Xenomorph Android malware targets U.S. banks
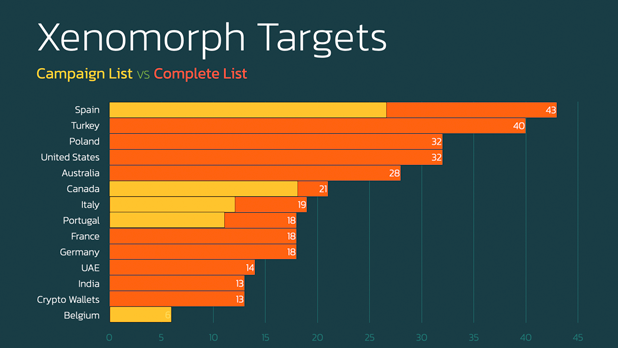
Security researchers have identified a new campaign aimed at distributing an enhanced version of the Xenomorph malware, Xenomorph v3. This malware variant was developed by the threat actor group known as Hadoken Security Group, and it is targeting Android device users. The Xenomorph malware was initially discovered in February 2022, emerging into the spotlight for the first time as it focused its attention on 56 European banks. This was achieved through the deployment of dropper applications released on the Google Play Store. The most recent release of Xenomorph is focused on individuals who use cryptocurrency wallets and a range of financial institutions in the United States. Xenomorph v3, the latest iteration of this malware, has been crafted with the aim of targeting over 400 banking and financial entities, encompassing cryptocurrency wallets like Binance, BitPay, Coinbase, and many others.
At first, they employed Google Pay to disseminate the malware. The operators now distributing it via phishing Web pages. These malicious sites falsely claim that users need to update the victim’s Chrome browser urgently.
What is Xenomorph?
In early 2022, Xenomorph made its initial appearance in the wild, functioning as a banking trojan primarily aimed at 56 European banks through a screen overlay phishing technique. Its distribution took place via Google Play, where it managed to accumulate more than 50,000 installations. At that point, Xenomorph had earned a place among Zimperium’s (Mobile application security solution) top ten most active banking trojans, solidifying its status as a significant and prominent threat. In August of 2022, the Xenomorph was being distributed through a discovered dropper called ‘BugDrop,’ effectively circumventing security measures in Android 13. The new variant, Xenomorph v3, represents a substantial upgrade from the initial version. The latest iteration of the Xenomorph malware is now capable of initiating designated applications, displaying push notifications, exfiltrating cookies, and redirecting calls, among its array of functionalities.”
In their most recent campaign, the malware operators opted to use phishing pages, luring visitors to update their Chrome browser and trick them into downloading the malicious APK.

Fake Chrome Update Page
Instead of a legitimate update, users unknowingly download an APK file containing the Xenomorph malware. This malware then steals information from bank and crypto apps. Like other banking malware, Xenomorph contains an overlay that spoofs the account login pages of all the targeted banks. When an Android user with a compromised device tried to access their account with any of the banks targeted, the malware would immediately show a spoofed version of the bank’s login page. This fake page was designed to illicitly collect usernames, passwords, and additional account details. Xenomorph also included functionality for intercepting and stealing two-factor authentication tokens sent through SMS messages. The notable feature of Xenomorph v3 is its sophisticated and flexible Automatic Transfer System (ATS) framework, which facilitates the automatic transfer of funds from a compromised device to one controlled by an attacker. Security researchers observed that the new version of Xenomorph is being distributed through third-party hosting services, primarily the Discord Content Delivery Network (CDN).
Measures Taken to Counter Malware:
- Always be cautious of unsolicited messages or websites claiming urgent updates.
- Encourage users to download apps only from official app stores like Google Play. Warn against sideloading apps from unverified sources.
- Always verify the URLs and domains before clicking on any links, whether they are from unknown sources or even from familiar contacts.
- Activate Google Play Protect, which scans apps for malware on your device regularly. You can find this in your device’s settings.
- Regularly check the apps installed on your device and promptly uninstall any apps that you cannot identify or are not familiar with.
- Advise users to review app permissions on the devices carefully before installing any app. Only grant permissions that are necessary for the app’s functionality.
- Ensure your online security by relying on a trusted antivirus application. These specialized apps not only provide superior protection but also shield you from harmful malware threats.
- If you suspect any unusual activity on your bank accounts, contact your bank immediately to report it.



