From Watering Hole to Spyware: EvilBamboo Targets Tibetans, Uyghurs, and Taiwanese
Tibetan, Uyghur, and Taiwanese individuals and organizations are the targets of a persistent campaign orchestrated by a threat actor codenamed EvilBamboo to gather sensitive information.
“The attacker has created fake Tibetan websites, along with social media profiles, likely used to deploy browser-based exploits against targeted users,” Volexity security researchers Callum Roxan, Paul Rascagneres, and Thomas Lancaster said in a report published last week.
Targeting Android: Work is continuing to create the proprietary malware families BADBAZAAR, BADSIGNAL, and BADSOLAR to infect CCP opponents.
The attacker has constructed phony Tibetan websites and social media pages, which they probably utilized to spread browser-based vulnerabilities against specific victims.
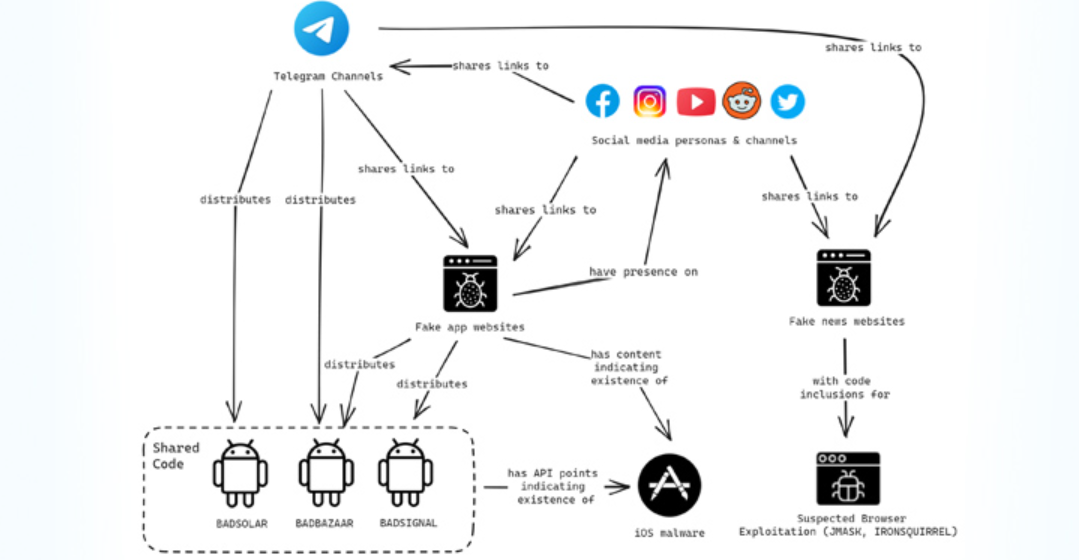
Building communities to aid in malware distribution: The attacker has developed communities on internet platforms like Telegram to help with malware distribution, in part by imitating already well-known communities.
iOS applications: Volexity uncovered solid proof that malicious iOS apps were being spread successfully through the Apple App Store.
Using a unique JavaScript profiling framework, the attackers were able to identify iOS-powered devices, according to Volexity, who believes this might have been used to send malware to just certain targets. Additionally, Volexity found evidence supporting the ongoing usage of IRONSQUIRREL.
A zero-day vulnerability in the WebKit browser engine, which Apple addressed at the beginning of 2019, was used by attacks against the Apple mobile operating system to distribute the spyware strain Insomnia. In March 2021, Meta claimed to have discovered the threat actor utilizing its platforms illegally to spread malware-hosting websites.
The organization is also notorious for disguising dictionary, keyboard, and prayer apps found on third-party app marketplaces as Android spyware like ActionSpy and PluginPhantom to steal sensitive information from victim devices.
