Migo Malware Targets Redis Servers for Cryptocurrency Mining
Cado Security has uncovered a concerning new malware campaign, dubbed Migo, which specifically targets Redis servers to gain unauthorized access, aiming to exploit compromised Linux hosts for cryptocurrency mining. This sophisticated malware employs advanced techniques to infiltrate systems and evade detection, marking a significant development in the realm of cyber threats within cloud environments. The emergence of Migo underscores the ever-evolving tactics employed by threat actors to exploit vulnerabilities in cloud infrastructure for illicit gain. This discovery highlights the critical need for robust cybersecurity measures to protect against such targeted attacks and safeguard sensitive data and resources hosted on cloud platforms.
Understanding the Migo Malware Campaign Targeting Redis Servers
Recent observations reveal the emergence of a novel malware campaign dubbed Migo, which specifically targets Redis servers as a gateway for initial access, aiming to exploit compromised Linux hosts for cryptocurrency mining purposes. This campaign utilizes advanced evasion tactics and persistence mechanisms to fly under the radar of detection systems, indicating a high level of sophistication by the threat actors involved. The targeting of Redis servers underscores the strategic focus on exploiting widely-used infrastructure components for illicit gain, highlighting the evolving nature of cyber threats. This development underscores the importance of robust security measures and proactive defense strategies to mitigate the risk posed by such malicious campaigns and protect critical systems and data from exploitation.
Redis Server Exploitation: Initial Access and Exploitation
The Migo campaign initiates its attack by exploiting Redis servers through a series of ingenious system weakening techniques. Cado Security researcher Matt Muir underscores the deployment of unconventional methods aimed at disabling vital configuration options, such as protected-mode, replica-read-only, aof-rewrite-incremental-fsync, and rdb-save-incremental-fsync. These strategic maneuvers serve as a precursor to executing supplementary commands, thereby enabling future exploitation while circumventing security defenses. By leveraging these innovative tactics, threat actors can stealthily gain a foothold within target environments, underscoring the sophistication and adaptability of modern cyber threats. This highlights the imperative for organizations to remain vigilant and implement robust defensive measures to thwart such malicious activities effectively.
Payload Delivery and Execution
Following the initial breach, threat actors proceed by deploying two distinct Redis keys: one directed towards an SSH key under their control, and the other configured to trigger a cron job responsible for fetching the primary malicious payload from Transfer.sh, a well-known file transfer service. This strategic maneuver, reminiscent of tactics observed as early as 2023, underscores the adversaries’ adeptness in repurposing proven methods to suit their objectives. At the core of this campaign lies Migo, a sophisticated Golang ELF binary meticulously crafted with compile-time obfuscation and persistence mechanisms. These features ensure Migo’s enduring presence on compromised Linux systems, amplifying the threat posed by the malware. The seamless integration of diverse techniques highlights the adversaries’ proficiency in orchestrating multifaceted attacks, emphasizing the urgency for organizations to fortify their cybersecurity posture with robust defensive measures. The evolving nature of such threats underscores the imperative for continual vigilance and proactive defense strategies to effectively mitigate the risks associated with sophisticated cyber campaigns.
Functionalities of Migo Malware
Functioning as a downloader, Migo retrieves an XMRig installer from GitHub, facilitating the installation and operation of cryptocurrency mining software on compromised hosts. This enables threat actors to exploit the computational resources of compromised systems for mining purposes. Migo incorporates multiple anti-reverse engineering techniques, enhancing its resilience against analysis and detection by security researchers. Furthermore, the malware actively terminates competing miners present on the infected machines, ensuring its undisputed control over the mining operation. This comprehensive approach demonstrates the sophistication and determination of the threat actors behind the Migo campaign, underscoring the evolving nature of cyber threats targeting cryptocurrency resources. It emphasizes the critical importance of robust cybersecurity measures to detect, mitigate, and prevent such malicious activities from compromising organizational assets.
