SOPHOS FIREWALL RCE VULNERABILITY UNDER ACTIVE EXPLOITATION
The Sophos firewall system has been determined to have a critical RCE vulnerability, according to a cybersecurity firm. Sophos has issued a warning that a significant security flaw in their “XG enterprise firewall” firewall solution is being regularly exploited in real-world attacks. Sophos has observed that this vulnerability is being used to target a small set of specific organizations primarily in the south Asia region.
Cause of the flaw
- CVE-2022-1040 – The issue has a CVSS score of8 out of 10 and affects Sophos firewall versions 18.5 MR3 (18.5.3) and older. It’s about an authentication bypass vulnerability in the user portal and web admin interface that, if exploited, might allow a remote attacker to run arbitrary code. The issue has been fixed in a hotfix that is installed automatically for clients who have enabled “allow automatic installation of hotfixes.” CVE-2022-1040 is currently being investigated.
Technique
Hackers abused the SQL injection bug to steal passwords. “The attack used a previously unknown SQL injection vulnerability to gain access to exposed XG devices”, Sophos said in a security advisory. Hackers targeted Sophos XG firewall devices that had their administration (HTTPS service) or the user portal control panel exposed on the internet. Hackers used the SQL injection vulnerability to download a payload on the device. This payload then stole files from XG firewall. Stolen data could include usernames and hashed passwords for the firewall device admin, for the firewall portal admins, and user accounts used for remote access to the device. it also included the firewall’s license and serial number, and user emails. Sophos said that the passwords for customer’s other external authentication systems, such as AD or LDAP, were unaffected. The company said that during its investigation, it did not find any evidence that hackers used the stolen passwords to access XG firewall devices, or anything beyond the firewall, on its customers’ internal networks. Sophos researchers named the malware Asnarok.
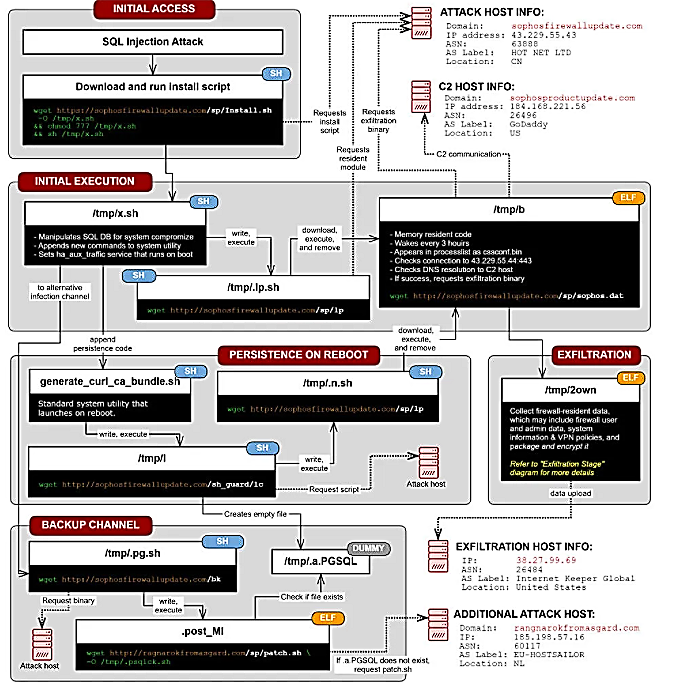
Recommendations:
- Ensure that the user portal and webadmin are not accessible to the WAN to protect themselves from external attackers.
- Follow device access best practices to disable WAN access to the user portal and webadmin, and instead utilize VPN and/or Sophos central for remote access and control.
- Users of previous versions of the Sophos firewall must upgrade in order to receive the most up-to-date security.
- Users have to install version which are above the 18.5.3 version.
Sophos recommends a variety of procedures for businesses that have had their devices hacked:
- Reset the accounts of the portal administrator and the device administrator.
- Restart your XG gadget (s)
- Reset all local user accounts’ passwords
- Even though the passwords were hashed, it is suggested that any accounts where the XG credentials may have been reused have their passwords updated.



