Cookie Consent Plugin Bug Exposes 1.5 million WordPress Sites to Hacker Attacks
In recent times, the cyber security landscape has been marred by a series of targeted attacks aimed at exploiting a vulnerability within a widely used WordPress cookie consent plugin called Beautiful Cookie Consent Banner. With over 40,000 downloads recorded as of May 2023, this plugin has unwittingly become a target for malicious actors seeking to exploit its weaknesses.
The method employed by these attackers is known as Cross-Site Scripting (XSS), a technique that allows them to inject and execute JavaScript code within the visitors’ web browsers. By leveraging this vulnerability, hackers can run JavaScript scripts with malicious intent, potentially compromising the security and privacy of unsuspecting website visitors.
Given that JavaScript is a fundamental component used by countless websites to create dynamic and interactive webpages, the implications of this flaw are far-reaching and highly concerning. It underscores the urgency to address this risk promptly and robustly, in order to safeguard the integrity of online experiences for both website owners and their visitors.
Recognizing the gravity of the situation, concerted efforts are being made to prevent this vulnerability from being further exploited. By identifying and rectifying the underlying weaknesses within the Beautiful Cookie Consent Banner plugin, developers and security experts aim to mitigate the risks posed by this particular XSS exploit.
Affected Software
A plugin that goes by the name of Beautiful Cookie Consent was exploited in over 1.5 Million WordPress websites. This was exploited to such an extent that even a failed attack could corrupt the plugin configuration stored in nsc_bar_bannersettings_json option.
The Plugin patch versions have been updated and all users were advised to update the patch versions to the latest ones to avoid any attacks or exploits. The issue for this website may have been solved but this issue looms large for many other websites which are exposed to this vulnerability.
Nearly 3 million attacks on more than 1.5 million sites ranging from across 14000 IP Addresses were recorded as of May 23, 2023. This number huge especially when considering that all of this just exploits one vulnerability.
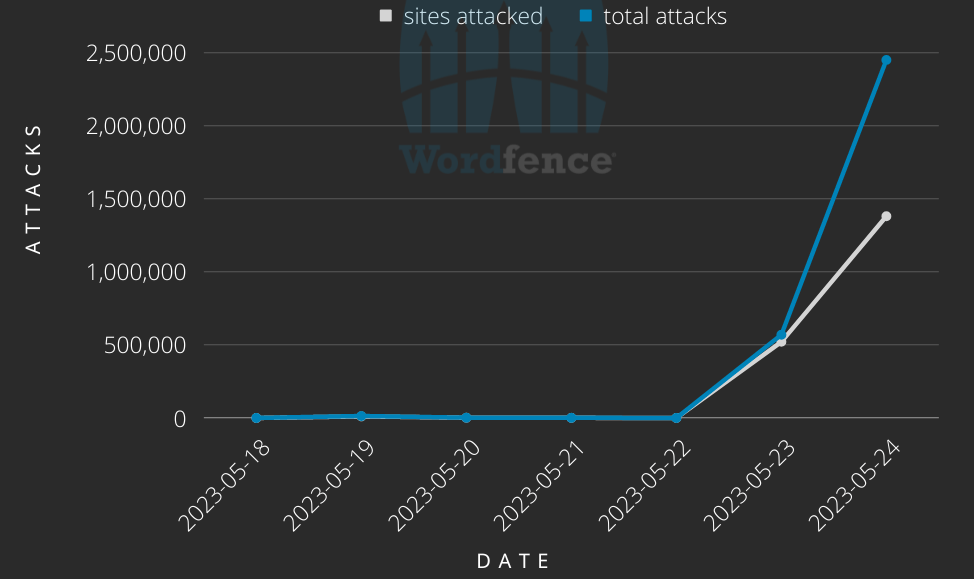
The above graph gives an idea of how many attacks have taken place recently.
Root Cause Analysis
Unauthenticated users are able to create admin accounts on WordPress websites using outdated plugin versions, according to WordPress startup Defiant, which discovered the assaults first.
This vulnerability has been on the attack since February 2023, the latest one being in May 2023.
The threat actor used a misconfigured exploit that doesn’t deploy a payload when targeting a WordPress website. The primary method used was exploiting Unauthenticated Stored Cross-Site Scripting (XSS) vulnerability. This includes injecting a JavaScript code snippet into the website.