Persistence and Evasion Techniques
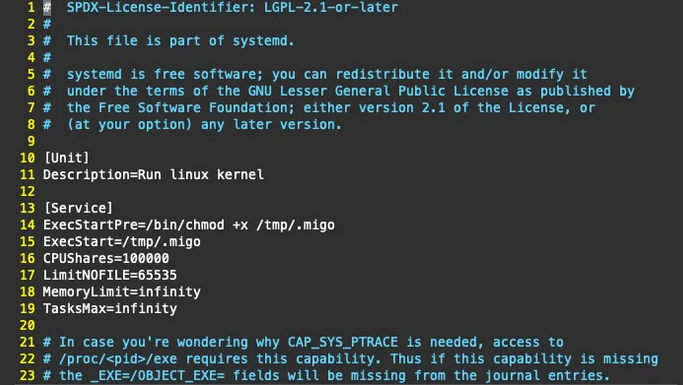
Migo surpasses mere payload delivery by integrating functionalities to secure persistence, eliminate rival miners, and conduct cryptocurrency mining operations seamlessly. A notable aspect of its operations involves the disabling of Security-Enhanced Linux (SELinux) and the pursuit of uninstallation scripts designed for monitoring agents typically bundled within cloud provider compute instances. Additionally, Migo incorporates a customized iteration of the widely-used user-mode rootkit, libprocesshider, strategically concealing both its processes and on-disk artifacts to bolster its stealth capabilities. This comprehensive approach underscores the malware’s sophistication, illustrating the adversaries’ meticulous efforts to evade detection and maintain control over compromised systems. It underscores the pressing need for organizations to bolster their cybersecurity defenses and remain vigilant against evolving threats in the digital landscape.
Analysis and Hypotheses
The malware demonstrates a distinctive behavior of recursively traversing through files and directories within the /etc directory, potentially as a tactic to obscure its malicious operations. This activity may serve multiple purposes, including the deliberate obfuscation of its actions to evade detection by sandbox and dynamic analysis solutions. Additionally, it could be an attempt to identify and exploit specific artifacts unique to the target environment, thereby enhancing its effectiveness in compromising the system. By employing such techniques, the malware showcases a sophisticated understanding of evasion tactics, highlighting the adversaries’ intention to operate undetected and maximize their impact. This underscores the critical importance of robust cybersecurity measures and proactive threat hunting strategies to effectively combat evolving threats in today’s digital landscape.
Advanced Tactics and Future Implications
Migo’s tactics resonate with those employed by prominent cryptojacking groups like TeamTNT, WatchDog, Rocke, and threat actors linked to the SkidMap malware. Remarkably, Migo employs a strategy akin to these groups, utilizing recursive iterations through files and directories within the /etc directory. This technique serves dual purposes: first, it may function as a means of obfuscating the malware’s malicious intent, aiming to evade detection by security measures, including sandboxing and dynamic analysis solutions. Second, it could potentially serve as an attempt to locate environment-specific artifacts that could aid in further compromising the system. Despite these observations, Cado’s exhaustive investigation yielded no definitive evidence to support the latter hypothesis. This highlights the complexity of Migo’s behavior and the challenges inherent in deciphering the motivations behind its actions. The alignment of Migo’s tactics with those of established cryptojacking groups underscores the evolving nature of cyber threats and the need for continual adaptation and enhancement of cybersecurity defenses. Organizations must remain vigilant and proactive in their efforts to detect, mitigate, and prevent such sophisticated threats from compromising their systems and data.
Remediation Steps
- Implement Proper Access Controls: Ensure that Redis servers are configured securely with proper access controls to prevent unauthorized access and configuration changes.
- Enable Security Features: Enable security features such as SELinux and regularly update monitoring agents to detect and prevent malicious activities.
- Monitor Network Traffic: Monitor network traffic for unusual activity targeting Redis servers, including unexpected command sequences or attempts to disable critical configuration options.
- Limit Outbound Connections: Restrict outbound connections from Redis servers to trusted sources and block access to suspicious file transfer services.
- Enhance Endpoint Security: Deploy endpoint security solutions capable of detecting and blocking malware like Migo, and regularly update antivirus definitions.
- Implement File Integrity Monitoring: Implement file integrity monitoring to detect unauthorized changes to critical system files and directories, including those under /etc.
- Educate Personnel: Educate personnel on recognizing phishing attempts and suspicious activity to prevent initial access to Redis servers and other critical infrastructure components.



