Blackcat/ALPHV ransomware breaches 60+ organizations
Introduction
BlackCat is the first ransomware group to successfully breach organizations using RUST, which is considered to be a more secure programming language that offers improved performance and reliable concurrent processing.
As of March 2022, BlackCat/ALPHV ransomware as a service (RaaS) has compromised at least 60 entities worldwide, according to a new report by the Federal Bureau of Investigation (FBI), which details showing indicators of compromise (IOCs) associated with attacks involving BlackCat/ALPHV.
How It Works?
In addition, BlackCat/ALPHV ransomware leverages previously compromised user credentials to gain initial access to the victim system. According to the FBI, once the malware establishes access, it compromises Active Directory user and administrator accounts. The malware uses Windows Task Scheduler to configure malicious Group Policy Objects (GPOs) to deploy ransomware. Initial malware deployment leverages PowerShell scripts, in conjunction with Cobalt Strike, and disables security features within the victim’s network. BlackCat/ALPHV ransomware also leverages Windows administrative tools and Microsoft Sysinternals tools during compromise; steals victim data prior to the execution of the ransomware, including from cloud providers where company or client data was stored; and, leverages Windows scripting to deploy ransomware and to compromise additional hosts.
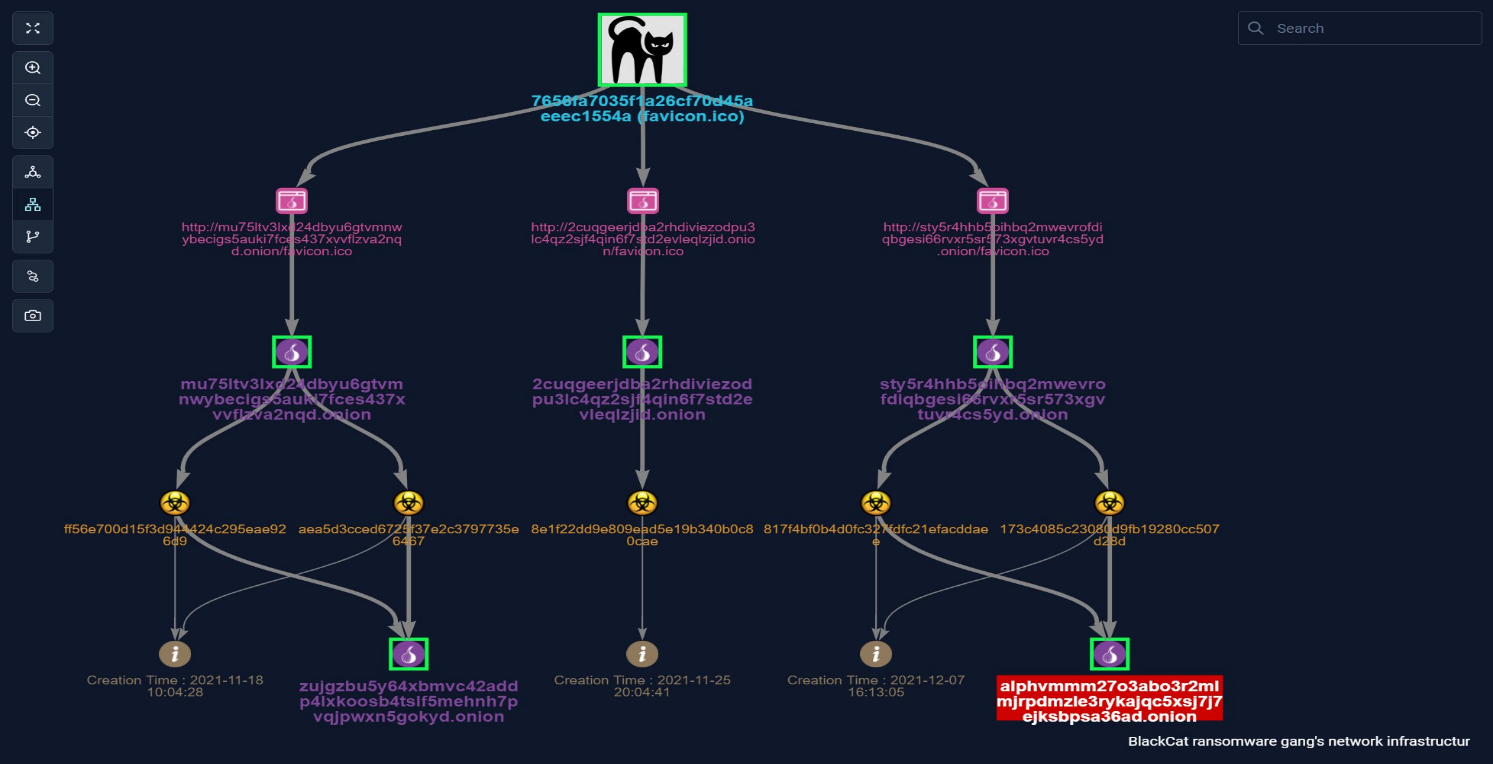
Black-Cat affiliated threat groups typically request ransom payments of several million dollars in Bitcoin and Monero but have accepted ransom payments below the initial ransom demand amount. Many of the developers and money launderers for BlackCat/ALPHV are linked to Darkside/Blackmatter, indicating they have extensive networks and experience with ransomware operations.
Recommended Mitigations
- Review domain controllers, servers, workstations, and active directories for new or unrecognized user accounts.
- Regularly back up data, air gap, and password-protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (e.g., hard drive, storage device, the cloud).
- Use multi-factor authentication where possible.
- Update the rules for the security systems that are implemented in the organization.



