Malicious Google Ads Deceptively Target WinSCP Users for Malware Installation
In recent cybersecurity developments, threat actors are exploiting manipulated search results and deceptive Google ads to trick users seeking legitimate software, such as WinSCP, into unwittingly installing malware. This ongoing campaign, known as SEO#LURKER, has been identified and monitored by the cybersecurity company Securonix.
Attack Overview:
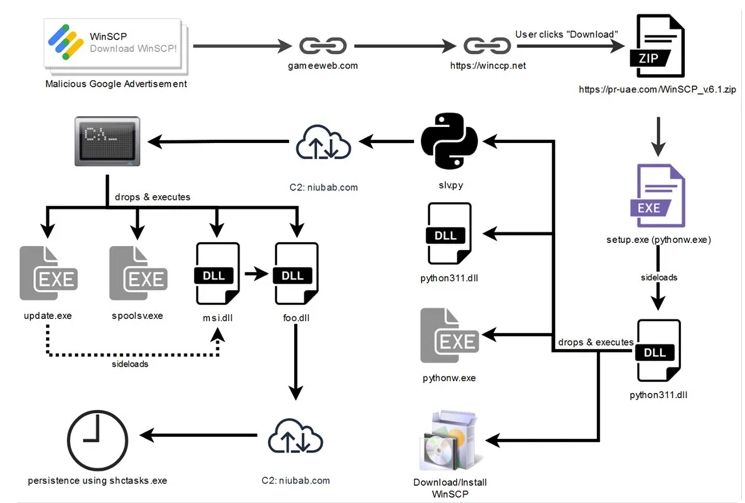
The malicious scheme begins with a manipulated advertisement directing users to a compromised WordPress website, gameeweb[.]com, which further redirects them to an attacker-controlled phishing site. The attackers are believed to leverage Google’s Dynamic Search Ads (DSAs) to automatically generate ads based on a site’s content, leading victims to the infected site.
Multi-Stage Attack Chain:
The ultimate goal of this complex attack is to entice users into downloading malware from a fake WinSCP website, winccp[.]net. The traffic redirection between gameeweb[.]com and winsccp[.]net relies on a correct referrer header. If incorrect, users are redirected to the famous Rick Astley YouTube video as a diversion.
Malicious Payload:
The final payload is delivered as a ZIP file (“WinSCP_v.6.1.zip”) containing a setup executable. When launched, the executable employs DLL side-loading to execute a DLL file named “python311.dll” found within the archive. While appearing to install WinSCP legitimately, this DLL secretly downloads and executes Python scripts (“slv.py” and “wo15.py”) in the background. These scripts activate malicious behavior and establish contact with a remote server controlled by the attackers, allowing them to run enumeration commands on the compromised host.
Geographical Targeting:
The researchers note that the geoblocking on the malware-hosting site suggests victims are primarily in the United States. Given that the attackers utilized Google Ads to distribute malware, it’s inferred that the targets are specifically individuals seeking WinSCP software.
History of Exploiting Dynamic Search Ads:
This is not the first instance of threat actors abusing Google’s Dynamic Search Ads for malware distribution. In a previous campaign, users searching for PyCharm were targeted with links to a compromised website hosting a rogue installer, leading to the deployment of information-stealing malware.
Rise of Malvertising:
Malvertising has gained popularity among cybercriminals in recent years, with various campaigns employing this tactic for attacks. Notably, recent reports by Malwarebytes highlight an increase in credit card skimming campaigns in October 2023, compromising hundreds of e-commerce websites to steal financial information through counterfeit payment pages.
Remediation Steps:
To safeguard against SEO#LURKER and similar malvertising campaigns, follow these remediation steps:
- Keep software up-to-date: Regularly update legitimate software to patch vulnerabilities.
- Exercise caution with ads: Be wary of ads, especially when downloading software. Use official websites or trusted sources.
- Employ reputable security software: Utilize reputable antivirus and anti-malware tools to detect and block malicious activities.
- Educate users: Raise awareness about the risks of malvertising and encourage safe online practices.
- Monitor network traffic: Keep an eye on unusual network activities and implement intrusion detection systems.
- Implement geoblocking: Consider geoblocking to restrict access to certain regions and mitigate potential risks.
- Report suspicious activities: Promptly report any suspicious ads or websites to relevant authorities and cybersecurity organizations.
Conclusion:
As malvertising continues to pose a significant threat, staying vigilant and implementing robust cybersecurity measures are crucial. By following these remediation steps, users and organizations can enhance their defenses against campaigns like SEO#LURKER and protect themselves from falling victim to malicious activities.