“Toitoin Unleashed: Trojan Horse Strikes Banking Firm!”
Banking firm in Latin America is targeted by a new banking Trojan horse known as toitoin. It is a multistage attack. Phishing is just the first stage of a multi-stage attack that targets financial institutions. The last stage involves the installation of a brand-new Trojan called Toitoin, which steals sensitive system data. The complex campaign was uncovered by Zscaler researchers. It uses a multistage infection chain with specially developed modules at each stage to inject malicious code into remote processes and bypass user account control (UAC), among other things.
Background:
In 2014, researchers first identified the banking Trojan known as ” Toitoin.” Its ability to be modified to target particular banks is a feature that distinguishes it as a modular piece of malware. Virus-filled spam emails with harmful attachments are the main way that Toitoin is propagated. Once it has been installed, Toitoin can be used to steal credit card numbers, passwords for online banking accounts, and other private data from victims’ computers. Transactions involving money can also be intercepted and changed using it. It is a sophisticated virus which is being updated constantly.
Working:
A multi-staged infection chain is followed across each stage using the custom modules by the Trojan. The malicious actions carried out by the custom modules during reboots and process inspections include:-
- UAC circumvention with code injection
- Sandbox avoidance
Toitoin trojan infection chain:
The targeted effort starts with a well-designed phishing email compromise and employs the TOITOIN malware infection chain from there. While the trick email in this campaign deliberately targets the Latin American Investment Banking firm.
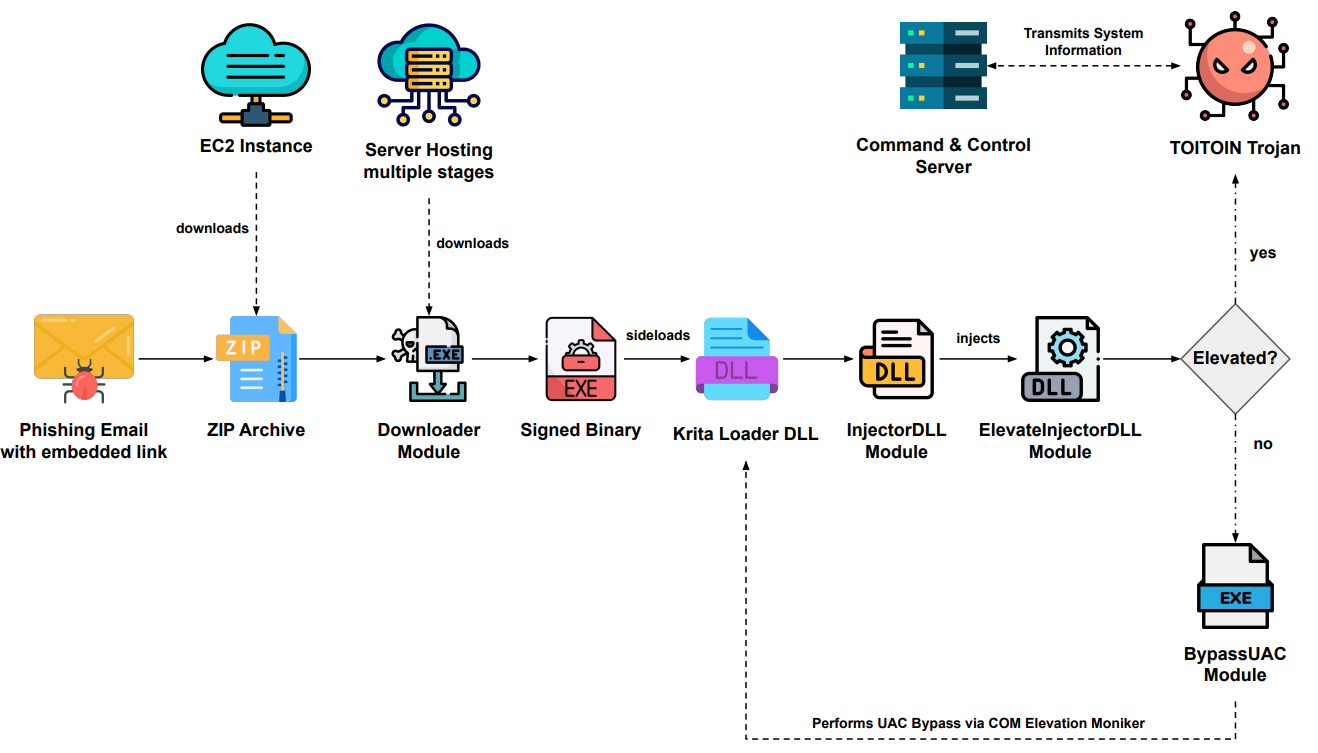
The email contains a Payment Notification Lure that is carefully prepared to entice the recipient to click “Visualizer Boleto” (View Invoice). Users are enticed to open the email’s contents by the sense of urgency created by this, falling into the threat actors’ trap.
Impact:
The Toitoin banking malware may have a major impact. The virus may empty victims’ bank accounts and compromise their financial data by stealing credit card numbers. The virus has even occasionally been used to steal money from corporations.
- Financial loss
- Identity theft
- Damage to reputation
Remediation:
- Use Strong Passwords and Change Them Periodically: Using strong and complex passwords significantly enhances your accounts’ security. A strong password typically includes a combination of upper- and lower-case letters, numbers, and special characters. Avoid easily guessable information like birthdates or common words. Changing passwords regularly reduces the chances of unauthorized access even if a password is compromised.
- Keep Your Operating System and Software Up to Date: Regularly updating your operating system and software is crucial to maintaining security. Updates often include patches to fix vulnerabilities that hackers could exploit. By keeping your system up to date, you ensure that you’re benefiting from the latest security enhancements and bug fixes.
- Only Use Secure Websites When Banking Online: When conducting online banking or other sensitive transactions, make sure the website uses HTTPS (HyperText Transfer Protocol Secure). The “s” in HTTPS indicates that the communication between your browser and the website’s server is encrypted, reducing the risk of interception and unauthorized access to your financial information.
- Be Careful with Links in Emails and Social Media Messages: Phishing attacks often involve malicious links that lead to fake websites designed to steal your personal information. Be cautious when clicking links in emails or social media messages, especially if the source is unfamiliar or the message seems suspicious. Hover over links to see their actual destination before clicking.
- Use a Reputable Antivirus Program: Installing a reputable antivirus program helps protect your computer from malware, viruses, and other malicious software. Antivirus programs scan files and websites for potential threats and can prevent harmful programs from running on your system.
- Back up Your Data Regularly: Regular data backups ensure that your important files are safe in case of hardware failures, data corruption, or ransomware attacks. Backing up your data to an external drive or a secure cloud storage service provides a way to recover your information even if your primary device is compromised.



