Delta Dental hit by MOVEit zero-day exploitation
The recent cyberattacks on dental insurance provider Delta Dental underscore the persistent and evolving threats organizations face in the digital landscape. In the first incident, Delta Dental became a victim of the MOVEit Transfer zero-day flaw exploitation campaign orchestrated by the Cl0p ransomware group. The attackers accessed and obtained sensitive information, affecting almost seven million customers. The second incident involved Delta Dental of California, which suffered a data breach due to unauthorized access through the MOVEit file transfer software. This breach impacted 6,928,932 individuals, exposing a range of personal details.
Key Incident & How it happened:
Delta Dental of California and its affiliates, covering 45 million people across 15 states fell victim to the MOVEit Transfer zero-day flaw exploitation campaign, orchestrated by the Russia-linked ransomware group Cl0p and also suffered a data breach due to unauthorized access through the MOVEit file transfer software application.
The hackers accessed and acquired private information, including driver’s licenses and passport numbers, of nearly seven million Delta Dental customers. The breach occurred on the MOVEit platform between May 27th and May 30th. The MOVEit software was vulnerable to a zero-day SQL injection flaw (CVE-2023-34362), leading to remote code execution. The Clop ransomware gang leveraged this vulnerability to breach Delta Dental of California.
Consequences:
Delta Dental discovered the compromise on June 1, 2023, confirming unauthorized access and data theft between May 27 and May 30, 2023. The leaked information, affecting 6,928,932 individuals, included a range of sensitive details such as names, addresses, Social Security numbers, driver’s license numbers, passport numbers, financial account information, and health-related data. The attackers also obtained credit card or account numbers along with security codes, access codes, passwords, or PINs. Delta Dental took prompt action, stopping access to MOVEit, removing malicious files, and enhancing security measures. The company provides 24 months of free credit monitoring and identity theft protection to affected individuals.
Legal Ramifications & Security Measures:
Progress Software, the vendor behind MOVEit, is facing legal challenges with at least 13 lawsuits alleging inadequate security leading to the MOVEit flaw. Emsisoft warns of the potential misuse of stolen information and emphasizes the global threat it poses in various cybercrimes.
Progress Software fixed the vulnerability on May 31, preventing further intrusions. However, experts caution that the full extent of the MOVEit data breaches is yet to be determined, with ongoing investigations expected to reveal additional victims in the coming weeks.
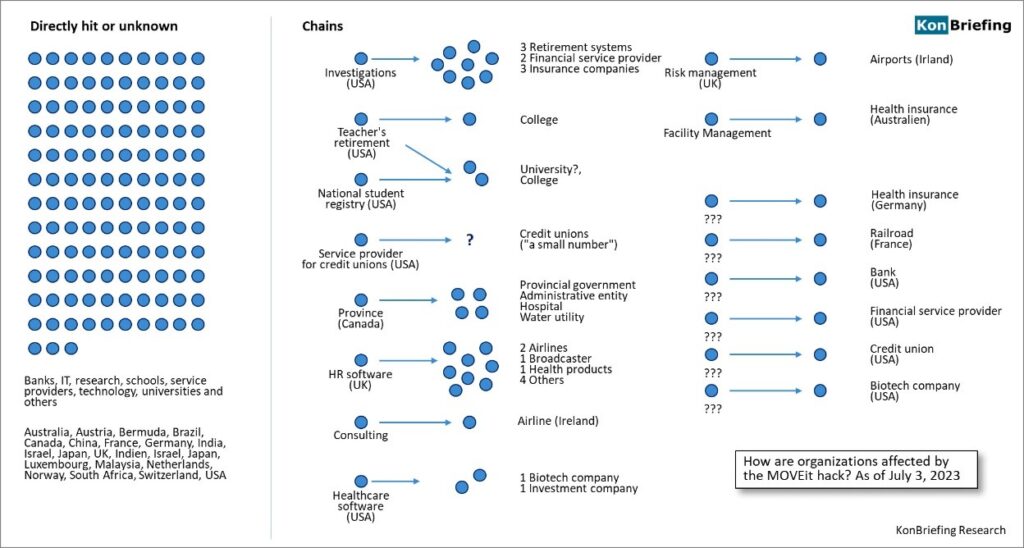
MOVEit’s other victims
Other Victims of MOVEit breach:
The MOVEit Transfer zero-day flaw exploitation campaign has affected a range of organizations, both directly and indirectly. Notable victims include:
- Direct Impact on Zellis: UK-based Zellis, a payroll and HR firm, suffered a direct impact.
- Indirect Impact on Major Organizations: Large organizations relying on Zellis’ services, including BBC, British Airways, the US Department of Energy, Shell, Deutsche Bank, PwC, TJX Companies, and more, experienced indirect harm.
- Other Impacted Entities: Additional impacted entities include Marshalls, HomeGoods, HomeSense, Sierra (owned by TJX), Emerson, Siemens Energy, Schneider Electric, Netscout, several German banks, Shutterfly, and Honeywell.
Number of Individuals Affected-
The personal information, mainly Social Security numbers, of numerous individuals has been compromised. Victims include:
- Fidelity & Guaranty Life Insurance Co.: 873,000 victims
- 1st Source Bank (Indiana): 450,000 victims
- Franklin Mint Federal Credit Union (Pennsylvania): 141,000 victims
- PokerStars (TSG Interactive US Services Limited): 110,291 victims
- Athene Annuity and Life Company (Iowa): 70,412 victims
- Massachusetts Mutual Life Co. (MassMutual): 242 victims
Recommendations/Remedies:
Both incidents highlight the need for organizations to prioritize cybersecurity measures, including prompt vulnerability patching, robust threat detection, and comprehensive incident response strategies to safeguard sensitive data and protect individuals from the consequences of such breaches.
- Enhanced Cybersecurity Measures:Implement robust cybersecurity protocols, including advanced threat detection systems, firewalls, and intrusion prevention systems to identify and block malicious activities.
- Employee Training and Awareness:Conduct regular training sessions to educate employees on cybersecurity best practices, with a specific focus on recognizing and avoiding phishing attempts.
- Multi-Factor Authentication (MFA):Enforce multi-factor authentication for access to critical systems and accounts, adding an extra layer of security to prevent unauthorized access.
- Regular Security Audits and Assessments:Conduct frequent security audits and assessments to identify vulnerabilities in systems and networks. Regular testing helps ensure that security measures are effective and up to date.



