Hackers use new malware to breach air-gapped devices in Eastern Europe
Chinese state-sponsored hackers have been actively targeting industrial organizations with a sophisticated new malware capable of stealing data from air-gapped systems. These isolated systems are of paramount importance as they serve critical roles while remaining completely disconnected from both the enterprise network and the public internet.
Chinese attackers continue to refine their tactics, the need for heightened vigilance and innovative cybersecurity solutions becomes more urgent than ever before. Air-gapped systems typically fulfill critical roles and are isolated from the enterprise network and the public internet either physically or through software and network devices.
In the ever-evolving landscape of cybersecurity threats, researchers at the renowned cybersecurity company Threat Researchers have recently stumbled upon a malicious campaign orchestrated by the infamous cyber-espionage group, APT31, also known as Zirconium. Their latest discovery sheds light on the group’s sophisticated techniques and provides insights into their covert operations in Eastern Europe. Let’s delve into the fascinating world of cyber espionage and the enigmatic ‘FourteenHi’ malware family that lies at the heart of their sinister schemes.
Enter the ‘FourteenHi’ Malware Family:
Among the many malicious tools utilized by APT31, the most intriguing is the notorious ‘FourteenHi’ malware family. Acting as the group’s signature, this malicious software has been used in various campaigns, consistently leaving a trail of devastation in its wake. Its capabilities remain shrouded in mystery, as researchers work tirelessly to unravel its intricate code and understand its full potential.
Multi-stage attacks:
Security Researchers says that the attacks started in April last year and involved three separate stages. The implants in the initial-phase established persistence and remote access to the compromised systems and collected data useful for reconnaissance.
In the second stage, APT31 drops more specialized malware that can steal data from isolated (air-gapped) systems using USB propagation.
Finally, in the third stage of the attack, the hackers use implants that can upload the collected data to their command and control (C2) servers.
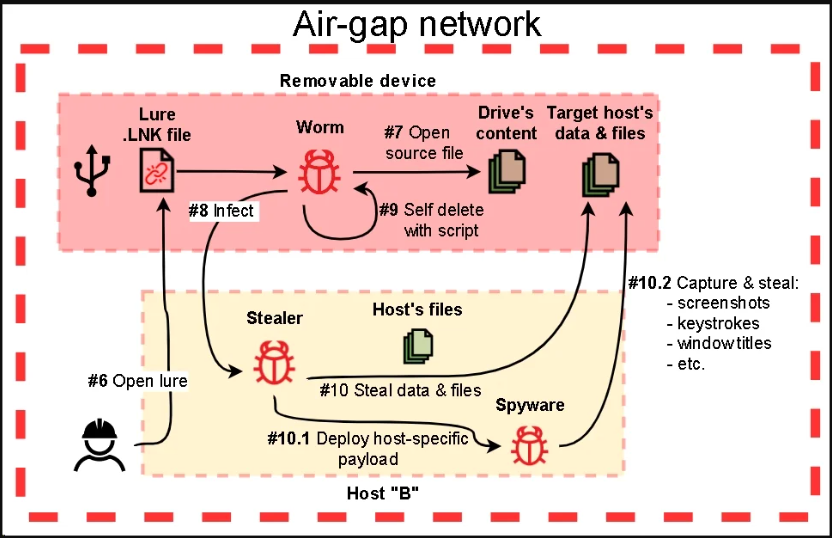
The malware that targets isolated systems consists of four modules described below:
- First module: Profiles removable drives connected to the system, collects files, captures screenshots and window titles, and drops additional payloads on the infected device.
- Second module: Infects removable drives by copying a legitimate McAfee executable which is vulnerable to DLL hijacking, and a malicious DLL payload onto the root directory of the device, and sets them as “hidden.” The tool also creates a lure LNK file that triggers the infection if the victim launches it.
- Third module: Executes a batch script to collect data from the device and save the output to the “$RECYCLE.BIN” folder, from where the first module will collect it.
- Fourth module: Variant of the first module seen in some attacks, acts as a payload dropper, keylogger, screenshot-capturing tool, and file stealer.
Threat Researchers noticed an additional implant used in the APT31 attacks, designed to collect local files from breached systems.
That implant decrypts and injects its payload into the memory of a legitimate process to evade malware detection, then sleeps for 10 minutes and eventually copies all files that match the file type extensions defined in its configuration.
The stolen files are archived using WinRAR (if not available, the malware exits) and then stored in temporary local folders created by the malware under “C:\ProgramData\NetWorks\.” Ultimately, the archives are exfiltrated to Dropbox.
Threat Researchers underlines that the attacks were stealthy and listed the following tactics, techniques, and procedures (TTPs): DLL order hijacking to load malicious payloads into memory and hide payloads in encrypted form in separate binary data files.
The company provides a technical report that includes additional data such as malware hashes, a full set of indicators of compromise, and details about the activity of the malware from start to finish.
Air-gapped systems are an attractive target for APT groups, who typically turn to USB drives to deliver malware and exfiltrate data from the isolated environment.
Remediations Action:
- Patch and Update: Keep software and systems up-to-date with the latest security patches to address known vulnerabilities.
- Network Segmentation: Implement robust network segmentation to isolate air-gapped systems and limit communication channels.
- Physical Security: Strengthen physical access controls and surveillance around air-gapped systems to prevent unauthorized entry.
- Zero Trust Architecture: Adopt a Zero Trust approach to continuously verify users and devices before granting access to critical resources, ensuring enhanced security for air-gapped systems and sensitive data.
- Adopt Multi-Factor Authentication (MFA): Enforce MFA for all users attempting to access critical systems, ensuring an additional layer of authentication beyond passwords.
- Utilize Least Privilege: Limit user privileges to only what is necessary for their roles. Apply the principle of least privilege to reduce the impact of potential breaches.
- Continuous Monitoring and Behavior Analysis: Implement advanced threat detection (EDR/XDR/MDR) solutions to continuously monitor network traffic and user behavior. Detect anomalies and potential threats in real-time.
- Embrace Strong Encryption: Encrypt data both in transit and at rest to ensure data integrity and confidentiality. Implement strong encryption protocols to protect sensitive information from unauthorized access.



