Middle East Cyber Espionage Unveiled: Deadglyph Malware’s Stealthy Operations
In a recent cyberespionage incident targeting a government agency in the Middle East, security experts have identified a new and highly sophisticated backdoor malware known as “Deadglyph.” This malicious software has been linked to the Stealth Falcon Advanced Persistent Threat (APT), a state-sponsored hacking group originating from the United Arab Emirates (UAE).
The hacking group has been known for targeting activists, journalists, and dissidents for almost a decade. Security Researchers shares analysis of the new modular malware and how it infects Windows devices.
Deadglyph Attacks:
Security researchers lack information on the initial infection method, but there is suspicion that a malicious executable, potentially a program installer, is employed. Nevertheless, they have managed to dissect most elements of the infection chain, shedding light on how the malware functions while attempting to evade detection.
The Deadglyph malware’s loading sequence initiates with a registry shellcode loader (DLL) responsible for extracting code from the Windows registry to activate the Executor (x64) component, which subsequently loads the Orchestrator (.NET) component. Notably, only the initial component persists as a DLL file on the compromised system’s disk, significantly reducing the risk of detection.
To further obscure its activities, the loader retrieves shellcode from the Windows Registry, encrypting it to heighten the complexity of analysis. Given that DLL components are more susceptible to detection when stored in the file system, threat actors have cunningly employed a homoglyph attack within the VERSIONINFO resource. This attack utilizes distinctive Greek and Cyrillic Unicode characters to mimic Microsoft’s information, thereby appearing as a legitimate Windows file. This tactic cleverly exploits the visual similarity of characters while maintaining distinct differences, such as the use of Greek Capital Letter San (U+03FA, Ϻ) and Cyrillic Small Letter O (U+043E, о) in Microsoft Corporation.
Following this intricate loading process, the Executor component proceeds to load AES-encrypted configurations for the backdoor. It initializes the .NET runtime on the system, enabling the loading of the .NET section of the backdoor while serving as its library. Finally, the Orchestrator assumes responsibility for command-and-control server (C2) communications, utilizing two dedicated modules known as ‘Timer’ and ‘Network.’ In the event of a failure to establish communication with the C2 server within a predetermined timeframe, the malware triggers a self-removal mechanism, thwarting any attempts at analysis by researchers and cybersecurity experts.
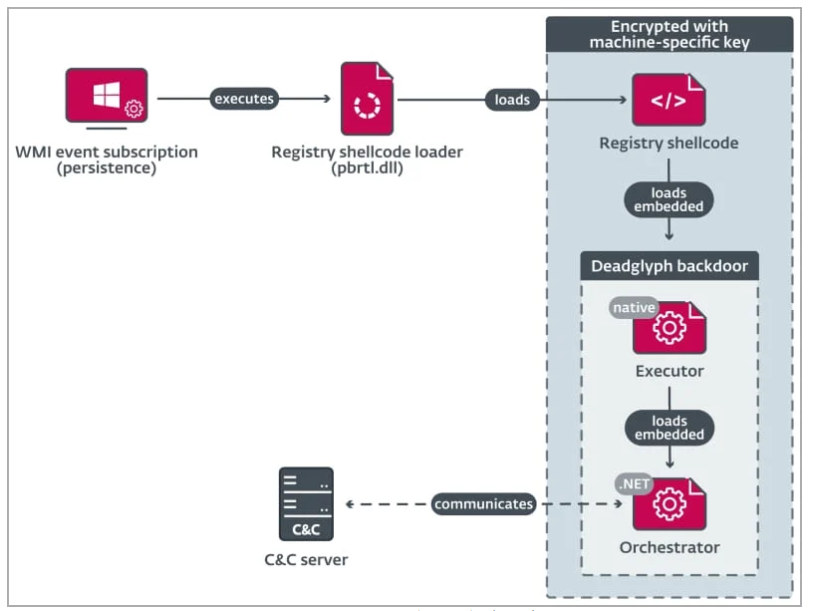
The Deadglyph loading chain
Deadglyph : A modular malware
The Deadglyph malware operates with a modular architecture, allowing it to dynamically retrieve additional modules from the command-and-control server (C2). These modules contain various shellcodes designed to execute specific tasks through the Executor component.
This modular approach provides threat actors with the flexibility to craft customized attacks by developing and deploying new modules as required. These modules leverage both standard Windows APIs and specialized Executor APIs, encompassing a total of 39 distinct functions. These functions enable a wide range of actions, including file operations, executable loading, Token Impersonation, encryption, and hashing.
Security researchers speculate that there exist between nine to fourteen unique modules, although their examination yielded access to only three specific ones: a process creator, an information collector, and a file reader.
The information collector uses WMI queries to feed the Orchestrator with the following information about the compromised system:
- operating system
- network adapters
- installed software
- drives
- services
- drivers
- processes
- users
- environment variables
- security software
The process creator operates as a tool for executing predefined commands as separate processes, relaying the outcomes to the Orchestrator. Meanwhile, the file reader module serves the purpose of extracting file content and transmitting it to the Orchestrator. It also grants operators the choice to delete the file post-extraction.
Although security researchers could only unveil a portion of the malware’s functionalities, it is evident that Deadglyph, attributed to Stealth Falcon, represents a significant and formidable threat in the realm of cybersecurity.
Remediations:
- Stay Informed: Regularly update your cybersecurity knowledge and threat intelligence to understand emerging threats like Deadglyph.
- Enhance Cyber Hygiene: Educate employees to avoid suspicious downloads and phishing emails.
- Implement Robust Endpoint Security: Deploy advanced security tools for malware detection and prevention.
- Keep Systems Updated: Maintain up-to-date software and patch known vulnerabilities.
- Network Segmentation: Segment your network to limit the malware’s lateral movement.
- Incident Response Plan: Develop and test an incident response plan for quick and effective mitigation.
- Backup and Recovery: Maintain regular backups of critical data and systems. In the event of a malware infection or ransomware attack, having up-to-date backups can be a lifesaver.
- Zero Trust Architecture: Consider implementing a zero-trust architecture where trust is never assumed, and verification is required from anyone trying to access resources in your network.



