Cisco Secure Client Vulnerability: CVE-2024-20337
In the realm of cybersecurity, vigilance is paramount. Recently, a critical vulnerability was discovered in Cisco Secure Client, a widely used VPN solution. This flaw, tracked as CVE-2024-20337, poses a significant risk to organizations relying on VPNs for secure communication.
Exploitation code for a significant vulnerability in Cisco Secure Client Software for Windows, known as CVE-2023-20178, is now accessible in the form of a proof-of-concept. This flaw allows authenticated attackers to elevate privileges to the SYSTEM account without user interaction, exploiting a specific function of the Windows installer process. Cisco has promptly addressed this issue with security updates, including fixes in the latest releases of AnyConnect Secure Mobility Client for Windows (version 4.10MR7) and Cisco Secure Client for Windows (version 5.0MR2). Although there is currently no evidence of malicious exploitation or publicly available exploit code, users are advised to apply the updates promptly for enhanced security.
Networking giant Cisco recently patched a high-severity flaw in its Secure Client software. This vulnerability could be exploited by threat actors to open a VPN session with a targeted endpoint. Let’s dive into the details.
This week, a security researcher, disclosed proof-of-concept (PoC) exploit code for an Arbitrary File Delete vulnerability that was discovered and reported to Cisco. Dragović tested the PoC against Cisco Secure Client (version 5.0.01242) and Cisco AnyConnect (version 4.10.06079).
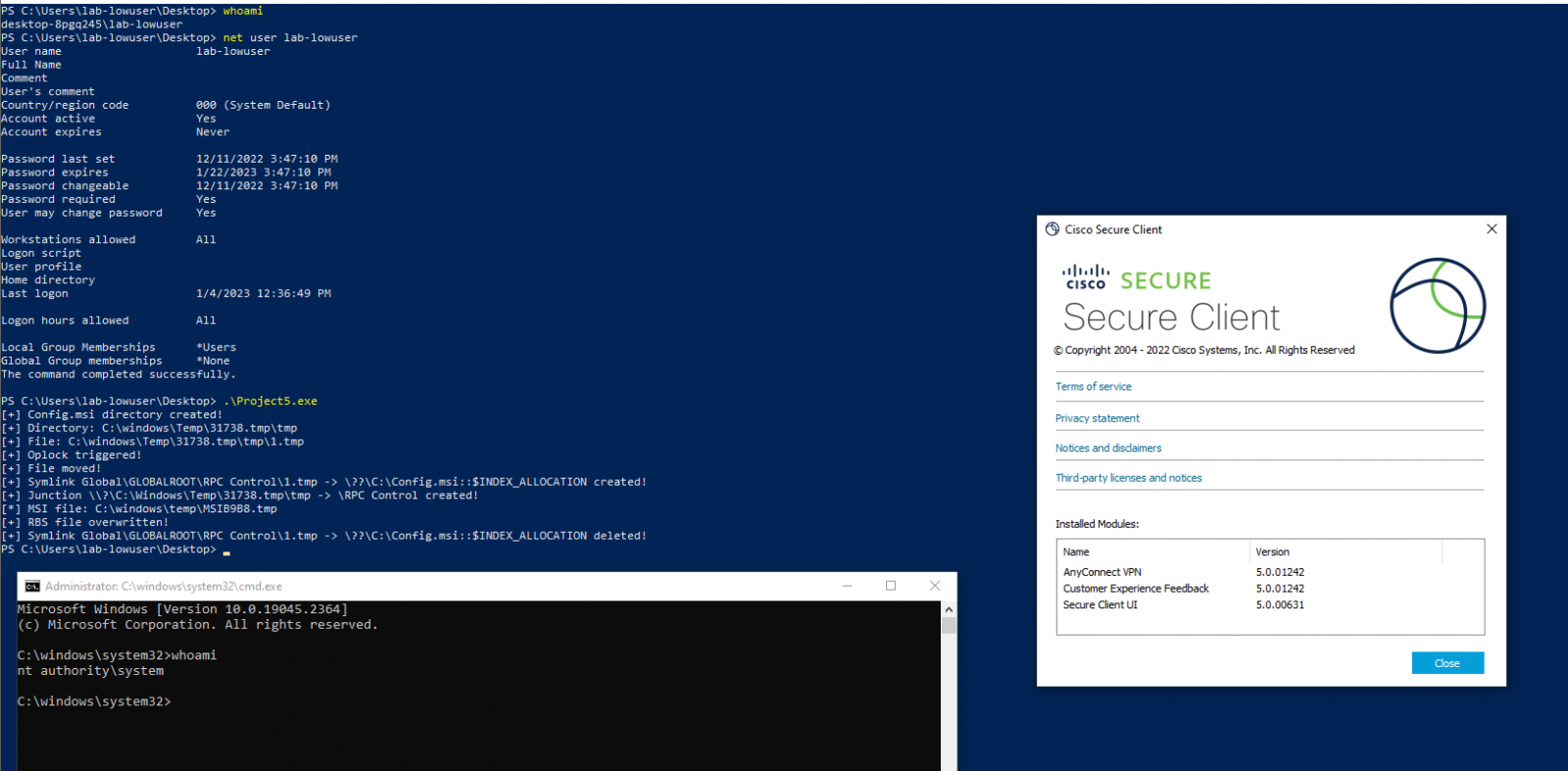
Explaining the exploit, Dragović outlined that when a user connects to the VPN, the vpndownloader.exe process initiates in the background, creating a directory in c:\windows\temp with default permissions in the format of <random numbers>.tmp. Subsequently, vpndownloader.exe checks if the directory is empty, and if not, it deletes all files/directories within. This behavior can be manipulated to execute arbitrary file deletion under the NT Authority\SYSTEM account.
Exploiting this, an attacker can spawn a SYSTEM shell through arbitrary file deletion by capitalizing on the Windows installer behavior. Additionally, the client update process, executed after each successful VPN connection, provides an avenue for privilege escalation using the described technique.
Digging Deep into the Vulnerability
- Vulnerability Name: Carriage Return Line Feed Injection (CVE-2024-20337)
- Severity Score: 8.2 (high severity)
- Description: The flaw allows an unauthenticated attacker to perform a carriage return line feed (CRLF) injection on the target endpoint remotely.
- Exploit Scenario: By persuading a user to click a crafted link during VPN session establishment, an attacker can execute arbitrary script code in the victim’s browser.
- Impact: The attacker could then use the compromised session to establish a remote access VPN session with the privileges of the affected user. However, additional credentials would still be required for accessing individual hosts and services behind the VPN headend.
Technical Analysis
Vulnerability Details
- CVE ID: CVE-2024-20337
- Vulnerability Type: Carriage Return Line Feed Injection (CRLF)
- Affected Product: Cisco Secure Client
- Severity Score: 8.2 (high severity)
Understanding the Vulnerability
The vulnerability arises from insufficient validation of user-supplied input during VPN session establishment. Let’s break down the technical aspects:
- Attack Vector: An unauthenticated attacker crafts a malicious link.
- Social Engineering: The attacker persuades a user to click the crafted link while setting up a VPN session.
- CRLF Injection: By injecting carriage return line feed characters into the session, the attacker manipulates the communication flow.
- Browser Script Execution: The victim’s browser executes arbitrary script code embedded in the manipulated session.
- Session Compromise: The attacker gains control over the compromised session.
How It Works
- Insufficient Validation: The vulnerability arises from insufficient validation of user-supplied input.
- Crafted Links: Hackers can trick victims into clicking custom-tailored links while setting up a VPN session.
- Local Network Access: Once successful, threat actors gain access to the target’s local internal networks.




