New Fileless Malware uses Windows Event Logs for Hiding Shellcode
Researchers have spotted a malevolent campaign that uses a previously unseen approach to silently install fileless malware on target PCs.
The method includes directly inserting shellcode into Windows event logs. According to a Kaspersky research paper issued on Wednesday (4/May/2022), this allows attackers to utilize Windows event logs as a cover for dangerous late stage trojans.
The effort was unveiled in February by researchers, who believe the anonymous foes have been operating since last month.
Denis Legezo, senior security researcher at Kaspersky’s Global Research and Analysis Team stated that the most unique component of this operation, was the event logs method, which no one has seen before.
To distribute the malware payload, the attackers behind the campaign employ a variety of injection tools and anti-detection techniques. “The actor behind this effort is highly capable,” Legezo noted, “with at least two commercial products in use, as well as numerous types of last-stage RAT and anti-detection wrappers.”
HIDING THE MALWARE IN PLAINSIGHT (EVENT LOGS)
The attacker drives targets to a genuine website and entices them to download a compressed .RAR file decoyed with the network penetration testing tools Cobalt Strike and SilentBreak. Both are popular tools used by hackers for delivering the shellcode to target PCs.
Cobalt Strike and SilentBreak use independent anti-detection AES decryptors that are built with Visual Studio.
The Cobalt Strike module’s digital certificate differs. “15 distinct stagers from wrappers to final stagers were signed,” according to Kaspersky.
Following that, attackers may leverage Cobalt Strike and SilentBreak to “implant code into any process” and inject plug-ins into Windows system processes or trustworthy apps like DLP. This layer of infection chain decrypts, maps into memory and finally launches the code.
It is classified as fileless because of its capacity to inject malware into the system’s memory. Fileless malware, as the name implies, infects targeted systems without leaving any traces on the local hard drive, making it simple to avoid standard signature-based security and forensics technologies. The approach of hiding attackers’ operations in a computer’s random-access memory and using native Windows capabilities like as PowerShell and Windows Management Instrumentation (WMI) is not new.
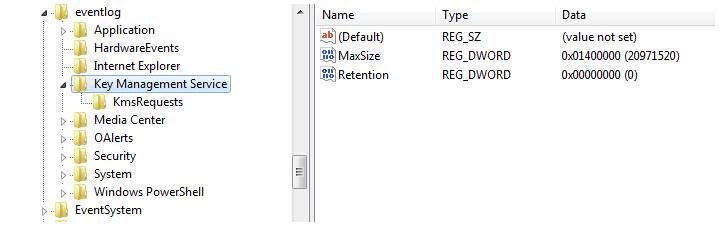
The unseen thing behind this attack is how the encrypted shellcode with the malicious payload is inserted in Windows event logs. The code is “split into 8 KB chunks and stored in the binary component of event logs” to prevent discovery.
“The dropper places the launcher on disc for side-loading, and publishes information messages containing shellcode into the current Windows KMS event log,” Legezo explained.
“The dropped wer.dll is a loader and would do no harm if the shellcode wasn’t buried in Windows event logs,” “The dropper scans the event logs for entries with the category 0x4142 (“AB” in ASCII) and the Key Management Service as a source.” If none are detected, 8KB chunks of shellcode are inserted into information logging messages using the ReportEvent() Windows API method (lpRawData argument).”
Following that, a launcher is placed in the Windows Tasks directory. “At the entrance point, a separate thread assembles all of the above mentioned 8KB parts into a full shellcode and executes it,” said the researcher.
“Such attention to the campaign’s event logs isn’t restricted to saving shellcodes. Dropper modules additionally modify native Windows API functions linked to event tracing (ETW) and anti-malware scan interface (AMSI) to make the infection process more discreet,” the researchers added.
Recommendation against Fileless Attacks:
An integrated strategy that tackles the whole threat lifecycle is critical to successfully countering fileless threats. One can have an edge over attackers by being able to analyze every aspect of a campaign before, during, and after an attack if they have a multi-layered defense.
Two things are extremely critical:
- The potential to view and quantify what is happening, including understanding the attack’s tactics, monitoring activity in PowerShell or other scripting engines, getting aggregated threat data, and gaining visibility into user activities.
- The capacity to manipulate the state of the targeted system, including the ability to interrupt arbitrary operations, remediate processes involved in the attack, and isolate affected devices.
Other practices that can be followed to defend organizations against fileless malware threats are as follows:
- Ensuring strong organizational security hygiene –
- Make sure your windows computers are patched and up to date.
- Conduct regular security awareness training sessions to create awareness among employees regarding dangers of email attachments and clicking on suspicious links.
- Understand the behavior of built-in windows code so you can spot any anomalies if present.
- Clearly defining access rights and privileges – to prevent the privilege escalation attacks (after the malware has entered any host on the network), proper network segmentation should be implemented and clear understanding of access rights, especially for third-party applications and users.
- Using strong and latest anti-virus is always a good option.



