BIG-IP iControl REST Vulnerability Alerted by F5
F5, a multi-cloud security and application delivery firm, discovered 43 security flaws in its BIG-IP, NGNIX Service Mesh, F5OS-A, and Traffix SDC products. One common vulnerability and exposure (CVE) was rated Critical, 17 were rated High, 24 were rated Medium, and one was rated Low in the security warning released on Wednesday, May 4, 2022.
CVE-2022-1388, the most serious vulnerability, involves circumventing iControl REST authentication. The flaw “may permit an unauthorised adversary with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands, create or remove files, or stop services,” according to F5.
This vulnerability basically allows an attacker with management interface pretend to be an administrator due an implementation flaw in authentication, once you have the admin privileges, you can communicate with all the application endpoints, including the execute codes.
CVE-2022-1388, if exploited, can result in a complete system takeover. As a result, it received a CVSS score of 9.8 out of 10. The Common Vulnerability Scoring System (CVSS) is a framework for determining the severity of software vulnerabilities.
The figure below displays the affected BIG-IP versions, along with the patches that were introduced for the iControl REST authentication bypass flaw.
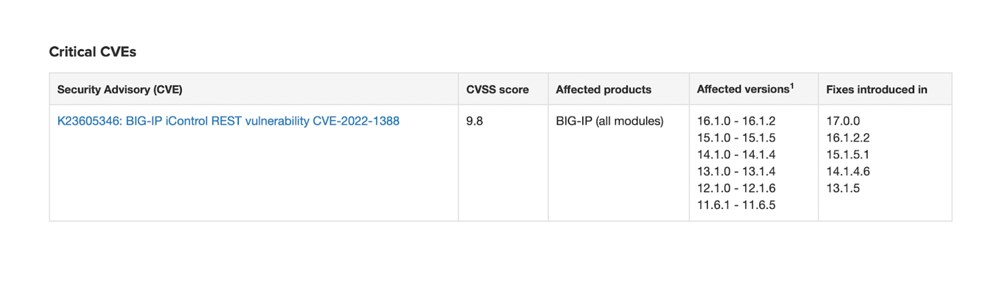
This issue affects just BIG-IP and does not affect BIG-IQ Centralized Management, F5OS-A, F5OS-C, or Traffic SDC. The table below shows which patches are associated with which affected versions.
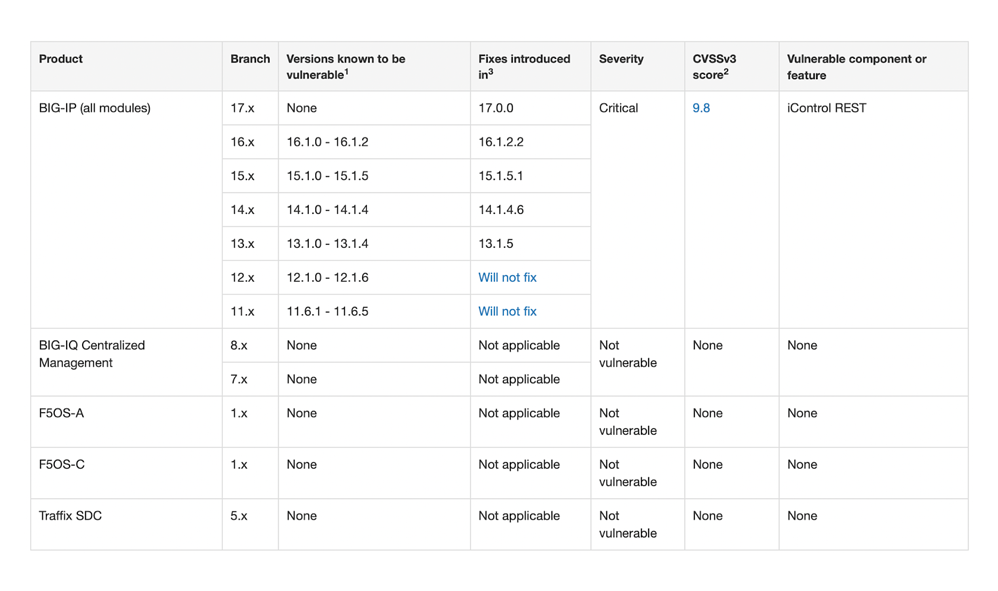
Recommended Actions:
According to F5, if you are operating a version that is listed in the Versions known to be susceptible column, you can eradicate this vulnerability by installing a version from the Fixes introduced in column. If the Fixes introduced in column does not include a version for your branch, there is presently no update candidate for that branch, and F5 suggests updating to a version that has the patch.
Mitigations:
If there is no accessible repair for your branch’s version, F5 has suggested the following solutions as temporary mitigations. Following strategies should limit access to iControl REST to only authorized networks or devices, minimizing the attack surface:
- Block iControl REST access through the self IP address
All access to the iControl REST interface of BIG-IP system can be blocked through self IP addresses. To do so, change the Port Lockdown setting to Allow None for each self IP address in the system.
- Block iControl REST access through the management interface
To mitigate this vulnerability for affected F5 products, restrict the management access only to trusted users and devices over a secure network.
- Modify the BIG-IP httpd configuration
To mitigate this issue, alter the BIG-IP httpd settings in addition to limiting access via the self IP addresses and administration interface, or as an alternative to preventing access if those options are not available in the particular environment.



