HTTP/2 Zero-Day Vulnerability Leads To DDoS Attacks
Introduction:
In the world of cybersecurity, Zero-day vulnerabilities, in particular, pose a significant threat as they are flaws in software that are exploited by hackers before the developers have a chance to fix them. One such recent incident involves the exploitation of a zero-day vulnerability in HTTP/2, leading to record-breaking Distributed Denial of Service (DDoS) attacks. In this blog, we will delve into the details of the HTTP/2 Rapid Reset Zero-Day Vulnerability and its exploitation in launching massive DDoS attacks.
The World Wide Web uses the HTTP/2 protocol, which is a major revision of the HTTP protocol. It was developed to improve the efficiency of web communication, making web pages load faster and reducing latency. While HTTP/2 has brought many benefits to web performance, it has also introduced new security challenges.
A zero-day vulnerability refers to a security flaw that is unknown to the software vendor or the community at large. This term “zero-day” implies that the vulnerability has existed for zero days, meaning there is no patch or fix available when it is exploited. Hackers actively seek out such vulnerabilities to exploit them before they can be mitigated, often causing significant damage in the process.
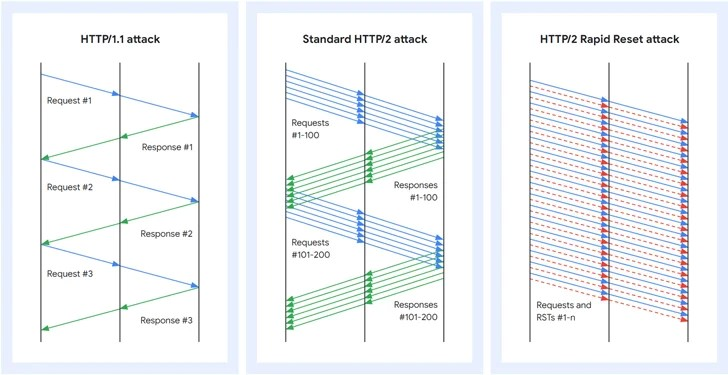
The HTTP/2 Rapid Reset Zero-Day Vulnerability:
The HTTP/2 Rapid Reset Zero-Day Vulnerability, also known as CVE-2023-44487, was discovered by a security researcher. This vulnerability allowed an attacker to send malicious requests to a vulnerable server, causing it to enter into a rapid reset loop. This loop would overload the server’s resources, ultimately leading to a complete denial of service for legitimate users.
Once the vulnerability was identified, hackers wasted no time in exploiting it. By crafting specially designed HTTP/2 requests, they were able to target a wide range of servers and web services that supported the protocol. The rapid reset loop effectively overwhelmed the targeted servers, rendering them inaccessible to legitimate users. This technique was used to launch massive DDoS attacks on various high-profile websites and services.
The scale of the DDoS attacks that followed the exploitation of the HTTP/2 Rapid Reset Zero-Day Vulnerability was unprecedented. Some of the affected websites reported a significant increase in traffic, reaching several terabits per second. This magnitude of traffic overload resulted in extended downtimes, frustrating users and causing financial losses for affected businesses.
Impact on Targeted Websites:
The impact of these record-breaking DDoS attacks on targeted websites was severe. Not only did they suffer downtime and service disruption, but they also had to allocate substantial resources to mitigate the attacks and implement temporary workarounds. Additionally, the attacks damaged their reputation and eroded trust among their user base.
Remediations:
- Apply Vendor Patches and Updates: The first step is to apply patches and updates provided by software vendors to fix the zero-day vulnerability. Ensure that all servers, web services, and software components that support HTTP/2 are updated promptly. Regularly monitor vendor security advisories to stay informed about any new patches or updates.
- Reconfigure Security Settings: Review and adjust security configurations for web servers and network devices. This includes implementing rate limiting and traffic filtering to mitigate the risk of exploitation. Custom security rules should be created to detect and block malicious HTTP/2 requests.
- Conduct a Security Audit: Perform regular security audits and vulnerability assessments on your network infrastructure. Engage in penetration testing to identify potential weaknesses and vulnerabilities. Regularly scanning for new vulnerabilities is essential in identifying and addressing them before they can be exploited.
- Implement Intrusion Detection and Prevention Systems (IDPS): Install and configure IDPS systems that can detect unusual traffic patterns and block malicious requests. Intrusion detection and prevention systems can provide real-time alerts and take action to mitigate potential threats automatically.
- Establish an Incident Response Plan: Develop and maintain a comprehensive incident response plan that outlines the steps to take in the event of a security breach. This plan should include communication procedures, roles and responsibilities, and recovery strategies to minimize the impact of a successful attack.
- User and Staff Training: Ensure that your organization’s employees are well-informed about security best practices. Conduct regular training sessions on recognizing phishing attempts, avoiding downloading suspicious files, and reporting security incidents. Employee awareness can help prevent many security breaches.



