All you need to know about H0lyGh0st Ransomware
Since June 2021, a new ransomware strain has been affecting small- to medium-sized enterprises worldwide, according to Microsoft Threat Intelligence Center (MSTIC). The malware, known as H0lyGh0st, was initially created by a newly discovered North Korean APT that was identified as DEV-0530. Targeting industries including industry, education, financial services, and technology, ransomware assaults have a clear financial motivation.
Analysis of DEV-0530 activities uncovers connections to Plutonium (also known as Andariel), a functioning subunit of the Lazarus umbrella and another threat actor supported by North Korea. Security experts notice that the clusters are actively communicating with one another and using shared malicious tools to carry out the attacks.
H0lyGh0st Description
H0lyGh0st ransomware is a relatively recent strain created by the developing DEV-0530 APT supported by the North Korean government. Threat actors target arbitrary small and medium-sized businesses worldwide with the malware for financially driven attacks in an effort to smuggle money into their nation.
Since September 2021, there have been consistent attacks. Threat actors use unpatched vulnerabilities (like CVE-2022-26352) in customer-facing online applications and CMSs to distribute the H0lyGh0st ransomware. Then, using H0lyGh0st and the.h0lyenc extension, all files on the specified instance are encrypted. The victim also receives a sample of the files used to prove the attack along with the ransom note. Cyber attackers commonly request Bitcoin payments between 1.2 and 5 BTC.
Researchers found text attached to a ransom note that they received in which attackers claim they want to “bridge the gap between the rich and poor,” indicating that H0lyGh0st’s ransomware campaigns are financially driven, they added. They also make an effort to justify their acts by claiming to raise victim security awareness by educating the victims about their security posture.
According to MSTIC, DEV-0530 also has ties to another North Korean-based group known as PLUTONIUM, commonly referred to as DarkSeoul or Andariel, and researchers have been able to observe conversations between the two groups. They claimed that H0lyGh0st has also been observed using only PLUTONIUM-made tools.
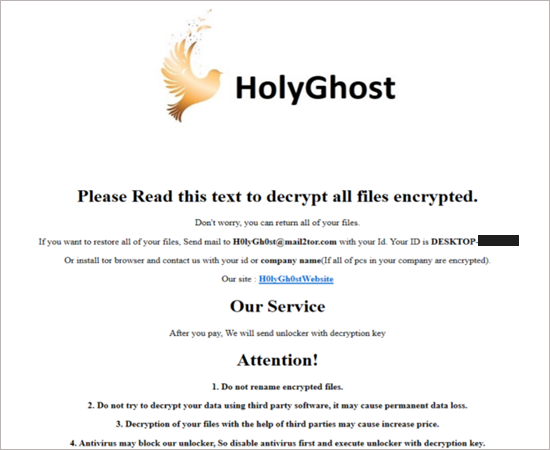
A H0lyGh0st ransom note linked to attacker’s onion site.
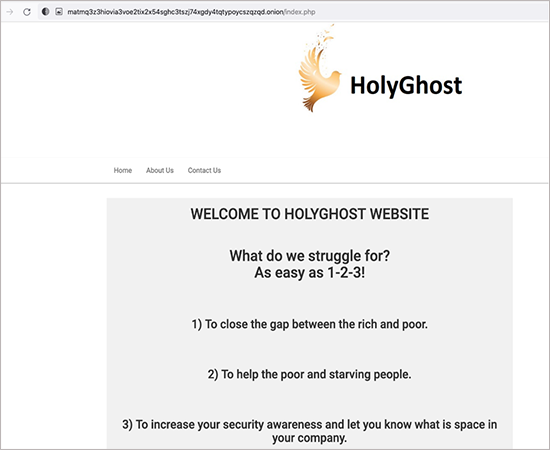
DEV-0530 attackers publishing their claims on their website.
In contrast to the Go-based versions, SiennaPurple (BTLC C.exe) was an early version of Holy Ghost ransomware and lacked a number of critical capabilities.
Microsoft refers to the more recent versions as SiennaBlue.
- exe
- exe
- exe
Additionally, throughout time, the following features were added to their functionality and are now part of their present version: –
- Multiple encryption options
- String obfuscation
- Public key management
- Internet support
- Intranet support
Remediation Actions
- As part of broader security against ransomware and extortion threats, it is important that all organisations proactively create and regularly validate a data backup and recovery plan.
- Building credentials hygiene.
- Credential exposure auditing
- Prioritizing deployment of Active Directory updates
- Cloud hardening
- Use basic best practises and the Azure Security Benchmark to secure identity infrastructure.
- Make sure that the cloud admins and tenant admins are treated with the same level of security and credential hygiene.
- Address gaps in authentication coverage.
- Ensure that MFA is enforced on every account you have.
- Using password less authentication methods to enable the user to log in without a password.
- Ensure that legacy authentication is disabled.



