OPTUS DATA BREACH – EXPOSED CUSTOMER DATA
The follow-up post from an anonymous account claiming responsibility for the Optus hack, in which it apologized for the attack. (Supplied)
Introduction:
On September 22, 2022, Optus, a wholly owned subsidiary of Singtel and the second largest wireless carrier in Australia, announced that it was the victim of a cyberattack that resulted in the data breach of approximately 10 million users. The next day, on September 23, 2022, a hacker posted a tiny sample of the stolen data on a Breached Hacking site demanding $1,000,000 (USD) in ransom money from the company. Although Optus has not yet revealed how many users may have been affected by the breach. It has stated that unauthorized access might have exposed their names, dates of birth, phone numbers, email addresses, and, for a subset of consumers, addresses and ID document numbers such as driver’s licenses or passport numbers.
Attack Process:
Optus described the attack as a sophisticated attack. The company has not yet acknowledged how the data is acquired. But as per the reports, the attack has been implemented using the company’s web API (Application Programming Interface), which does not have proper access controls for protecting the customers’ data. Without technical restrictions in place for authentication and authorization, any user might have requested information from any other user. The attacker most likely automated the operation to capture millions of instances of personally identifiable information from the endpoint.
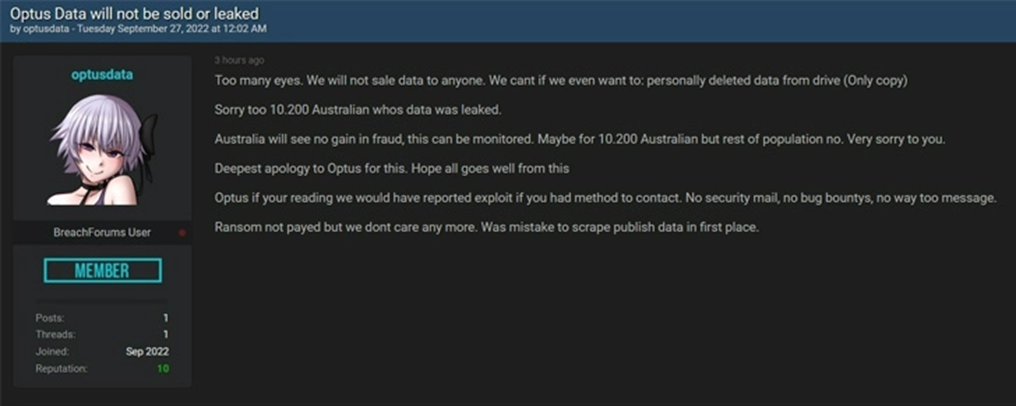
The attacker has gathered 10,200 customers’ data and demanded the company a crypto ransom of 1 million USD. But Optus refused to pay the demanded ransom. After failing to receive a ransom demand, the threat actor made a larger sample of stolen data of customers available on the same hacker forum for free. The company has cooperated with Australian Federal Police to investigate the situation. The Australian Federal Police (AFP) has announced the commencement of “Operation Hurricane” to identify the threat actors responsible for the breach and extortion demands. The AFP also stated that they were aware of stories of stolen data getting sold on the dark web and started monitoring it with specialist capabilities. On September 27, 2022, the attacker apologized on the same hacker forum and stated that he would delete the leaked data from the drive. Reports presumed that the amount of attention the incident received, the involvement of the AFP, and remarks from high-level politicians, frightened the attacker back down.
Impact:
The cyber-attack resulted in the data breach of approximately 10 million customers. The data breach could have exposed the Customers’ names, dates of birth, phone numbers, email addresses, and, for a subset of customer addresses, ID document numbers such as driver’s licenses or passport numbers. The attacker did not access Payment information and account passwords. Optus services, such as mobile and home internet, texts, and voice calling, are not affected by the attack.
Remediation:
- Optus began investigating possible unauthorized access to current and past customers’ information following the cyber-attack
- The company has collaborated with the Australian Cyber Security Centre to reduce any threats to customers. It has also contacted the Australian Federal Police, the Australian Information Commissioner, and other relevant regulators.
- Optus contacted its customers to notify them about the impact of the cyber-attack, if any, on their personal information. They also informed customers about the safeguards that had no effect in the past.
- Optus started providing free 12-month subscriptions to Equifax Protect to the most affected current and past customers whose information was exposed because of a breach. Equifax Protect is a credit monitoring and identity theft prevention service. There was no compromise of passwords or financial information.
- Optus recommended the users follow several precautions to protect their online identity:
- Old passwords have to be updated.
- Turn on two-factor authentication.
- Maintain vigilance over internet accounts, looking for odd activities.
- Be more cautious about SMS and email scams.
- Never click links in emails or SMS communications; instead, search the corporate website manually.



