Exploiting Wireless Chargers: Voice Command Injection and Device Damage by VoltSchemer Attacks
In a world increasingly reliant on smartphones and wireless technology, ensuring the security of our devices is paramount. However, a recent discovery by a team of academic researchers from the University of Florida and CertiK has unveiled a concerning vulnerability that threatens the integrity of our smartphones: VoltSchemer.
What is VoltSchemer?
It’s a sophisticated attack vector that leverages electromagnetic interference to manipulate smartphones through the magnetic field emitted by off-the-shelf wireless chargers. This revelation sheds light on a previously unrecognized threat lurking in the seemingly innocuous realm of wireless charging technology.
At its core, VoltSchemer operates by injecting voice commands into a smartphone’s voice assistant, exploiting the electromagnetic fields generated by wireless chargers. This means that attackers could potentially hijack your smartphone, issuing commands and wreaking havoc without your knowledge or consent.
But the implications of VoltSchemer extend beyond mere manipulation. Shockingly, this attack can also inflict physical harm, raising temperatures to dangerous levels and causing damage to both the device itself and nearby items. Imagine your smartphone overheating to the point of physical damage, or nearby objects being heated to temperatures high enough to cause them to ignite. It’s a chilling thought, to say the least.
So, how does VoltSchemer work its nefarious magic?
Essentially, it takes advantage of vulnerabilities in the hardware design of wireless charging systems and the protocols governing their communication. By manipulating the voltage supplied to the charger, attackers can distort the magnetic fields emitted during charging, disrupting data exchange and enabling the injection of malicious commands.
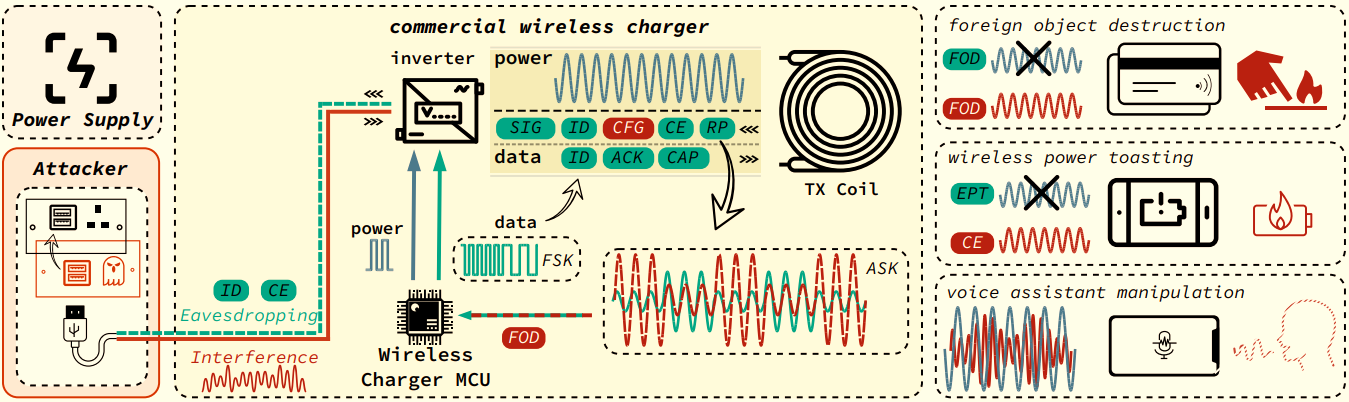
The implications of VoltSchemer are far-reaching and deeply concerning. From the risk of overheating and overcharging to the potential for bypassing safety standards and injecting voice commands, the threat posed by this attack is significant. Moreover, its discovery underscores the need for greater vigilance and scrutiny when it comes to the security of IoT devices and wireless technologies.
In response to this discovery, the researchers have shared their findings with the vendors of the tested charging stations, advocating for improved designs and countermeasures to mitigate the risk of VoltSchemer attacks. However, the onus is on all stakeholders – from manufacturers and developers to consumers – to remain vigilant and proactive in safeguarding against emerging threats like VoltSchemer.
As we continue to embrace the convenience and connectivity afforded by wireless technologies, let us not forget the importance of security. The discovery of VoltSchemer serves as a stark reminder that with innovation comes the potential for exploitation. It’s up to us to stay one step ahead, ensuring that our devices remain secure in an increasingly interconnected world.
Remediation:
Now that the threat of VoltSchemer has been brought to light, it’s crucial to take proactive steps to safeguard your smartphone against potential attacks. While the discovery of VoltSchemer is concerning, there are several measures you can take to mitigate the risk and enhance the security of your device.
- Use Trusted Charging Accessories: Stick to using charging accessories from reputable manufacturers and vendors. Avoid purchasing cheap or counterfeit chargers, as they may lack the necessary security measures to protect against VoltSchemer and other potential attacks. Investing in high-quality, certified chargers can help minimize the risk of exploitation.
- Monitor Device Temperature: Keep an eye on your smartphone’s temperature while it’s charging. If you notice any abnormal heating or overheating, immediately disconnect the device from the charger and investigate the cause. Overheating can be a sign of VoltSchemer or other malicious activity, so vigilance is key to preventing potential damage or security breaches.
- Implement Voice Assistant Security Measures: Take precautions to secure your smartphone’s voice assistant functionality. Consider enabling voice recognition or biometric authentication to prevent unauthorized access to voice commands. Additionally, review and adjust your device’s voice assistant settings to limit access and functionality, reducing the likelihood of exploitation by VoltSchemer or similar attacks.
- Update Firmware and Software: Ensure that both your smartphone’s firmware and software are up-to-date. Manufacturers often release security patches and updates to address vulnerabilities and enhance device security. Regularly check for updates and install them promptly to keep your device protected against emerging threats like VoltSchemer.
- Report Suspicious Activity: If you suspect that your smartphone has been compromised or if you encounter any suspicious activity while using wireless chargers or voice assistants, report it to the appropriate authorities or device manufacturer immediately.



