Potential Credential Leakage in Build Logs: Risks Posed by AWS, Google, and Azure CLI Tools
Recent cybersecurity research has uncovered a pressing vulnerability known as LeakyCLI, underscoring the potential dangers inherent in the command-line interface (CLI) tools offered by leading cloud service providers like Amazon Web Services (AWS) and Google Cloud. Identified and named by the cloud security firm Orca, this vulnerability exposes sensitive credentials within build logs, presenting substantial security risks for organizations reliant on these services. The inadvertent disclosure of such credentials can facilitate unauthorized access to critical resources, posing severe threats to data integrity and confidentiality. LeakyCLI has illuminated the need for heightened vigilance and robust security measures within cloud environments, urging organizations to reevaluate their reliance on CLI tools and fortify their defenses against potential breaches. This revelation underscores the evolving nature of cybersecurity threats in cloud ecosystems and the imperative for proactive mitigation strategies. As organizations navigate the complexities of cloud infrastructure, mitigating vulnerabilities like LeakyCLI demands a multifaceted approach encompassing rigorous access controls, enhanced monitoring capabilities, and the adoption of secure secrets management practices. Furthermore, this discovery serves as a poignant reminder of the collaborative efforts required across industries to identify, address, and mitigate emerging security threats effectively. In response to LeakyCLI, organizations must prioritize the implementation of remediation measures aimed at bolstering the resilience of their cloud environments and safeguarding sensitive information from malicious exploitation. By fostering a culture of security awareness and investing in robust defensive mechanisms, organizations can mitigate the risks posed by LeakyCLI and fortify their defenses against future vulnerabilities.
Understanding the Vulnerability
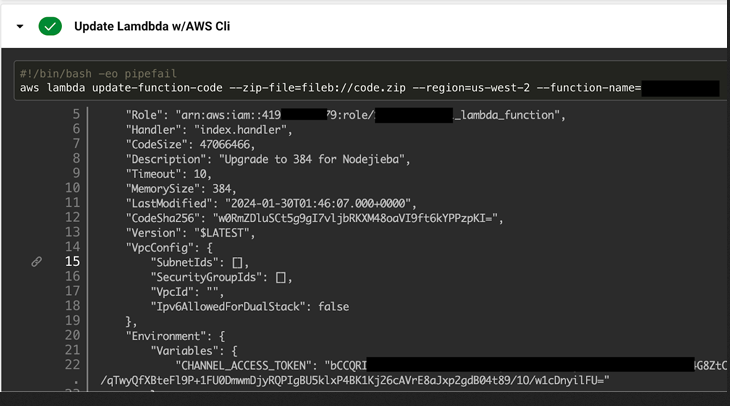
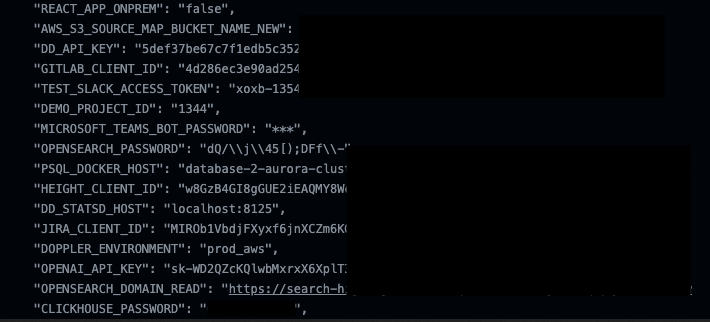
LeakyCLI exposes sensitive data through specific CLI commands, revealing critical information, notably environment variables, which can be captured by malicious entities. Integration into CI/CD pipelines exacerbates the risk, as these variables may be inadvertently published in logs, including those generated by platforms like GitHub Actions. This vulnerability underscores the peril of inadvertently disclosing sensitive information within cloud workflows, highlighting the need for stringent security measures. As environment variables are often utilized for storing credentials and other confidential data, their exposure poses significant threats to data integrity and confidentiality. Mitigating LeakyCLI requires careful scrutiny of CLI command usage and the implementation of robust controls to prevent inadvertent disclosures. Organizations must prioritize securing CI/CD pipelines and implementing encryption mechanisms to safeguard against potential breaches.
The Vulnerable Commands
A comprehensive list of vulnerable commands spans across AWS and Google Cloud platforms, including but not limited to:
- aws lambda get-function-configuration
- aws lambda get-function
- aws lambda update-function-configuration
- aws lambda update-function-code
- aws lambda publish-version
- gcloud functions deploy <func> –set-env-vars
- gcloud functions deploy <func> –update-env-vars
- gcloud functions deploy <func> –remove-env-vars
Implications and Risks
Orca’s inquiry revealed numerous GitHub projects inadvertently disclosing access tokens and sensitive data through widely-used CI/CD tools like GitHub Actions, CircleCI, TravisCI, and Cloud Build logs. If exploited, these leaked environment variables could compromise critical credentials such as passwords, usernames, and keys, granting unauthorized access to a repository owner’s resources. This exposure underscores the urgent need for stringent security measures to prevent unauthorized access and safeguard sensitive information within cloud environments. The potential ramifications of such breaches underscore the importance of proactive security measures and diligent oversight in protecting organizational assets from malicious exploitation.
Mitigation Strategies
While Microsoft swiftly addressed the vulnerability with security updates and assigned it the CVE identifier CVE-2023-36052, Amazon and Google take a different stance. Both companies consider this behavior to be expected, emphasizing the importance of organizations implementing robust security measures. They recommend avoiding the storage of secrets in environment variables and instead utilizing dedicated secrets store services like AWS Secrets Manager or Google Cloud Secret Manager.
Additionally, Google suggests leveraging the “–no-user-output-enabled” option to suppress the printing of command output to standard output and standard error in the terminal, thus minimizing the risk of inadvertently exposing sensitive information.
Remediation Steps: Strengthening Your Defense
- Review and Restrict CLI Command Usage: Conduct a comprehensive review of CLI command usage within your organization’s workflows, identifying and restricting the usage of vulnerable commands wherever possible.
- Implement Secrets Management Solutions: Transition away from storing sensitive credentials in environment variables and plaintext configurations. Utilize dedicated secrets management services such as AWS Secrets Manager or Google Cloud Secret Manager to securely store and manage credentials.
- Enhance Access Controls: Implement stringent access controls and adhere to the principle of least privilege to limit access to sensitive resources and credentials. Ensure that only authorized personnel have access to critical infrastructure components.
- Secure CI/CD Pipelines: Enhance the security posture of your CI/CD pipelines by implementing encryption mechanisms for storing and transmitting credentials securely. Integrate static code analysis and security scanning tools to detect and remediate vulnerabilities in code and configurations.
- Leverage Output Suppression: Follow best practices recommended by cloud providers, such as enabling the “–no-user-output-enabled” option, to suppress the printing of command output to standard output and standard error in the terminal, minimizing the risk of inadvertent exposure.
- Enable Logging and Monitoring: Establish robust logging and monitoring capabilities to detect anomalous behavior and unauthorized access attempts. Regularly review audit logs and set up alerts for suspicious activities to enable timely response and remediation.



