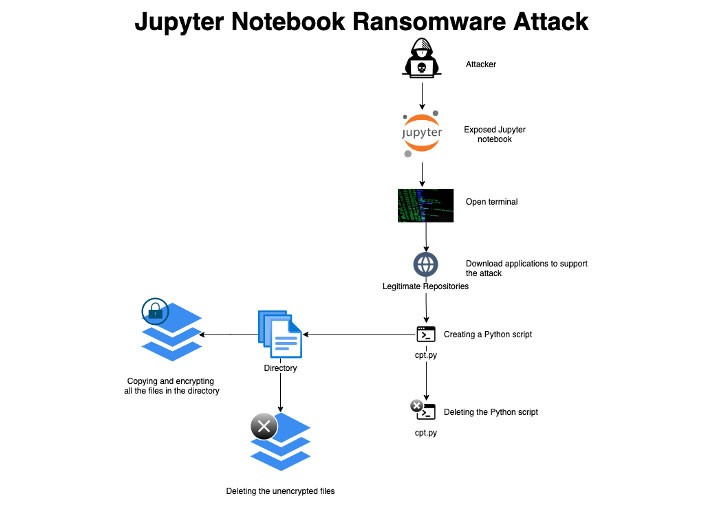
A misconfigured application allowed the attacker to connect to the server, download the libraries and tools (such as encryptors), and then manually create a ransomware script by pasting the Python code and executing it.
In order to simulate a real-life enterprise environment, the honeypot included Jupyter notebooks as well as raw data files the attacker could encrypt. It was stopped before further damage could be done. The python file (cpt.py) was designed to delete itself after the execution to conceal the attack.
There was no ransom note in this attack. It is possible that the adversary was experimenting with the attack on the machine, or the honeypot expired before the attack could be completed.
The attack is simple and straightforward compared to ransomware that uses advanced techniques, such as Locky, Ryuk, WannaCry, or ransomware-as-a-service, such as GandCrab.
To detect the attack use Tracee
Tracee of Aqua Security continuously monitors their honeypots, which are open source runtime security and forensics tools for Linux designed to address common Linux security issues. To detect the malicious event there are number of runtime security detection engines.
In this attack, Tracee detected two drift events, drooping and execution on the fly of a binary and a python file. The attacker downloaded a nano binary to create the file cpt.py and execute the binary along with the cpt.py script.
What is Honeypots?
A honeypot is a security mechanism that creates a virtual trap to lure attackers. An intentionally compromised computer system that allows attackers to exploit vulnerabilities so the organization can study to improve their security policies.
Recommendations:
There are a few recommendations that can be followed to mitigate these risks and protect the data applications: –
- Use tokens or another authentication method to control access to the data development application.
- Ensure that Secure Socket Layer is used to protect data while transmitting.
- Limit inbound traffic to the application either by blocking the internet access completely or if the environment requires internet access, by using network rules or VPN to control inbound traffic. Also, recommended to limit outbound access.
- Back up critical business system s regularly and consistently to avoid data loss.
- Identify exposures, vulnerabilities and misconfigurations that can provide entry points for attackers to gain access and compromise network.



