Critical Vulnerability in Popular Android Apps Exposes Over 1.5 Billion Users to Potential Exploitation
A recent report by Dimitrios Valsamaras from the Microsoft Threat Intelligence team has shed light on a significant security flaw affecting numerous Android applications, leaving millions of users vulnerable to potential attacks. Dubbed the “Dirty Stream attack,” this vulnerability, centered around path traversal, could be exploited by malicious apps to overwrite critical files within the vulnerable app’s home directory.
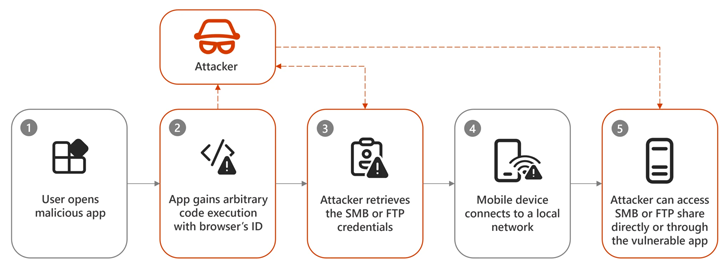
“Dirty Stream” is a newly identified vulnerability in Android applications that enables malicious apps to manipulate and overwrite files within another app’s home directory. This vulnerability can have severe consequences, including arbitrary code execution and theft of sensitive data.
At the heart of the Dirty Stream vulnerability is the misuse of Android’s content provider system. The content provider system is designed to manage access to shared data sets among different applications while enforcing security measures to prevent unauthorized access and path traversal attacks.
Malicious actors exploit this vulnerability by leveraging custom intents, which are messaging objects facilitating communication between components across Android apps. By manipulating these intents, attackers can deceive target apps into trusting unvalidated filenames or paths. This manipulation leads the target apps to execute or store files in critical directories, allowing attackers to gain unauthorized access, execute arbitrary code, or steal sensitive information.
The Dirty Stream vulnerability has a widespread impact, affecting numerous Android applications installed over billions of times. High-profile apps like Xiaomi’s File Manager and WPS Office have been identified as vulnerable targets.
The Vulnerable Apps
Among the widely used applications found susceptible to this exploit are Xiaomi File Manager (com.mi. Android.globalFileexplorer) and WPS Office (cn.wps.moffice_eng), boasting over 1 billion and 500 million installations respectively.
Understanding the Vulnerability
Android’s implementation of isolation typically assigns dedicated data and memory spaces to each application, maintaining security boundaries. However, flaws in the implementation of content providers, designed to facilitate secure data and file sharing between apps, can lead to the bypassing of read/write restrictions within an app’s home directory.
Exploitation and Consequences
Exploiting this vulnerability could enable attackers to assume full control over an application’s functionality, potentially leading to unauthorized access to users’ online accounts and sensitive data.
By manipulating file-sharing mechanisms and leveraging weaknesses in how apps handle filenames, attackers could execute arbitrary code and overwrite critical files, including shared preferences and native libraries.
Mitigation and Responses
Following responsible disclosure, both Xiaomi and WPS Office have addressed the issue in their respective apps. However, Microsoft warns that similar vulnerabilities may exist in other apps, emphasizing the need for developers to conduct thorough security checks.
In response, Google has issued guidance to developers, urging them to implement proper filename handling practices to mitigate the risk of exploitation. Recommendations include using internally generated unique identifiers for filenames and sanitizing provided filenames to prevent potential attacks.
The ‘Dirty Stream’ vulnerability uncovered in popular Android apps is another incident that underlines the urgency for continuous vigilance in the cloud threat landscape. This flaw, which can trigger arbitrary code execution and token theft, reinforces the importance of secure coding practices. To protect from such threats, companies should:
- Invoke rigorous application testing and code review policies to uncover potential vulnerabilities early on.
- Encourage users to regularly update their applications, so they receive patched versions in a timely manner.
- Implement a solid incident response plan to promptly address any security issues that might arise.



