Malware Distribution via Fake Zoom, Skype, and Google Meet Websites
A threat actor has initiated a deceptive campaign involving counterfeit Skype, Google Meet, and Zoom meetings, aiming to distribute malware that targets both Android and Windows users. Beginning in December, this campaign poses a significant cybersecurity risk to corporate users, as revealed by researchers from Zcaler’s ThreatLabz in a blog post dated March 6. The attackers are utilizing shared web hosting to host fake online meeting platforms on a single IP address. These platforms employ URLs that closely resemble the legitimate websites of the targeted services. For example, the Skype campaign directs users to “join-skype[.]info,” while the Google Meet variant entices participants with “online-cloudmeeting[.]pro.” Similarly, the Zoom campaign leverages the URL “us06webzoomus[.]pro.
The spoofed sites are in Russian and are hosted on domains that closely resemble their legitimate counterparts, indicating that the attackers are using typosquatting tricks to lure prospective victims into downloading the malware. They offer app downloads for Android, iOS, and Windows platforms, each with its respective button. Clicking the Android button initiates the download of an APK file, while clicking the Windows app button triggers the download of a batch script. The malicious batch script triggers the execution of a PowerShell script, which then downloads and runs the remote access trojan. There’s no indication that iOS users are being specifically targeted, as clicking the iOS app button redirects users to the legitimate Apple App Store listing for Skype. The AhnLab Security Intelligence Center (ASEC) has uncovered a new threat named WogRAT, capable of targeting Windows and Linux systems. This malware exploits the free online notepad platform ‘aNotepad’ to clandestinely host and fetch malicious code. Upon initial execution, WogRAT gathers essential system details and transmits them to the command and control (C&C) server. The malware facilitates various commands, including executing instructions, transmitting outcomes, fetching files, and uploading data.
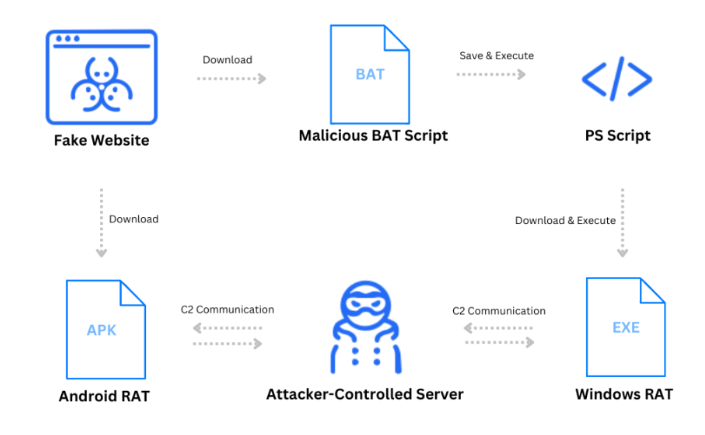
When a user lands on any of these counterfeit websites, selecting the Android option prompts the download of a malicious APK file, while choosing the Windows option triggers the download of a BAT file. Once executed, the BAT file initiates further actions, culminating in the installation of a RAT payload.
Zoom
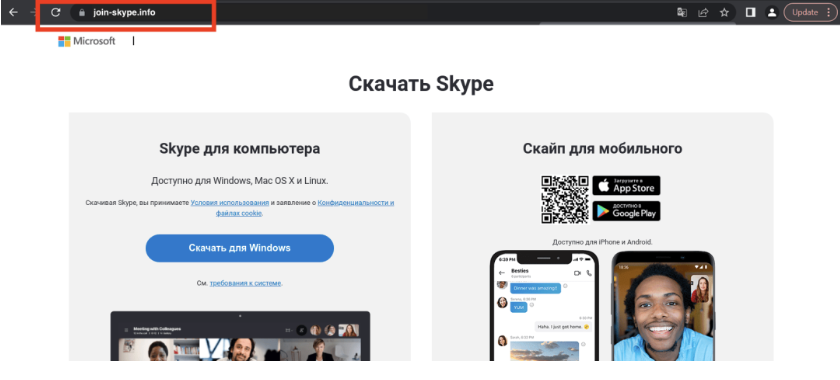
Researchers found that the initial fraudulent website, join-skype[.]info, came into existence in early December with the aim of tricking users into downloading a counterfeit Skype application. Clicking the Windows button led to a file named Skype8.exe, while the Google Play button directed to Skype.apk (both files were unavailable during analysis). The Apple App Store button redirected users to https://go.skype.com/skype.download.for.phone.iphone, suggesting that iOS users were not being targeted with malware.
