LUCR-3: Scattered Spider Getting SaaS-y in the Cloud
LUCR-3 is a financially motivated attacker who uses the Identity Provider (IDP) as initial access into an environment with the intention of stealing Intellectual Property (IP) for extortion. It has similarities to groups like Scattered Spider, Oktapus, UNC3944, and STORM-0875. The Fortune 2000 corporations targeted by LUCR-3 operate in a variety of industries, including but not limited to software, retail, hospitality, manufacturing, and telecommunications.
In order to accomplish its objectives, LUCR-3 skillfully makes use of the victims’ own tools, programs, and resources rather than relying primarily on malware or even scripts. Initial Access is generally obtained by using already compromised identities in the IDP (Okta: Identity Cloud, Azure AD/ Entrap, Ping Identity: Ping One). In order to understand how the victim organization functions and how to gain access to sensitive information, LUCR-3 makes advantage of SaaS applications including document portals, ticketing systems, and chat applications. They carry out their mission of data theft using the information they gathered during their reconnaissance within the SaaS apps. Customer data, IP, and code signing certificates are the three main targets of data theft.
LUCR-3 is a financially motivated threat actor that uses data theft of sensitive data (IP, Customer data, Code Signing Certificates) to attempt extortion. While extortion demands do vary, they are often in the tens of millions of dollars. Some personas within LUCR-3 will often collaborate with ALPHV to carry out the extortion phase of the attack.
The majority of the Windows 10 computers used by LUCR-3 for its cloud-based mission run GUI utilities. LUCR-3 may move around an organization without setting off any alarms by utilizing native SaaS application functionalities like search. The threat actor frequently uses the AWS administration panel (through a web browser) and the S3 Browser (version 10.9.9) in AWS. For any task requiring direct connection with the AWS API, LUCR-3 uses AWS Cloudshell inside the AWS administration console.
Attacker Lifecycle:
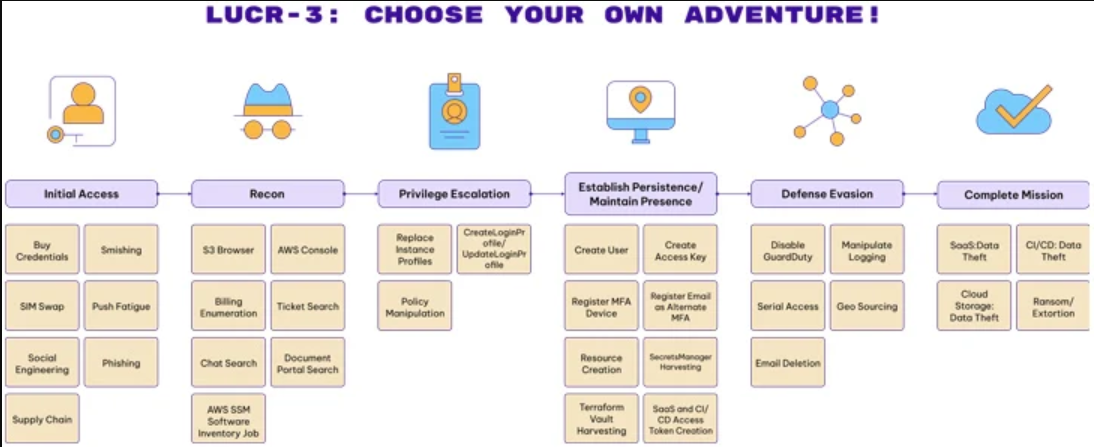
Initial access (IA)
LUCR-3’s initial access into an environment is gained through compromised credentials. They are not performing noisy activities like password spraying to find passwords. When they connect, they already have a legitimate password to use. The typical approach for them is:
- Identify credentials for the intended victim identity
- Bypass Multi-factor Authentication (MFA)
- Modify MFA settings
Recon (R)
R-SaaS#
LUCR-3 needs to know where the crucial data is and how to access it in order to achieve their objectives of data theft, ransom, and extortion. They carry out their duties similarly to any other employee. LUCR-3 can learn about an environment utilizing native applications without raising red flags by searching through and examining documents in various SaaS services like SharePoint, OneDrive, knowledge applications, ticketing solutions, and chat applications. LUCR-3 employs keywords for locating credentials, learning about software deployment environments, the process of code signing, and sensitive data.
