Critical MyFlaw Bug in Opera Browser Poses Severe Threat: Allows Hackers to Execute Any File on Mac or Windows Systems
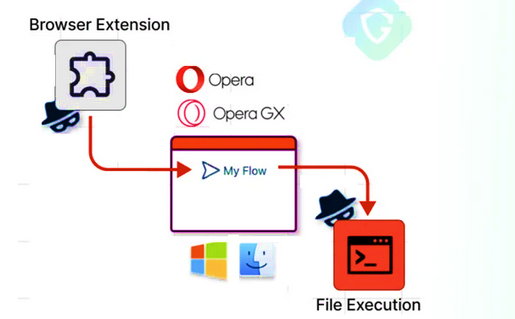
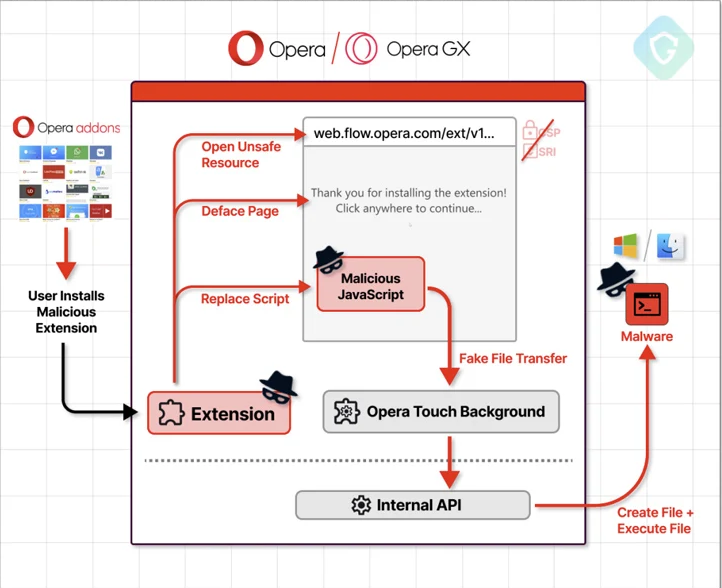
In a recent revelation, cybersecurity researchers from Guardio Labs exposed a critical security flaw in the Opera web browser, affecting both Microsoft Windows and Apple macOS platforms. Dubbed “MyFlaw,” the vulnerability exploited a feature known as My Flow, enabling the execution of arbitrary files on the underlying operating system. This flaw, now patched, bypassed the browser’s sandbox through a controlled extension, allowing remote code execution.
Technical Details:
- Vulnerability Name: Opera MyFlaw Bug
- Affected Systems: Opera Browser on Mac and Windows Platforms
- Impact: Potential unauthorized execution of files, leading to system compromise and data breaches.
- Severity: High
My Flow and the Exploited Feature:
At the core of the vulnerability is the My Flow feature, designed to synchronize messages and files between mobile and desktop devices. The flaw leveraged a browser extension called “Opera Touch Background,” responsible for communication with its mobile counterpart. This internal extension facilitated the flaw by operating beyond the browser’s security boundaries.
Manifest File and Permissions:
The extension came with its manifest file, outlining permissions and behavior, including the crucial “externally_connectable” property. This property declared which web pages and extensions could connect to it, posing a security risk if exploited.
Domain Patterns and Exposure:
The flaw exposed the messaging API to any page matching specified URL patterns, controlled by the browser vendor. The domains “*.flow.opera.com” and “.flow.op-test.net” were authorized, emphasizing the critical role of proper domain controls in preventing unauthorized access.
Discovery of the Forgotten My Flow Landing Page:
Guardio Labs unearthed a forgotten version of the My Flow landing page hosted on “web.flow.opera.com” using the urlscan.io website scanner tool. This version lacked essential security measures, such as the content security policy meta tag, making it susceptible to code injection.
Attack Chain and Exploitation:
The attack chain involved crafting a malicious extension masquerading as a mobile device to pair with the victim’s computer. The encrypted malicious payload, transmitted via a modified JavaScript file, prompted user interaction for execution. This sophisticated technique highlighted the multifaceted nature of browser-based attacks.
Implications and Browser Security Measures:
Despite operating in sandboxed environments, browser extensions can be potent tools for hackers, breaching security boundaries. Guardio Labs emphasized the need for internal design changes at Opera and improvements in Chromium’s infrastructure. Suggestions included disabling third-party extension permissions on dedicated production domains, akin to Chrome’s web store.
Opera’s Response:
Upon responsible disclosure on November 17, 2023, Opera promptly addressed the vulnerability in updates released on November 22, 2023. The company acknowledged the collaboration with Guardio Labs and affirmed its commitment to maintaining and enhancing product security.
Remediation Steps:
To address the Opera MyFlaw Bug, the following remediation steps should be taken:
- Ensure that Opera is updated to the latest version, as updates often include patches for known vulnerabilities.
- Regularly check and manage browser extensions. Remove any unfamiliar or unnecessary extensions.
- Use robust antivirus and anti-malware software, and keep them updated to detect and prevent malicious activities.
- Inform users about the risk of this bug and the importance of security practices like not downloading files from unknown sources.
- Conduct routine security audits of your systems to check for vulnerabilities and ensure all software is up to date.
- Regularly back up important data to mitigate the impact in case of a compromise.