Decoy Dog: New Breed of Malware Posing Serious Threats to Enterprise Networks
A more thorough examination of the Decoy Dog virus, which was recently found, has shown that it is a major improvement over the Pupy RAT, the open-source remote access trojan.
The capacity to shift victims to another controller, enabling them to keep in touch with compromised PCs and stay undetected for extended periods of time, is one of Decoy Dog’s entire array of extraordinary, previously unheard-of capabilities.
In addition, the malware now has the ability to connect to emergency controllers and run arbitrary Java code on the client using a mechanism akin to the DNS domain generation algorithm (DGA), with the Decoy Dog domains designed to respond to replayed DNS requests from compromised clients.
The cybersecurity company first learned about the sophisticated toolset in early April 2023 after spotting suspicious DNS beaconing activity, which revealed its highly focused attacks on business networks.
Although the origins of Decoy Dog are still unknown, it is believed to be run by a few nation-state hackers that use different strategies but reply to inbound requests that follow the format of client communication.
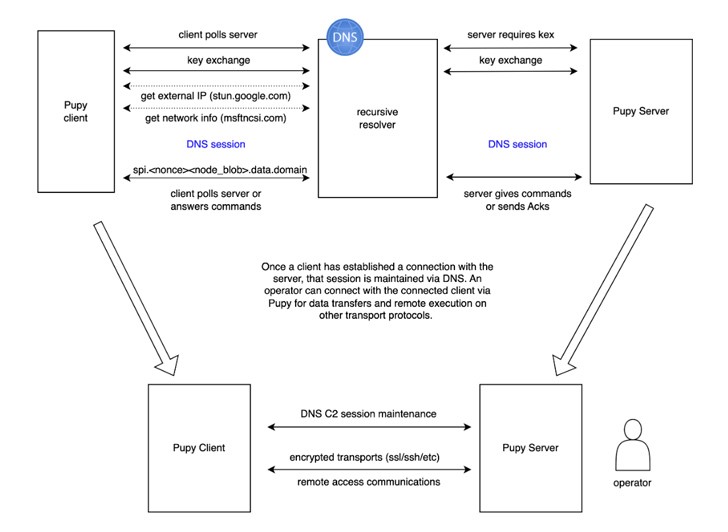
The domain name system (DNS) is utilized by Decoy Dog to carry out command-and-control (C2) operations. A malware-infected endpoint connects with and receives commands from a controller (a server) through DNS requests and IP address answers.
In reaction to the prior revelations, the threat actors behind the operation are reported to have quickly modified their assault infrastructure, knocking down some of the DNS nameservers and registering new replacement domains to achieve remote persistence.
Decoy Dog’s first deployment is known to have occurred in late March or early April 2022, and three other clusters were later found to be under the control of various operators. There are currently 21 Decoy Dog domains in existence.
Additionally, one group of controllers that have been registered from April 2023 have modified by implementing a geofencing technique to restrict replies to client IP addresses to certain places, with activity being restricted to Russia and Eastern Europe.
Remediations :
Remediations from such malwares are:
- Disconnect from the network: As soon as you suspect a malware infection, disconnect the affected device from the network to prevent the malware from spreading or communicating with external servers.
- Identify and isolate the malware: Use an up-to-date antivirus or anti-malware program to scan your system and identify the malicious software. Quarantine or isolate the infected files to prevent further harm.
- Remove the malware: Once the malware has been identified, use the antivirus software to remove it from your system. Follow the instructions provided by the software to ensure a thorough removal.
- Update your operating system and software: Make sure your operating system, antivirus software, and other applications are up to date with the latest security patches. This helps protect your system from known vulnerabilities that malware might exploit.
- Change passwords: If there’s a possibility that the malware has obtained your passwords or sensitive information, change your passwords for all your online accounts, including email, social media, and banking.



