Ukrainian military is targeted by Russian state-sponsored “Infamous Chisel” Android malware
The “Infamous Chisel,” a new sophisticated malware, has been targeting crypto wallets and exchanges, as revealed in a joint report by the U.S. Federal Bureau of Investigation (FBI) and the U.K.’s Government Communications Headquarters (GCHQ).
A report on a malware campaign targeting Android mobile devices used by the Ukrainian military was issued by the National Cyber Security Centre of the United Kingdom (NCSC) in collaboration with international partners.
The virus, Infamous Chisel, was employed by the Russian cyberthreat organization Sandworm, which is connected to the Main Centre for Special Technologies of the Main Intelligence Directorate of the Russian General Staff. Constant access to infected Android devices is provided by Infamous Chisel, which also collects and extracts data from them. “Infamous Chisel has very likely been used with the aim of stealing sensitive military information,” says the statement about the program, which also targets apps used by the Ukrainian military. This operation reveals how Russia is still supporting the invasion of Ukraine with its cyber capabilities.
The “Infamous Chisel’s capability to conduct recurring scans of network data that has been prepared for exfiltration is one of its worrying characteristics. It can access and export system and application configuration files once inside a system, giving malicious actors access to a wealth of data.
In addition to exfiltration, the virus has a network backdoor feature. Tor, also known as The Onion Router, and SSH (Secure Shell) make this possible. Such access provides criminals access to the device as well as some degree of anonymity.
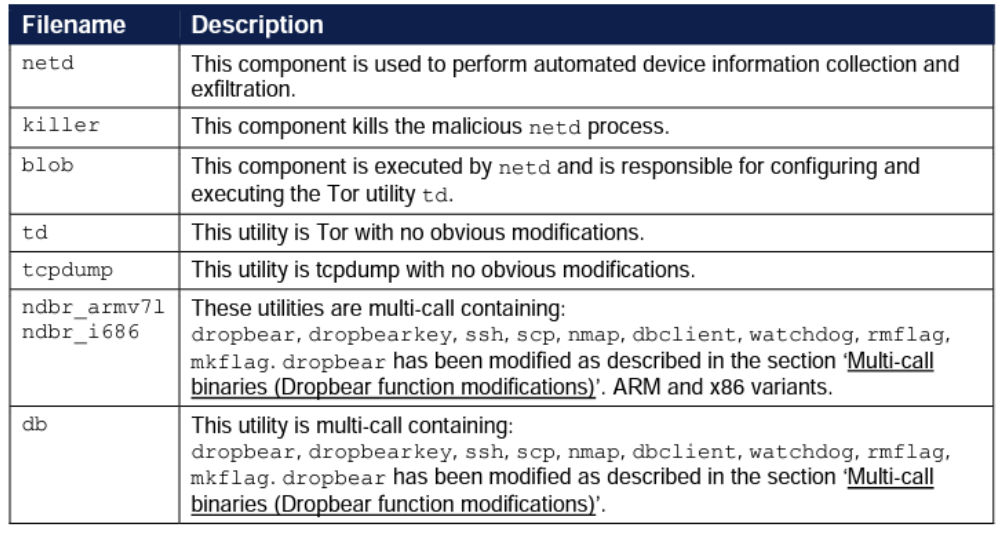
Figure 1 overview of components
Malware working:
- Delivery Mechanisms: Android malware is typically delivered through malicious apps, compromised websites, or phishing emails.
- Installation: Once downloaded, the malware often disguises itself as a legitimate app and requests various permissions during installation.
- Privilege Escalation: Malware may attempt to gain root access or exploit system vulnerabilities to gain elevated privileges.
- Data Theft: Malware can steal sensitive information such as personal data, login credentials, and financial information.
- Remote Control: Some malware allows attackers to remotely control the infected device, enabling them to perform various malicious actions.
- Botnets: Android malware can be used to create botnets, which are networks of compromised devices used for various cyberattacks.
- Payloads: Malware may download additional payloads or modules to extend its capabilities and avoid detection.
- Persistence: Malware may modify system files or settings to ensure it continues running even after device reboots.
- Evasion Techniques: Malware often employs techniques to evade detection, such as encryption, code obfuscation, and polymorphic behavior.
- Distributed Denial of Service (DDoS): Some Android malware participates in DDoS attacks, using infected devices to flood targeted servers or websites with traffic, causing them to become unavailable.
Remedies:
- Keep Software Updated: Regularly update your Android operating system and installed apps to patch known vulnerabilities.
- Download Apps from Trusted Sources: Only install apps from the official Google Play Store or reputable third-party sources.
- App Permissions: Review app permissions carefully and avoid apps that request excessive or unnecessary access to your device’s features.
- Install Antivirus Software: Use reputable antivirus and anti-malware apps to scan and protect your device.
- Enable App Verification: Enable the “Google Play Protect” feature on your device to scan apps for malware.
- Stay Informed: Keep up-to-date on the latest security threats and best practices for mobile device security.
- Use Strong Passwords: Protect your device with a strong, unique password or PIN, and enable biometric authentication if available.
- Regular Backups: Back up your data regularly to ensure you can recover it in case of a malware attack or data loss.
- Avoid Public Wi-Fi: Be cautious when connecting to public Wi-Fi networks, as they can be insecure and susceptible to attacks.



