Cyberattack Targets Indian Defense and Energy Sectors with Malware Disguised as Air Force Invitation
Recent events have witnessed a wave of sophisticated cyber espionage targeting Indian government entities and energy companies. Perpetrated by unidentified threat actors, these entities have fallen victim to a tailored assault employing a variant of the HackBrowserData malware, originally an open-source information stealer. What sets this attack apart is the novel use of Slack, a widely used communication platform, as a command-and-control (C2) channel, adding a layer of complexity to the operation. This campaign, marked by its intricacy, underscores the evolving tactics employed by cyber adversaries to infiltrate high-value targets. The modified malware, equipped with advanced features, has enabled threat actors to exfiltrate sensitive data covertly, further complicating detection efforts. As organizations grapple with the fallout of this cyber onslaught, it becomes imperative to scrutinize existing security measures and fortify defenses against such sophisticated threats. The exploitation of legitimate platforms like Slack for nefarious purposes highlights the need for continuous vigilance and adaptation in the face of evolving cyber threats. The implications of this breach extend beyond mere data theft, posing significant risks to national security and economic stability. Efforts to attribute the attack to specific actors are ongoing, underscoring the complexity of the cyber landscape and the challenges inherent in identifying perpetrators. Amidst escalating cyber tensions, collaboration between public and private sectors is essential to mitigate the impact of such attacks and enhance cyber resilience. Lessons gleaned from this incident must inform future cybersecurity strategies, emphasizing the importance of proactive threat intelligence and robust defense mechanisms. As organizations navigate the aftermath of this breach, emphasis must be placed on rapid incident response, containment, and recovery to minimize the damage inflicted by cyber adversaries. The convergence of advanced malware, sophisticated tactics, and the exploitation of legitimate platforms underscores the need for a holistic approach to cybersecurity. By prioritizing continuous monitoring, threat hunting, and employee education, organizations can bolster their defenses and thwart future cyber threats.
Campaign Overview
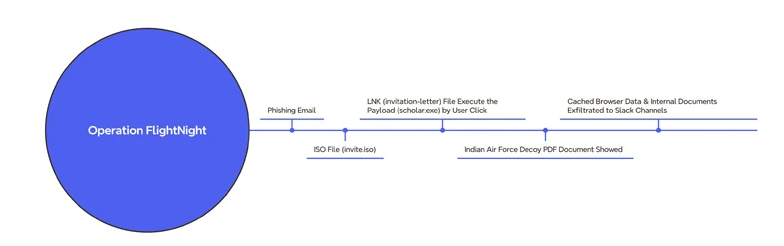
“Operation FlightNight” by cybersecurity researchers, this campaign was initiated on March 7, 2024, targeting various Indian government bodies, notably those engaged in electronic communications, IT governance, and national defense. Additionally, private energy corporations have fallen victim to this meticulously planned assault. The wide-ranging impact of the campaign underscores its sophistication and strategic intent, posing significant challenges for affected organizations and the broader cybersecurity community. As the campaign unfolds, it highlights the critical need for robust defense mechanisms and collaborative efforts between public and private sectors to mitigate the evolving cyber threats. The infiltration of both governmental and private sectors underscores the indiscriminate nature of cyber attacks, necessitating comprehensive security measures across all sectors.
Attack Vector
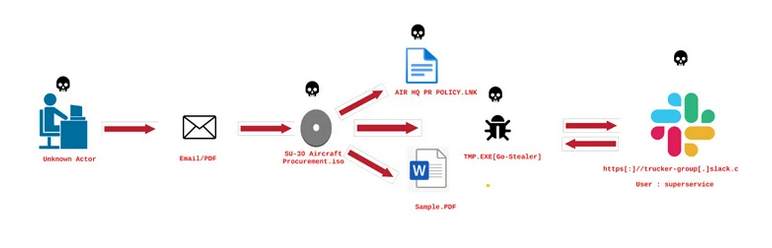
The attack vector initiates with a phishing email cleverly crafted to appear as an invitation letter from the Indian Air Force. Within this deceptive email, recipients encounter an attached ISO file named “invite.iso.” Concealed within this file is a Windows shortcut (LNK) designed to clandestinely execute a hidden binary named “scholar.exe.” Simultaneously, victims are presented with a decoy PDF file, masquerading as an official invitation letter from the Indian Air Force, serving to distract and further the illusion of legitimacy. This multifaceted approach underscores the meticulous planning and social engineering tactics employed by the threat actors, highlighting the need for heightened awareness and scrutiny among email recipients. Such sophisticated attack techniques underscore the challenges organizations face in defending against increasingly deceptive and targeted cyber threats.
