GhostRace: A Fresh Data Leakage Vulnerability Impacting Contemporary CPUs
In the dynamic realm of cybersecurity threats, a recent discovery has shed light on a new avenue for data leakage, identified as GhostRace (CVE-2024-2193). This exploit marks a significant evolution of the notorious Spectre v1 vulnerability (CVE-2017-5753), leveraging a combination of speculative execution and race conditions to infiltrate system defenses. GhostRace represents a sophisticated approach, intertwining aspects of speculative execution, where a processor predicts and executes instructions ahead of time, with race conditions, exploiting timing discrepancies in concurrent processes. Through this fusion, attackers can manipulate speculative execution to access sensitive data, breaching system security. Unlike traditional exploits, GhostRace operates in a manner that eludes conventional detection methods, posing a formidable challenge for cybersecurity experts. As researchers delve deeper into its mechanisms, the urgency to develop effective countermeasures intensifies, highlighting the ongoing cat-and-mouse game between cyber attackers and defenders in the ever-evolving landscape of digital security.
Understanding GhostRace:
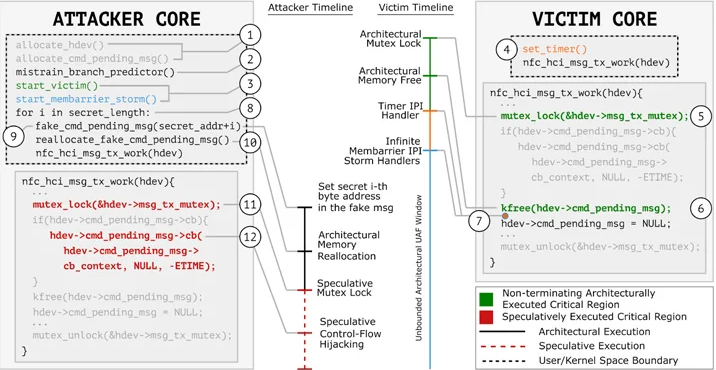
GhostRace exploits the convergence of speculative execution and race conditions, giving rise to a phenomenon termed Speculative Race Conditions (SRCs). Through the utilization of branch misprediction attacks, GhostRace effectively converts traditionally race-free critical regions into susceptible areas, thereby granting attackers the ability to extract sensitive data from the targeted system. This technique underscores the sophistication of GhostRace, as it manipulates the intricate interplay between speculative execution and race conditions to compromise system security. By exploiting SRCs, attackers can exploit timing discrepancies in concurrent processes, exploiting transient execution pathways to their advantage. This novel approach poses a significant challenge for cybersecurity defenses, as it introduces a new avenue for potential exploitation within modern CPU architectures. As security researchers work to understand and address the implications of GhostRace, there is a growing imperative for the development of robust mitigation strategies to safeguard against speculative race conditions and their associated risks.
The Inner Workings:
GhostRace fundamentally exploits the inherent characteristics of speculative execution, coaxing the CPU into executing operations that would not typically arise during strictly serialized processing. By employing a Speculative Concurrent Use-After-Free (SCUAF) attack, GhostRace facilitates unauthorized access for adversaries to speculative executable code paths, enabling them to extract arbitrary data from the processor. This tactic capitalizes on the CPU’s predictive nature, which anticipates and executes instructions ahead of confirmation, often leading to temporary data exposure. Through GhostRace’s manipulation of speculative execution, malicious actors can exploit these transient pathways to their advantage, potentially compromising sensitive information. This technique represents a significant challenge for cybersecurity defenses, as it operates within the processor’s architecture, making detection and mitigation complex tasks. As the cybersecurity community grapples with GhostRace’s implications, there’s a pressing need for innovative solutions to mitigate the risks posed by speculative execution vulnerabilities.
Race Conditions and Vulnerability:
A race condition materializes when multiple processes contend for entry to a shared resource without adequate synchronization, resulting in discrepancies and offering an opportunity for malicious exploitation. In the context of GhostRace, the assault manifests on momentarily executed pathways stemming from misjudged branches, reminiscent of the Spectre v1 vulnerability. This scenario creates a scenario where speculative execution, a fundamental aspect of modern processors optimizing performance by executing instructions ahead of time, becomes a potential vector for exploitation. GhostRace leverages this vulnerability by manipulating speculative execution to access sensitive data, breaching system security. Unlike traditional exploits, GhostRace operates in a manner that evades typical detection mechanisms, posing a formidable challenge for cybersecurity professionals. As researchers delve deeper into its intricacies, the urgency to devise effective countermeasures intensifies, highlighting the ongoing cat-and-mouse game between cyber attackers and defenders in the constantly evolving landscape of digital security.
Implications and Mitigations:
The emergence of GhostRace presents considerable dangers for software relying on conditional branches for synchronization when lacking sufficient serialization instructions. While all microarchitectures face vulnerability, employing mitigation strategies akin to those used for Spectre vulnerabilities proves effective. AMD has reiterated its existing guidance, underscoring the importance of implementing protective measures against GhostRace. Meanwhile, the Xen open-source hypervisor has swiftly taken action by integrating robust patches aimed at fortifying system defenses and mitigating potential risks. These developments highlight the urgent need for proactive measures within the cybersecurity realm to combat evolving threats like GhostRace. As organizations navigate the complexities of safeguarding their digital infrastructures, collaborative efforts and the dissemination of best practices become pivotal in thwarting such sophisticated
- Patch Systems Promptly: Stay updated with the latest security patches from CPU vendors, as they often include fixes for speculative execution vulnerabilities like GhostRace.
- Apply Microcode Updates: Ensure CPUs are running the latest microcode updates to address underlying vulnerabilities.
- Enable Hardware Mitigations: Leverage hardware-level mitigations offered by CPU vendors to bolster defense against speculative execution attacks.
- Employ Compiler-Level Protections: Utilize compiler features like retpoline and speculation barrier to mitigate the risk of speculative execution attacks.
- Implement Software Hardening: Enhance software defenses by implementing serialization instructions in critical code paths to prevent speculative execution.
- Monitor and Detect Anomalies: Deploy intrusion detection systems (IDS) and anomaly detection mechanisms to identify suspicious behavior indicative of GhostRace exploitation.
- Educate Users and Administrators: Raise awareness among users and system administrators about the risks posed by GhostRace and the importance of following security best practices.