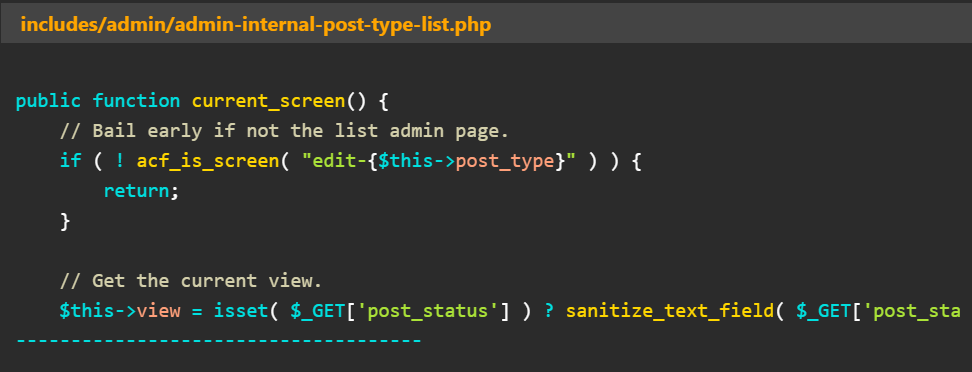
This vulnerability (CVE-2023-30777) results from the ‘admin_body_class’ function handler. At the same time, this handler did not adequately sanitize the output value of a hook that manages the CSS classes.
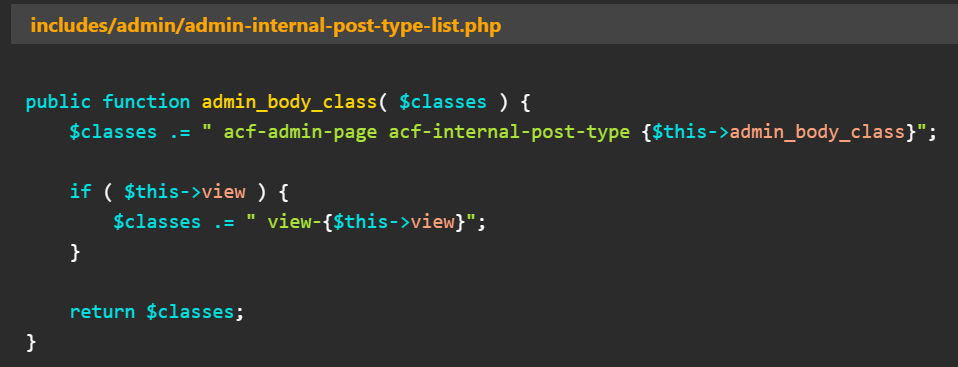
Within the plugin’s code, there exists an unsafe usage of a direct code sequence variable (‘$this->view’), which can be exploited by an attacker. This vulnerability allows malicious actors to inject harmful code, such as DOM XSS payloads, into the segments that are ultimately passed to a class string.
Possible Impact
The impact can include:
- Unauthorized access to private data. This could lead to consequences like the disclosure of thousands of Terabytes of user personal data.
- An unauthorized person intercepts and seizes control of a user’s active session on a computer network in a security attack known as session hijacking, often referred to as session stealing or session side jacking. By doing this, the attacker is able to access the user’s account without authorization, giving them the chance to carry out nefarious actions or obtain sensitive data.
- Malware infections happen when malicious software (malware) compromises a computer, device, or network. Malware is intended to interfere with, harm, or allow unauthorized access to computers and data.
Remediation
A number of steps can be taken to avoid this XSS vulnerability. These methods are being adopted by if you have identified a mass exploit targeting WordPress sites through a specific plugin, such as the Cookie Consent plugin, it’s important to take immediate action to mitigate the security risk. Here are some steps you can take to address the situation:
- Disable and remove the affected plugin: Disable and remove the Cookie Consent plugin from all affected WordPress sites. This will prevent further exploitation through the plugin vulnerabilities.
- Update WordPress and plugins: Ensure that your WordPress core installation and all other plugins are up to date with the latest security patches. This helps protect against known vulnerabilities and reduces the risk of future exploits.
- Scan for malware and malicious code: Conduct a thorough scan of your WordPress sites to detect any malware or malicious code that may have been injected as a result of the exploit. Use reputable security scanning tools or plugins to assist in this process.
- Clean up compromised sites: If any of your WordPress sites have been compromised, it’s essential to clean them up. Remove any malicious files, restore from a clean backup (if available), or consult with a security professional to perform a comprehensive cleanup.
- Reset user credentials: Change the passwords for all user accounts associated with the compromised WordPress sites. This includes administrators, editors, authors, and other user roles. Encourage users to choose strong, unique passwords to enhance security.
- Implement a web application firewall (WAF): Deploy a web application firewall, either as a plugin or at the network level, to provide an additional layer of protection against known attack patterns and malicious requests. A WAF can help detect and block malicious traffic targeting your WordPress sites.
- Enhance security measures: Review and strengthen your overall security measures for WordPress sites. This includes implementing secure user authentication, using strong passwords, restricting file permissions, enabling two-factor authentication, and regularly backing up your sites.
- Stay informed: Monitor security advisories and updates from reliable sources to stay informed about emerging threats and vulnerabilities affecting WordPress and its plugins. Promptly apply patches and security updates as they become available.