R-AWS#
In AWS, LUCR-3 carries out recon in a variety of methods. To understand what kinds of services are being used, they will simply travel around the AWS Management Console into services like billing, and then navigate each of those services in the console. Additionally, LUCR-3 needs to know which applications are running on an organization’s computing systems (EC2 instances). The native AWS- Gather Software Inventory job will be run against all EC2 instances by LUCR-3 using Systems Manager (SSM), returning the software installed on the EC2 instances. Last but not least, LUCR-3 will use the GUI tool S3 Browser in conjunction with a durable access key to view the S3 buckets that are accessible.
Privilege Escalation (PE): AWS
There are three primary methods for privilege escalation in AWS that PE-AWS# LUCR-3 has used:
Changes to current EC2 instance roles’ policies as well as the creation of new roles with fully open policies have been observed with LUCR-3.
Update Login Profile: To assign a password to an identity so they may use it for AWS Management Console logons, LUCR-3 will update the login profile and, occasionally, build one if it doesn’t already exist.
Secrets Manager Harvesting: For programmatic access from their cloud infrastructure, many enterprises store credentials in Secrets Manger or Terra form Vault. To scrape all of the credentials stored in Secrets Manager and related programs, LUCR-3 will use AWS CloudShell.
Establish Persistence/ Maintain Presence (EP)
LUCR-3 employs various techniques to establish persistence and maintain a presence in different environments:
EP-AzureAD/Okta: Reset/Register Factor: They register their own device to ensure continued access and may monitor ecosystem switches and multiple user-device registrations.
Alternate MFA: LUCR-3 utilizes alternate MFA options, registering external emails with names aligned with the victim’s identity.
Strong Authentication Type: They may modify settings to allow SMS as a factor, changing Strong Authentication Method from Phone App OTP to One Way SMS in AzureAD.
EP-AWS: Create User: LUCR-3 attempts to create IAM Users with names matching the victim’s identity.
Create Access Key: They create access keys for IAM Users, often using S3 Browser for interactions with S3 buckets.
Create Login Profile/Update Login Profile: When stealth is necessary or IAM User creation isn’t possible, they create or update login profiles for existing users to gain their privileges.
Credential Harvesting: They target credential vaults like AWS Secrets Manager and Terra form Vault for victim organization and partner credentials.
Resource Creation: LUCR-3 creates or takes over resources (e.g., EC2 instances) for access and as staging areas for data theft.
EP-SaaS: LUCR-3 searches for credentials in various applications like ticketing systems, chat programs, document stores, and knowledge apps.
They create access tokens within these applications to interact with SaaS APIs.
EP-CI/CD: LUCR-3 generates access tokens for interacting with code repository APIs, such as GitHub and GitLab.
These techniques allow LUCR-3 to maintain a persistent presence across different environments, increasing their chances of continued access even if initial compromises are detected.
Defense Evasion (DE)
LUCR-3 employs various defense evasion tactics in different environments:
DE-AWS:
Disable Guard Duty: LUCR-3 deletes Guard Duty detectors and attempts to hinder re-addition by deleting invitations.
Stop Logging: They use actions like Delete Trail and Stop Logging to evade AWS detections.
Serial Console Access: LUCR-3 may enable serial console access for compromised AWS accounts, allowing them to establish hardware-based serial connections to EC2 instances, evading network monitoring.
DE-AzureAD/Okta:
Geolocation Spoofing: To avoid impossible travel detections, LUCR-3 sources their activities from geolocations similar to their victim identity, often using residential VPNs.
DE-M365/Google Workspace:
Email Deletion: LUCR-3 deletes emails sent to victims’ mailboxes as a result of their actions to avoid detection. Monitoring email deletions with sensitive terms (e.g. access token, MFA) in the web version of Outlook can provide higher fidelity signals for detection.
Complete Mission (CM)
LUCR-3’s primary mission is financial gain, achieved through:
In SaaS Applications:
Searching and downloading documents and web pages using traditional web browsers.
In AWS:
Data theft in S3.
Targeting database applications like Dynamo DB and RDS for sensitive data.
In CI/CD Environments (e.g., GitHub and GitLab):
Utilizing features like clone, archive, and view raw to access and download source data for their financial gain.
Remedies:
- Enforce strong passwords and multi-factor authentication (MFA).
- Implement continuous monitoring and anomaly detection.
- Educate employees on recognizing and reporting threats.
- Follow cloud security best practices for secure configurations.
- Deploy advanced endpoint protection and keep systems updated.
- Encrypt sensitive data at rest and in transit.
- Develop and test an incident response plan.
- Regularly back up data and test restoration procedures.
- Assess third-party vendor security and adherence to standards.
- Invest in email security solutions and advanced threat protection.



