Metastealer Malware Targets macOS Systems
This year has seen a surge in infostealers focusing on the macOS platform. Recently it has come to light that cybercriminals are employing MetaStealer, a specific type of malware focusing Mac users, primarily designed to illicitly acquire sensitive information from its targets.
MetaStealer, an application developed using the Go programming language, represents a notable menace to the privacy and security of Mac users. Typically, this malicious software is concealed within deceptive documents or files in the disk image format (DMG), occasionally disguised as an Adobe application or file.
Researchers from SentinelOne says that, this malware targeting business users is somewhat unusual for macOS malware, which is more commonly found being distributed via torrent sites or suspicious third-party software distributors as cracked versions of business, productivity or other popular software.
How Metastealer Works ?
The MetaStealer malware is designed specifically to target devices powered by Apple M1 and M2 processors, the researchers were able to find some indications of the malware’s functionality despite the obfuscation. The main component of the payload is an obfuscated Go-based executable that comes with features to harvest data from iCloud Keychain, saved passwords, and files from the compromised host. All the samples observed so far are designed for Intel-based macOS machines.
SentinelOne has observed DMGs named after Adobe software or client work, including the following:
- Advertising terms of reference (MacOS presentation).dmg
- CONCEPT A3 full menu with dishes and translations to English.dmg
- dmg
- Brief_Presentation-Task_Overview-(SOW)-PlayersClub.dmg
- dmg
- Adobe Photoshop 2023 (with AI) installer.dmg
This malware’s application packages consist of only the fundamental components, which include an Info.plist file, a Resources directory containing an icon image, and a macOS directory housing the malicious Mach-O executable.
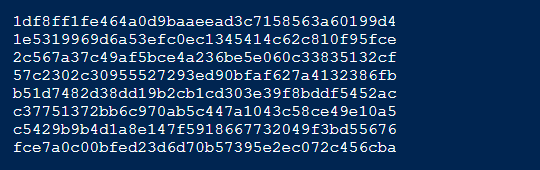
Mach-O Binaries – Intel x86_64
From samples of MetaStealer, security researchers observed reaching out to one of the following domains:
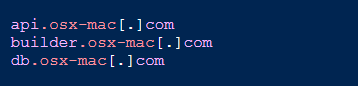
Malware reaching out Domains
Cybercriminals employ cunning tactics to lure users into infecting their computers with MetaStealer. They primarily rely on social engineering techniques, such as posing as fake clients or leveraging enticing filenames, to deceive victims into launching malicious payloads. The malware is often concealed within disk image bundles, with filenames that suggest business relevance, creating a sense of legitimacy to entice business users.
Researchers first identified MetaStealer in March, and newer versions have appeared steadily since then. Last week, Apple added a detection signature for MetaStealer to its XProtect antimalware system for macOS. MetaStealer stands out among the latest malware threats due to its specific focus on business users and its primary goal of extracting valuable information from their keychains and other sources. This valuable data is subsequently employed for various cybercriminal activity or to establish a presence within a larger corporate network.
MetaStealer capabilities:
MetaStealer poses a substantial data security risk, as it can steal sensitive information, opening the door to identity theft, financial harm, and privacy violations. When it sets its sights on business users, MetaStealer can disrupt company functions, jeopardize confidential data, and bring about financial losses while tarnishing the organization’s image. Specifically, the malware features functions allow for exfiltrating the keychain and extracting saved passwords, stealing files from the system. Also select versions of the malware have been observed containing functions that likely target Telegram and Meta services.
The keychain is a system-level password management system for macOS, managing credentials for websites, applications, WiFi networks, certificates, encryption keys, credit card information, and even private notes. Therefore, the ability to extract keychain contents represents a potent capability that could grant attackers access to confidential information.
These manipulative social engineering strategies exploit the victim’s trust, coaxing them into unwittingly running the concealed malware. Once activated, MetaStealer acquires unauthorized entry to the victim’s macOS system, commencing its data-stealing activities. Additionally, bogus applications such as TradingView are employed to distribute MetaStealer, the same tactic that has been adopted by Atomic Stealer in recent weeks.
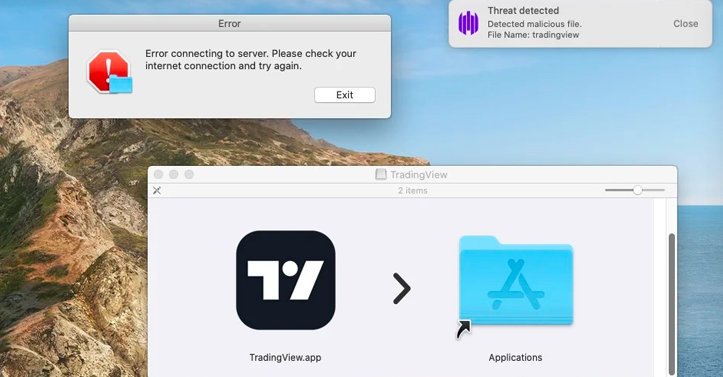
How to Stay Safe from MetaStealer?
- Apple’s XProtect update v2170 contains a detection signature for some versions of MetaStealer but not all. Hence perform recommended Updates for Apple’s XProtect.
- Deploy IDPS to monitor network traffic for signs of malicious activity and take action to prevent or mitigate threats.
- Utilize trustworthy antivirus or anti-malware software to detect and prevent potential threats, and also ensure that you regularly update these security tools to stay prepared against the most recent strains of malware.
- Enforcing strict role-based access controls and permissions to restrict unauthorized users or processes from accessing sensitive data and systems overall the organization.
- Implement Zero trust policy on the Organization, is a cybersecurity approach that assumes no inherent trust for any user or system, even those within an organization’s network.
- Provide training to employees to help them distinguish between malicious activities, such as social engineering, recognize malicious file downloads and other activities on their systems.
- Ensure that employees are aware of social engineering techniques and how to identify malicious files and links leads to social engineering.



