Microsoft’s October 2023 Patch Tuesday Addresses 103 CVEs
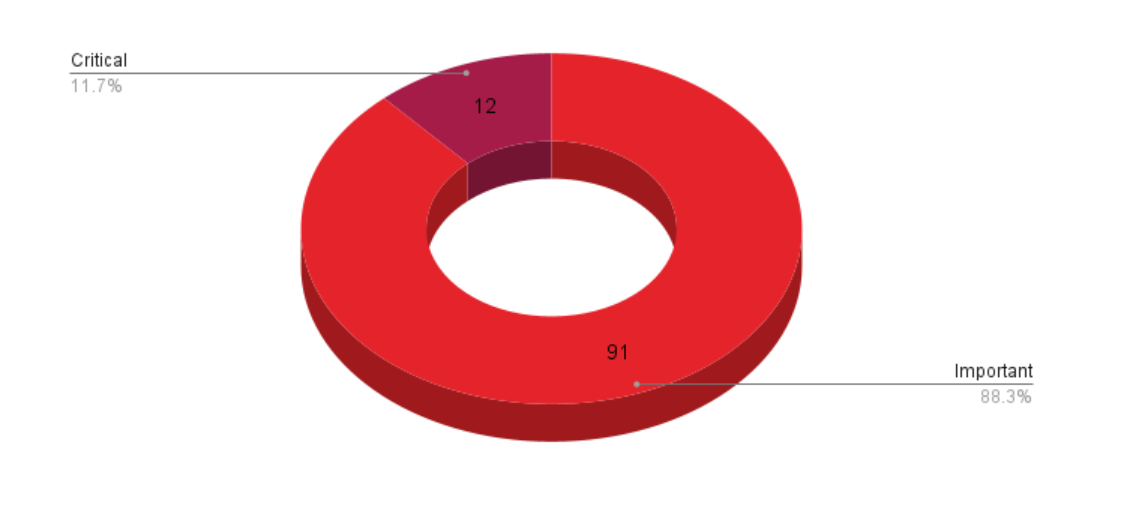
Microsoft addresses 103 CVEs including two vulnerabilities that were exploited in the wild. Microsoft patched 103 CVEs in its October Patch Tuesday release, with 12 rated as critical and 91 rated as important. We omitted CVE-2023-44487 from our counts as this vulnerability was reported to MITRE and not Microsoft and does not exclusively affect Microsoft products. Details about this flaw are included in our analysis below.
The two vulnerabilities that been weaponized as zero-days are as follows –
- CVE-2023-36563 (CVSS score: 6.5) – An information disclosure vulnerability in Microsoft WordPad that could result in the leak of NTLM hashes
- CVE-2023-41763 (CVSS score: 5.3) – A privilege escalation vulnerability in Skype for Business that could lead to exposure of sensitive information such as IP addresses or port numbers (or both), enabling threat actors to gain access to internal networks
“To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system,” Microsoft said in an advisory for CVE-2023-36563.
“Additionally, an attacker could convince a local user to open a malicious file. The attacker would have to convince the user to click a link, typically by way of an enticement in an email or instant message, and then convince them to open the specially crafted file.”
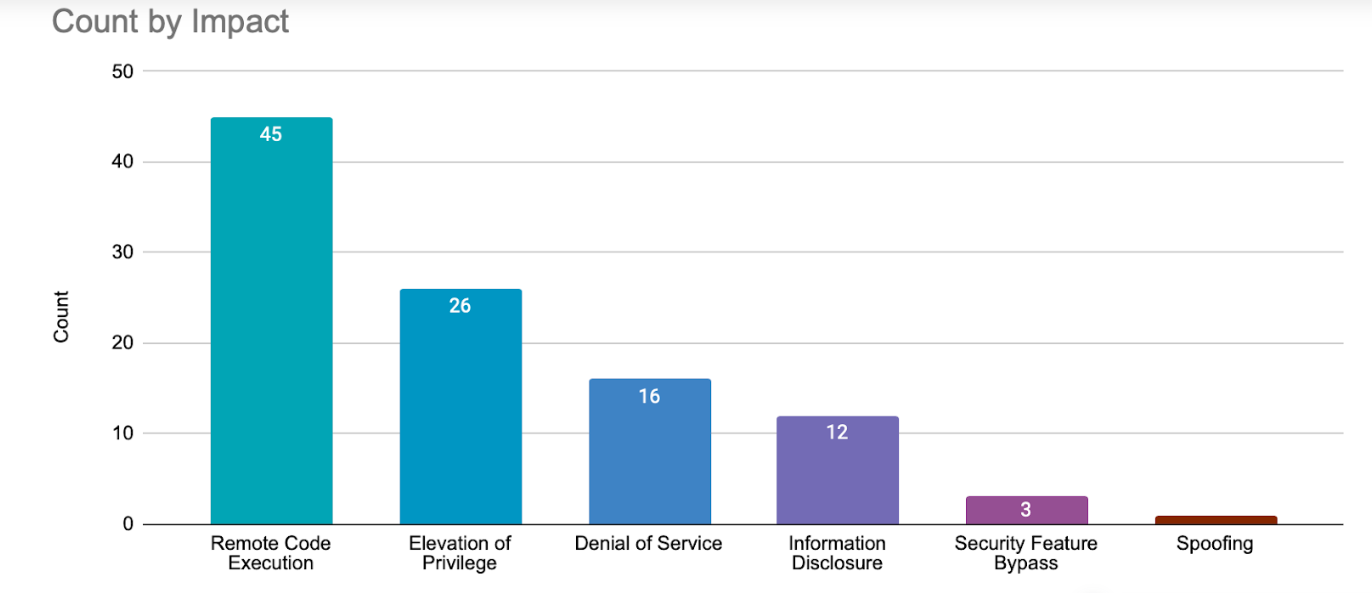
Also fixed by Redmond are dozens of flaws impacting Microsoft Message Queuing (MSMQ) and Layer 2 Tunneling Protocol that could lead to remote code execution and denial-of-service (DoS).
The security update further resolves a severe privilege escalation bug in Windows IIS Server (CVE-2023-36434, CVSS score: 9.8) that could permit an attacker to impersonate and login as another user via a brute-force attack.
The tech giant has also released an update for CVE-2023-44487, also referred to as the HTTP/2 Rapid Reset attack, which has been exploited by unknown actors as a zero-day to stage hyper-volumetric distributed denial-of-service (DDoS) attacks.
Finally, Microsoft has announced that Visual Basic Script (aka VBScript), which is often exploited for malware distribution, is being deprecated, adding, “in future releases of Windows, VBScript will be available as a feature on demand before its removal from the operating system.”
Remedies:
Here are some additional tips for protecting yourself from vulnerabilities:
- Keep your software up to date. Software developers regularly release updates to patch security vulnerabilities. By keeping your software up to date, you can help to protect yourself from known vulnerabilities.
- Use a strong password manager. A password manager can help you to create and store strong, unique passwords for all of your online accounts. This can help to protect your accounts from being compromised in a data breach or other attack.
- Be careful about the links you click on and the attachments you open. Phishing emails and malicious attachments are a common way for attackers to exploit vulnerabilities. If you receive an email or attachment from an unknown sender, or if you are unsure whether it is legitimate, do not click on any links or open any attachments.
- Use security tools and technologies. There are a variety of security tools and technologies available to help organizations protect themselves from vulnerabilities. These tools can include firewalls, intrusion detection systems, and security scanners.
- Have a plan in place for responding to incidents. Even with the best security measures in place, there is always a risk of being compromised. It is important to have a plan in place for responding to incidents so that you can minimize the damage and recover as quickly as possible.