Google Meet
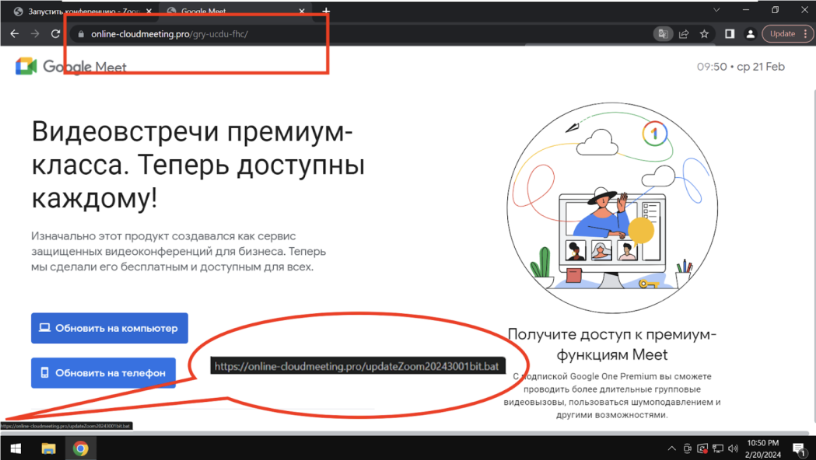
In late December, the perpetrator established yet another fraudulent website, online-cloudmeeting[.]pro, posing as Google Meet. The counterfeit Google Meet site was hosted on online-cloudmeeting[.]pro/gry-ucdu-fhc/, with the subpath gry-ucdu-fhc deliberately crafted to mimic a genuine Google Meet joining link. Legitimate Google Meet invite codes typically adhere to the pattern [a-z]{3}-[a-z]{4}-[a-z]{3}.
The deceptive site offers download links for a counterfeit Skype application for both Android and Windows platforms. Clicking on the Windows link directs users to a BAT file named updateZoom20243001bit.bat, which subsequently fetches the final payload ZoomDirectUpdate.exe. This ultimate payload is a WinRAR archive containing DCRat, concealed with Eziriz .NET Reactor.
Zoom
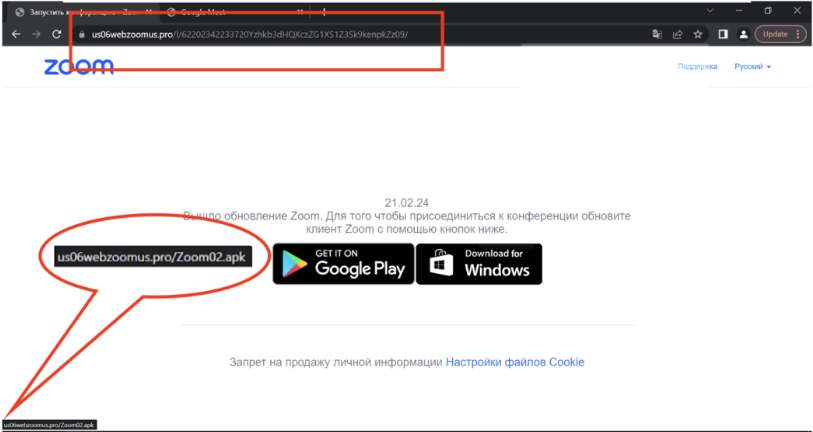
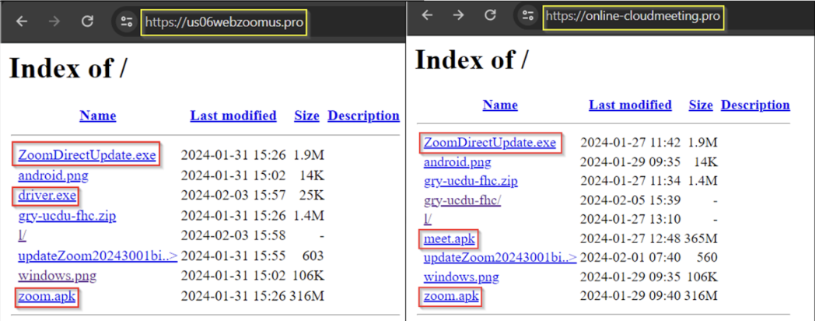
In late January, researchers from Zscaler uncovered a fraudulent Zoom website, us06webzoomus[.]pro, as depicted in Figure 4. This deceptive site, residing at the URL us06webzoomus[.]pro/l/62202342233720Yzhkb3dHQXczZG1XS1Z3Sk9kenpkZz09/, mimics a Zoom meeting ID. If users opt for the Google Play link, they unwittingly download a file named Zoom02.apk containing the SpyNote RAT. Similarly, selecting the Windows option triggers the download of a BAT file, leading to the installation of a DCRat payload.
In addition to hosting DCRat the counterfeit Google Meet and Zoom platforms feature an accessible directory (illustrated in Figure 5) containing two supplementary Windows executable files named driver.exe and meet.exe (enclosed in the archive gry-ucdu-fhc.zip), both identified as NjRAT. The inclusion of these files hints at the attacker’s potential use in future campaigns, owing to their specific designations.
Recommendations
- Educate users about the risks of downloading files from untrusted sources and emphasize the importance of verifying the legitimacy of websites before downloading any files.
- Implement web filtering solutions that can detect and block access to known malicious websites hosting malware payloads.
- Ensure that all systems have up-to-date antivirus and anti-malware software installed to detect and remove malicious files.
- Keep operating systems and software up-to-date with the latest security patches to mitigate vulnerabilities that malware may exploit.
- Employ security solutions capable of detecting unusual behaviour such as XDR,EDR etc indicative of malware activities like unexpected file downloads or execution of suspicious files.
- Maintain regular backups of critical data to ensure that data can be restored in the event of a successful malware attack.



