MGM Data Breach
MGM Resorts recently acknowledged that it appeared to have been the victim of a significant hack, which forced it to halt operations at many hotels. They are still investigating the situation, so they can’t yet say whether any customer or employee data was compromised. In an effort to educate anybody who may have been impacted by the MGM Resorts breach about the hazards they could encounter as a result of the breach and their legal rights, the data breach attorneys at Console & Associates, P.C. are looking into potential claims from those individuals.
In February 2020, MGM Resorts suffered a data breach affecting approximately 10.6 million guests. The breach was initially reported as unauthorized access to a cloud server, but later reports suggested that the attackers may have gained access through a social engineering attack on an employee.
The MGM data breach is a cautionary tale for businesses of all sizes. It shows that even the most sophisticated security systems can be compromised if employees are not properly trained on how to identify and avoid social engineering attacks.
MGM Resorts Suffers Data Breach at the Hands of the Scattered Spider Hacking Group (Recent Data Breach)
On September 11, 2023, MGM Resorts International, the largest casino company in Las Vegas, suffered a data breach at the hands of the Scattered Spider hacking group. The attack disrupted operations at MGM’s casinos across the United States, forcing the company to shut down some systems to contain the incident.
Who is Scattered Spider?
A gang of threat actors known as Scattered Spider is thought to utilize a variety of social engineering tricks to break into corporate networks.
These attacks include phishing and MFA fatigue to access multi-factor authentication codes, SIM switch attacks to take over the phone number of a targeted mobile device, and impersonating help desk staff to deceive users into providing credentials.
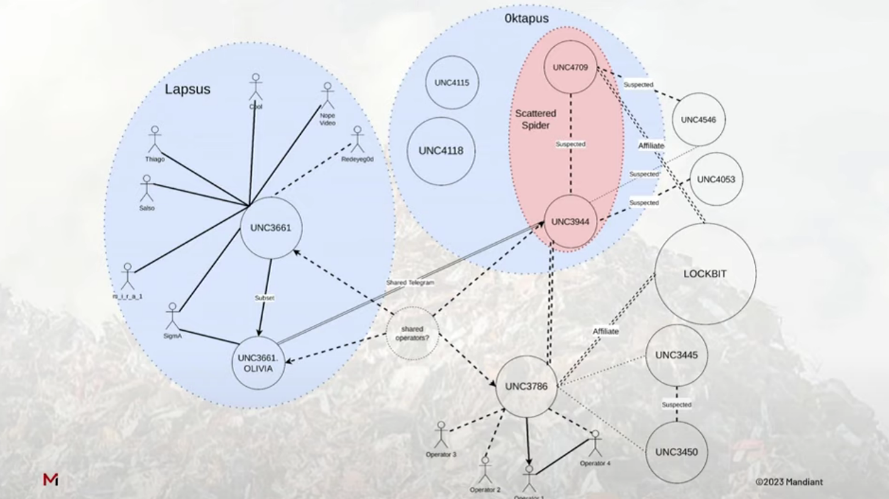
Unlike most ransomware affiliates who are from CIS countries, researchers believe that the hacking group consists of English-speaking teenagers and young adults ranging from 16-22 years of age. Furthermore, due to the similar tactics, researchers have noticed a connection between Scattered Spider and the Lapsus$ hacking group, which had a similar makeup for members and tactics.
A Scattered Spider campaign called ‘0ktapus’ was used to target over 130 organizations to steal Okta identity credentials and 2FA codes, with some of those targets including T-Mobile, MetroPCS, Verizon Wireless, AT&T, Slack, Twitter, Binance, KuCoin, CoinBase, Microsoft, Epic Games, Riot Games, Evernote, AT&T, HubSpot, TTEC, and Best Buy.
Technical Aspects:
The technical aspects of the attack are still under investigation, but it is believed that the Scattered Spider group gained access to MGM’s systems through a social engineering attack. The tremendous visibility of the disturbance was one sign that it was a ransomware attack. “The fact that everything’s down,” Hamerstone claims. Imply that everything wouldn’t be down if you were going to break in covertly, steal data, and then do something with it.”
In the case of the MGM attack, it is believed that the Scattered Spider group sent phishing emails to MGM employees that appeared to be from legitimate companies. The emails contained links to malicious websites that, when clicked, installed malware on the employees’ computers.
Once the malware was installed, the Scattered Spider group was able to steal login credentials and other sensitive information from the employees’ computers. This information was then used to gain access to MGM’s systems.
Impact of the Attack:
The impact of the MGM data breach is still being assessed, but it is known that the attackers exfiltrated a significant amount of data from the company’s systems. This data may include customer names, addresses, Social Security numbers, and credit card information.
MGM Resorts has stated that it is working with law enforcement to investigate the attack and that it is taking steps to protect its customers’ data. The company has also offered free credit monitoring to customers who may have been affected by the breach.
What Can Companies Do to Protect Themselves from Data Breaches?
There are a number of things that companies can do to protect themselves from data breaches, including:
- Educate employees about social engineering attacks: Employees should be trained on how to identify and avoid social engineering attacks. This training should cover common phishing techniques and how to spot suspicious emails.
- Implement multi-factor authentication (MFA): MFA requires users to provide two or more factors of authentication, such as a password and a one-time code, when logging in to systems and applications. This makes it more difficult for attackers to gain access to accounts, even if they have stolen a user’s password.
- Regular Software Updates and Patching: Keep all software, operating systems, and applications up to date with the latest security patches. Cybercriminals often exploit known vulnerabilities in outdated software to inject malware.
- Segment networks and systems: Segmenting networks and systems can help to contain the spread of a data breach if it does occur. By isolating different systems from each other, attackers can be prevented from moving laterally across the network and gaining access to additional systems.
- Regularly back up data: Companies should regularly back up their data to a secure location so that they can restore it in the event of a data breach or other disaster.
By adopting these preventive measures and maintaining a proactive approach to cyber security, organizations can significantly reduce the likelihood of social engineering and enhance their overall security posture.