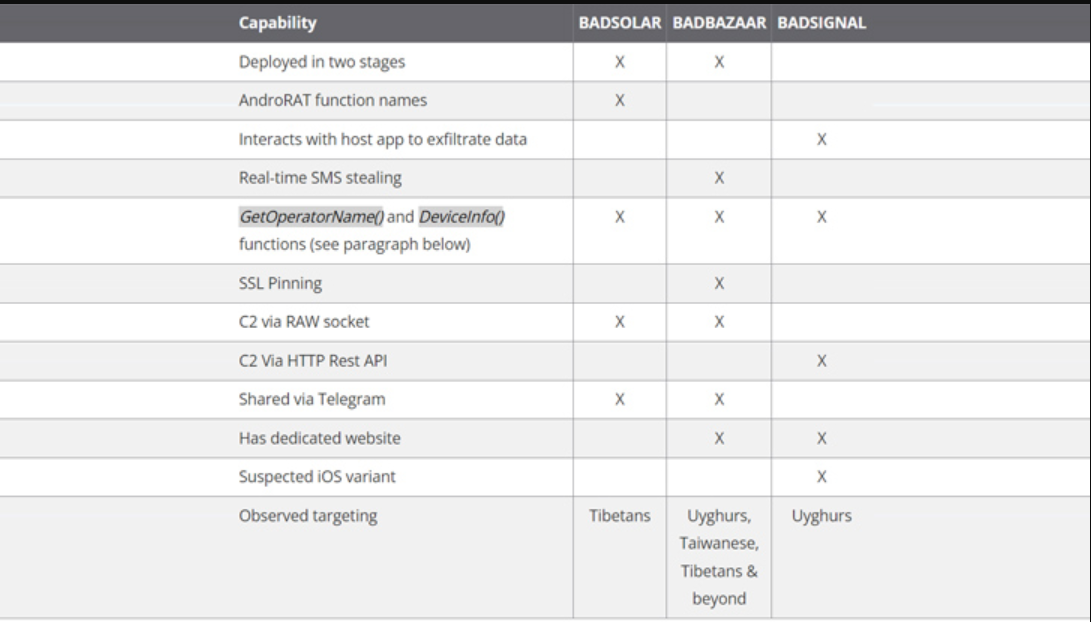
Three new Android espionage tools, BADBAZAAR, BADSIGNAL, and BADSOLAR, are attributed to EvilBamboo according to the most recent research from Volexity. The first of these tools was identified by Lookout in November 2022.
Fake Websites Leading to Malicious JavaScript:
A user who routinely shares BADSOLAR samples via the “Tibetanphone” Telegram group also shared a link to ignitetibet[.]net. This website is currently active and hosted on infrastructure (45.154.12[.]80) that has overlaps with uyghurinfo[.]net, which also shares a distinct registration pattern with several of the BADSOLAR C2 domains. Further, the same IP address hosts a website that has a simple survey regarding Taiwan’s independence tw.tinmf[.]org.
Additionally, BADSOLAR-backdoored programs and booby-trapped URLs that, when clicked, launch malicious JavaScript to profile and fingerprint the system have been sent via messages exchanged through Telegram channels.
While BADSOLAR appears to be used largely with applications that have Tibetan themes, BADBAZAAR appears to be used primarily to target Uyghur and other adherents of the Muslim faith. However, a second stage that is received from a distant server by both strains incorporates their harmful capabilities.
AndroRAT, an open-source Android remote access trojan, is also a derivative of the second-stage malware created by BADSOLAR. In contrast, BADSIGNAL includes all aspect of information collecting in the primary package.
Remedies:
- Keep Software Updated: Ensure your operating system, applications, and antivirus software are up to date with the latest security patches.
- Use Reputable Antivirus Software: Install and regularly update a trusted antivirus and anti-malware program to scan for and remove potential threats.
- Practice Safe Browsing: Be cautious when clicking on links or downloading files from unfamiliar sources, especially in emails or on websites that seem suspicious.
- Use Strong, Unique Passwords: Employ strong and unique passwords for your online accounts, and consider using a password manager to keep track of them.
- Enable Two-Factor Authentication (2FA): Whenever possible, enable 2FA on your online accounts for an extra layer of security.
- Avoid Jailbreaking or Rooting Devices: Avoid modifying your mobile device’s operating system beyond what’s officially supported, as this can make it more vulnerable to malware.
- Regularly Backup Data: Regularly back up your important data to a secure location so that you can recover it in case of malware or other data loss incidents.



