CUBA RANSOMWARE ATTACKS
A novel remote access Trojan named ROMCOM RAT on infected computers is one of the previously undocumented tactics, methods, and procedures (TTPs) that threat actors connected to the Cuba ransomware have been tied to.
The latest information was discovered by Palo Alto Networks’ Unit 42 threat intelligence team, which is monitoring the double extortion ransomware group known as Tropical Scorpius, which is themed after a constellation.
Cuba ransomware, also known as COLDDRAW, was discovered for the first time in December 2019 and reappeared on the threat environment in November 2021. It has been linked to attacks against 60 targets across five vital infrastructure sectors, resulting in at least $43.9 million in ransom payments.
40 of the victims listed on its data leak site are in the United States, indicating that its target organizations are not as widely dispersed as those of other ransomware gangs.
“Cuba ransomware is distributed through Hancitor malware, a loader known for dropping or executing stealers, such as Remote Access Trojans (RATs) and other types of ransomware, onto victims’ networks,” according to a December 2021 alert from the U.S. Federal Bureau of Investigation (FBI).
WHAT IS SOLIDBIT RANSOMWARE?
By disguising itself as several applications including the League of Legends account checker, Social Hacker, and Instagram Follower Bot, SolidBit stands out for its targeting of users of prominent video games and social networking sites and enabling the actors to cast a large net of prospective victims.
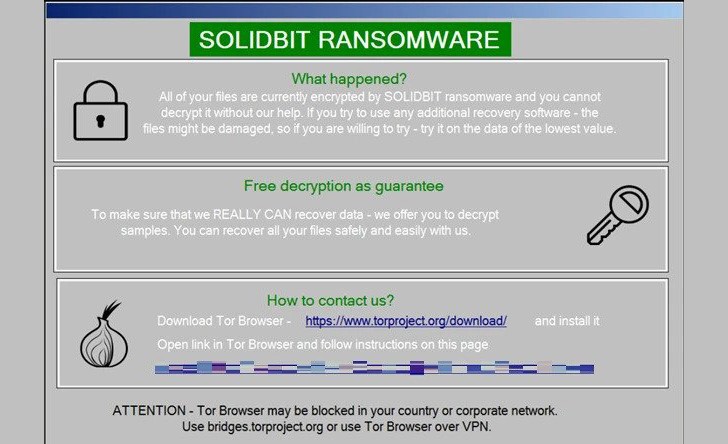
In a report published last week, Trend Micro revealed that SolidBit ransomware is actually a variation of the Chaos ransomware known as Yashma.
It’s conceivable that the ransomware perpetrators behind SolidBit are now collaborating with the creator of the Yashma ransomware and have probably tweaked several Chaos builder features before renaming them as SolidBit.
For its part, BlueSky is known to use anti-analysis techniques to mask its appearance and multithreading to encrypt data on the host for speedier encryption.
The ransomware payload also poses as a genuine Windows application when it begins by executing a PowerShell script that was received from an attacker-controlled server (“javaw.exe”).
REMEDIATION
- Make a thorough backup of your data – You should back up your company’s data on a regular basis. If something goes wrong, you should be able to quickly and easily restore a recent backup. If your company is ever attacked, however, the repercussions will be significantly less severe.
- Keep software up to date – Ransomware attackers can occasionally obtain access to the software by exploiting weaknesses. Adopt a patch management strategy and ensure that everyone on your team is up to date at all times.
- Improve threat detection – Most ransomware attacks can be found and resolved before it’s too late. To maximize your chances of being protected, install an autonomous threat detection system.
- Multi-factor authentication should be utilized – multi-factor authentication requires users to authenticate their identities in a variety of ways before being permitted access to a system. If a criminal acquires a password from an employee, the attacker will be unable to gain easy access to the systems.
- Employ the principle of least privilege: Employees should never have more data access than they require. Segmenting the firm and restricting access can act as a quarantine, limiting access vectors and decreasing the impact of a potential assault.
- Examine and track email and file activity – When using phishing techniques, cybercriminals typically use emails as their primary mode of communication. Scans and monitor emails on a regular basis, and consider adopting an automated email security solution to keep potentially harmful communications from reaching users. Think about scanning and tracking the file activity as well.
- Increase employee training – The bulk of ransomware attacks are the consequence of irresponsible or negligent employee behavior. On their own initiative, someone may give out their password or download unwelcomed material.
- Don’t pay the ransom – If your organization has been hit by ransomware, don’t pay the ransom. Getting out of this terrible situation as soon as feasible may seem desirable. Even yet, there’s no certainty that the assailant will follow through on his threats.
- Anti-ransomware software be utilized – To achieve its purpose, ransomware must engage in atypical behaviors such as opening and encrypting large numbers of files. To fight against ransomware that “slips through the cracks,” a specialized security solution is necessary.



