Critical OAuth Vulnerability (CVE-2023-28131) in Expo Platform
A critical vulnerability has been found in the implementation of the Open Authorization (OAuth) standard, which is widely used by websites and applications to connect with popular platforms like Facebook, Google, Apple, and Twitter. This vulnerability poses significant risks, including unauthorized access to user accounts, potential leakage of sensitive information, and even the possibility of financial fraud.
OAuth is a key component when users log in to a website and choose to authenticate using another social media account, such as “Log in with Facebook” or “Log in with Google.” This feature, widely employed for cross-platform authentication, has become a standard practice on many websites. However, a team from Salt Security’s Salt Labs, an API security firm, has recently discovered a flaw in the OAuth implementation within Expo. Expo is an open-source framework used for developing native mobile apps across various platforms like iOS, Android, and the Web, all from a single codebase. This flaw has been identified as CVE-2023-28131 and poses significant risks to the security and integrity of user accounts and sensitive data.
What is OAuth?
OAuth is an open standard protocol that ensures secure authorization, providing users with a standardized approach to grant access to their web service resources without divulging login information. Its primary application lies in facilitating users’ access to their data on social media platforms and other web services.
The Expo Framework:
JavaScript and react can be used to create native mobile applications using the open-source Expo framework. It offers a development environment that makes it easier to create, test, and release mobile applications across various platforms, including iOS, Android, and the web.
Developers who want to quickly prototype, build, and test mobile applications using well-known web technologies like JavaScript and React will find Expo to be especially helpful. It streamlines the workflow for creating cross-platform apps, lessens the need for platform-specific code, and streamlines the development process.
Understanding of Exploit:
Salt Labs, a security team affiliated with API security company Salt Security, recently discovered a vulnerability (CVE-2023-28131) within Expo’s implementation of the OAuth protocol. This vulnerability has been rated with a severity score of 9.6 on the CVSS scoring system.
Following a comprehensive investigation, Salt Labs determined that services utilizing the Expo framework are exposed to potential credential leakage. This flaw poses significant risks, including the potential for a complete account takeover, leading to identity theft, financial fraud, and unauthorized access to sensitive credit card details.
Under specific circumstances, this vulnerability even enables malicious individuals to impersonate compromised users on prominent platforms such as Facebook, Google, and Twitter, allowing them to perform actions on behalf of the affected users.

The vulnerability is rooted in a weakness within the storage of callback URLs within the auth.expo.io service. Exploiting this weakness involves manipulating users into clicking on malicious links, inadvertently revealing their third-party authentication credentials, and providing unauthorized access to their accounts.
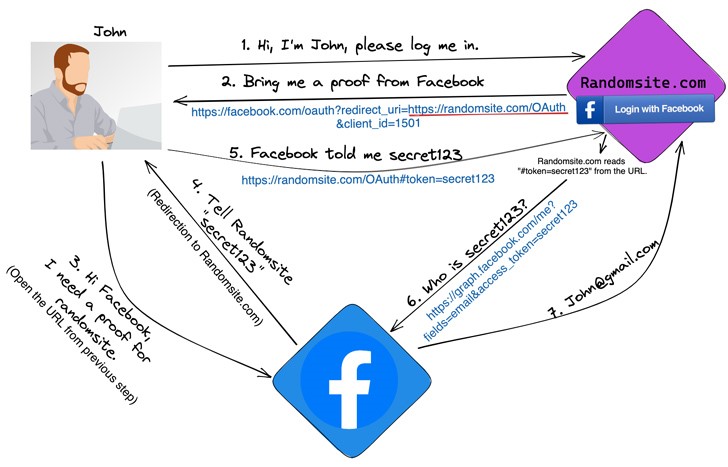
In the context of Site X, when users click on OAuth-enabled links to log in using their social media accounts, a fresh window opens, redirecting them to trusted authentication providers such as Facebook or Google. During the initial visit to Site X, the social media platform requests the user’s consent to share information with Site X. If the user has previously completed this process, Site X receives automatic authentication from the respective social media platform.
Researchers discovered several potentially affected services, including platforms like Codecademy, Booking.com, and Kayak.com. They demonstrated how the exploit could be used to gain control of user accounts.
CVE-2023-28131 Impact:
The security gaps identified made services using this framework susceptible to credentials leakage, allowing:
- Full account takeover, leading to identity theft, financial fraud, access to credit cards and more.
- In certain cases, it also allows a malicious actor to perform actions on behalf of a compromised user in Facebook, Google, Twitter, and other online platforms.
Remediation:
- Expo swiftly addressed the vulnerability by deploying a hotfix and advises customers to update their deployment, eliminating the risk associated with the vulnerable service.
- Developers are recommended to migrate to using deep links with third-party authentication providers directly, using the AUTH Session module’s use Proxy options. This migration enhances security, enables Single Sign-On (SSO) features, and ensures a reliable authentication process.
- To prevent unauthorized access, organizations should prioritize the implementation of Role based access control & multi-factor authentication alongside OAuth. This additional layer of security effectively mitigates the risk, even if the CVE-2023-28131 vulnerability is exploited.
- It is crucial to carefully evaluate the technology and application type when implementing OAuth. Client-side applications should undergo thorough scrutiny, while server-side applications have inherent advantages that minimize vulnerabilities and information disclosure.
- Organizations should review and update their OAuth implementation to ensure it aligns with the latest security best practices. This involves incorporating secure coding practices, implementing proper access controls, and regularly monitoring and auditing OAuth configurations.
- By combining a comprehensive understanding of the technology, consideration of the application type, and the integration of appropriate security measures, organizations can establish a robust and secure OAuth implementation.



