North Korean APT37 Exploits New FadeStealer Malware
RedEyes Group Deploys New Malware for Wiretapping and Information Theft.
The hacker collective APT37, also known as StarCruft, Reaper, or RedEyes, has used a brand-new piece of malware named FadeStealer to steal data. The ‘wiretapping’ component of this sophisticated malware allows the threat actors to listen in on and record conversations through the microphones of the victims.
About the Threat Group:
It is generally accepted that APT37 is a state-sponsored hacker organisation working in collaboration with North Korean objectives. Their primary targets are North Korean defectors, educational institutions, and organisations situated in the European Union. They have a long history of carrying out cyber espionage activities.
Previously, APT37 used specialised malware called Dolphin and M2RAT to carry out commands and collect information from Windows machines, including connected mobile phones, including data, credentials, and screenshots.
The group’s most recent strategies are described in a recent report from the AhnLab Security Emergency Response Centre (ASEC). Researchers have discovered new, specifically designed malware used by APT37 in their espionage operations, including the “AblyGo backdoor” and “FadeStealer.”
The Process:
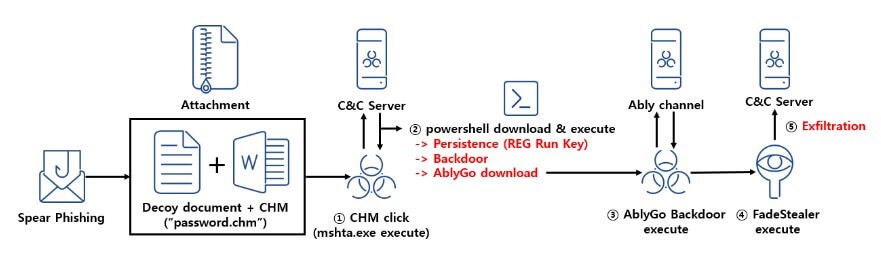
APT37 uses phishing emails that include password-protected Word and Hangul Word Processor documents (.docx and.hwp files), together with a Windows CHM file called “password.chm” that serves as an archive, to spread the virus. The phishing email instructs the recipient to open the CHM file in order to view the documents’ password, which starts the infection process.
The user is given the alleged password to unlock the file when they open a CHM file. A remote PowerShell script is secretly downloaded at the same time and run, operating as a backdoor on the Windows system with autostart registration.
The PowerShell backdoor then establishes contact with the attackers’ command and control servers and begins to carry out their instructions. Furthermore, it allows for the subsequent stages of the attack to introduce a second GoLang backdoor. Due to its use of the Ably Platform, an API service that enables developers to include real-time features and information delivery into their apps, this secondary backdoor is known as the “AblyGo backdoor.”
The final payload, the malware called “FadeStealer,” is delivered by the deployed backdoors. After being installed, FadeStealer uses DLL sideloading to insert itself into Internet Explorer’s legitimate ‘ieinstall.exe’ process. Every 30 minutes, it continues to collect data and store it in RAR archives, including screenshots, keystroke logs, files from connected smartphones and removable devices, and even audio recordings from the connected microphone. As a result, the threat actors can listen in on conversations. After gathering the data, it can be analysed to draw out sensitive data that the North Korean government can use.
APT37 is not the only North Korean threat actor using CHM files to spread malware, it is important to note. As reported by ASEC, Kimsuky, a state-sponsored hacking group, uses CHM files in phishing scams to spread malicious scripts that steal user data and set up additional malware.
Recommendations for zero trust architecture implementation:
Understand your environment: Begin by conducting a thorough assessment of your organization’s network infrastructure, applications, and data flow. Identify all assets, users, and their dependencies to gain a clear understanding of your environment.
Define your trust boundaries: Determine the trust boundaries within your organization’s network and define what level of access and privileges each user or system should have based on their role and the sensitivity of the resources they need to access.
Implement strict access controls: Implement granular access controls and least privilege principles to ensure that users and systems only have access to the specific resources they need to perform their tasks. Use techniques such as network segmentation, micro-segmentation, and role-based access controls (RBAC) to enforce access restrictions.
Use strong authentication mechanisms: Implement multi-factor authentication (MFA) to strengthen user authentication. This adds an extra layer of security by requiring users to provide additional proof of identity, such as a fingerprint or a one-time password, in addition to their username and password.
Monitor and log all activities: Implement robust logging and monitoring mechanisms to track user and system activities within your network. Use centralized logging solutions to collect and analyze logs for detecting any suspicious activities or potential security breaches.
Employ network segmentation: Divide your network into smaller segments or zones based on trust levels and apply strict access controls between these segments. This helps to contain potential breaches and limit lateral movement within your network.
Implement strong encryption: Encrypt sensitive data at rest and in transit using strong encryption algorithms. This ensures that even if data is intercepted or stolen, it remains unintelligible and unusable without the proper decryption keys.
XDR solutions (Extended Detection & Response)
XDR expands the capabilities of EDR solutions by integrating data from multiple security tools across different security layers, such as network traffic analysis, cloud environments, email gateways, and more. By aggregating and correlating data from various sources, XDR provides a holistic view of an organization’s security landscape. Key features of XDR solutions include:
Cross-layer visibility: XDR solutions collect and correlate data from various security tools and data sources, enabling security teams to detect and respond to threats that span multiple domains, such as endpoints, networks, and cloud environments.
Advanced analytics: XDR solutions leverage advanced analytics techniques, including machine learning and behavioral analysis, to identify complex threats and detect patterns that might go unnoticed by individual security tools.
Automated response and orchestration: XDR solutions often include automated response capabilities to execute predefined actions or trigger response workflows in response to detected threats. This helps in accelerating incident response and reducing manual effort.
Threat intelligence integration: XDR solutions integrate with external threat intelligence sources to enrich the analysis and provide context about known threats and indicators of compromise (IoCs).
EDR (Endpoint Detection and Response)
EDR solutions focus on monitoring and securing endpoints such as desktops, laptops, servers, and mobile devices. They provide real-time visibility into endpoint activities, including file and process monitoring, network traffic analysis, and behavioral analysis. Key features of EDR solutions include:
Threat detection: EDR solutions use various techniques like signature-based detection, behavior-based detection, and machine learning algorithms to identify potential threats and anomalies on endpoints.
Incident response: EDR solutions provide incident response capabilities, allowing security teams to investigate and respond to detected threats. They offer features like remote endpoint isolation, file quarantine, and threat remediation.
Endpoint visibility: EDR solutions offer detailed visibility into endpoint activities, including process execution, file modifications, network connections, and user behavior. This helps security teams understand the scope and impact of security incidents.
Forensic analysis: EDR solutions often include forensic capabilities to collect and analyze data from endpoints for investigation purposes. This can be helpful in understanding the root cause of an incident and gathering evidence.
Remediation:
Remediation from such malwares are:
- Disconnect from the network: As soon as you suspect a malware infection, disconnect the affected device from the network to prevent the malware from spreading or communicating with external servers.
- Identify and isolate the malware: Use an up-to-date antivirus or anti-malware program to scan your system and identify the malicious software. Quarantine or isolate the infected files to prevent further harm.
- Remove the malware: Once the malware has been identified, use the antivirus software to remove it from your system. Follow the instructions provided by the software to ensure a thorough removal.
- Update your operating system and software: Make sure your operating system, antivirus software, and other applications are up to date with the latest security patches. This helps protect your system from known vulnerabilities that malware might exploit.
- Change passwords: If there’s a possibility that the malware has obtained your passwords or sensitive information, change your passwords for all your online accounts, including email, social media, and banking.