Malware Functionality
The malware at the heart of the attack represents an evolved iteration of HackBrowserData, boasting expanded functionalities beyond its original purpose of browser data theft. This modified version is adept at exfiltrating various types of documents, including those in Microsoft Office, PDF, and SQL database formats. Moreover, it leverages Slack as a communication channel, enabling covert interactions with command-and-control servers. To evade detection, the malware employs sophisticated obfuscation techniques, enhancing its stealth and resilience against traditional security measures. This amalgamation of advanced capabilities signifies a significant escalation in cyber threat sophistication, posing formidable challenges to detection and mitigation efforts.
Exfiltration Process
Following execution, the malware operates covertly, systematically extracting a wealth of sensitive data including documents and cached web browser information. These pilfered assets are then surreptitiously relayed to a Slack channel dubbed “FlightNight,” under the control of the threat actors. This Slack channel serves as a clandestine conduit for the exfiltration of a myriad of confidential materials, ranging from internal documents to private email communications. The utilization of Slack as an exfiltration point underscores the adaptability of cyber adversaries in leveraging legitimate platforms for nefarious purposes, evading traditional detection measures. The seamless integration of Slack into the exfiltration process reflects the ingenuity of the attackers in exploiting widely-used communication tools to facilitate data theft. Such tactics highlight the evolving sophistication of cyber threats and necessitate a multi-layered approach to cybersecurity, encompassing both technological defenses and user education.
Similarities to Previous Campaigns
Comparative analysis has revealed striking parallels between Operation FlightNight and an earlier phishing endeavor directed at the Indian Air Force, utilizing a Go-based information stealer named GoStealer. Notably, both campaigns share identical infection sequences, employing procurement-themed bait to divert victims’ attention while executing data exfiltration via Slack. This similarity underscores a deliberate strategy by threat actors to replicate successful tactics, exploiting the familiarity and trust associated with official procurement communications. The use of Slack as a common exfiltration channel further underscores the operational consistency and adaptability of cyber adversaries, necessitating heightened vigilance and tailored defense strategies against such recurrent threats.
Implications and Insights
The utilization of accessible offensive tools such as HackBrowserData and the adaptation of legitimate platforms like Slack enable threat actors to orchestrate precise attacks with minimal resource expenditure and heightened evasion of detection measures. This phenomenon illuminates the shifting dynamics within the realm of cyber threats, where even less proficient cybercriminals possess the capability to exact substantial harm upon organizations. Consequently, it emphasizes the critical need for organizations to fortify their cybersecurity posture through proactive threat monitoring, swift incident response protocols, and ongoing adaptation to emerging adversarial tactics. In the face of an evolving threat landscape, vigilance and adaptability remain paramount in mitigating risks and preserving digital resilience.
Mitigating Steps:
- Enhanced Email Security Measures: Implement robust email filtering solutions capable of identifying and quarantining suspicious attachments and phishing attempts.
- Vigilant Employee Training Programs: Conduct regular cybersecurity awareness training sessions to educate employees on identifying phishing emails and avoiding malicious attachments.
- Multi-Factor Authentication (MFA): Enforce the use of MFA across all systems and applications to bolster authentication mechanisms and mitigate unauthorized access attempts.
- Comprehensive Endpoint Protection: Deploy advanced endpoint protection solutions equipped with heuristic detection capabilities to detect and thwart malware infiltration attempts.
- Network Segmentation: Segment the network to restrict lateral movement in the event of a breach, minimizing the potential impact of compromised systems.
- Continuous Monitoring and Threat Intelligence Integration: Establish a robust monitoring infrastructure capable of detecting anomalous activities and integrate threat intelligence feeds to stay abreast of emerging threats and adversary tactics.



