Critical Flaws in Cacti Framework Could Let Attackers Execute Malicious Code
Cacti, a framework for network monitoring and fault management, has recently bolstered its security measures by tackling critical vulnerabilities. This post offers an in-depth examination of these vulnerabilities, their potential ramifications, and the steps to mitigate them effectively. The analysis underscores the importance of proactive security measures in safeguarding Cacti deployments. By addressing these vulnerabilities, Cacti aims to enhance its resilience against potential exploits and malicious activities. Users are urged to stay informed about security updates and promptly apply patches to mitigate risks. Understanding the nature of these vulnerabilities is essential for maintaining a secure network infrastructure. Cacti’s commitment to security underscores its dedication to providing a robust and reliable platform for network monitoring. Effective mitigation strategies are crucial in minimizing the impact of vulnerabilities and fortifying Cacti installations against potential threats. Organizations must prioritize security measures to ensure the integrity and availability of their network monitoring systems.
Vulnerability Overview
- CVE-2024-25641 – Arbitrary File Write in Package Import
- CVSS Score:1
- This vulnerability enables authenticated users with “Import Templates” permission to execute arbitrary PHP code through the “Package Import” feature, resulting in remote code execution.
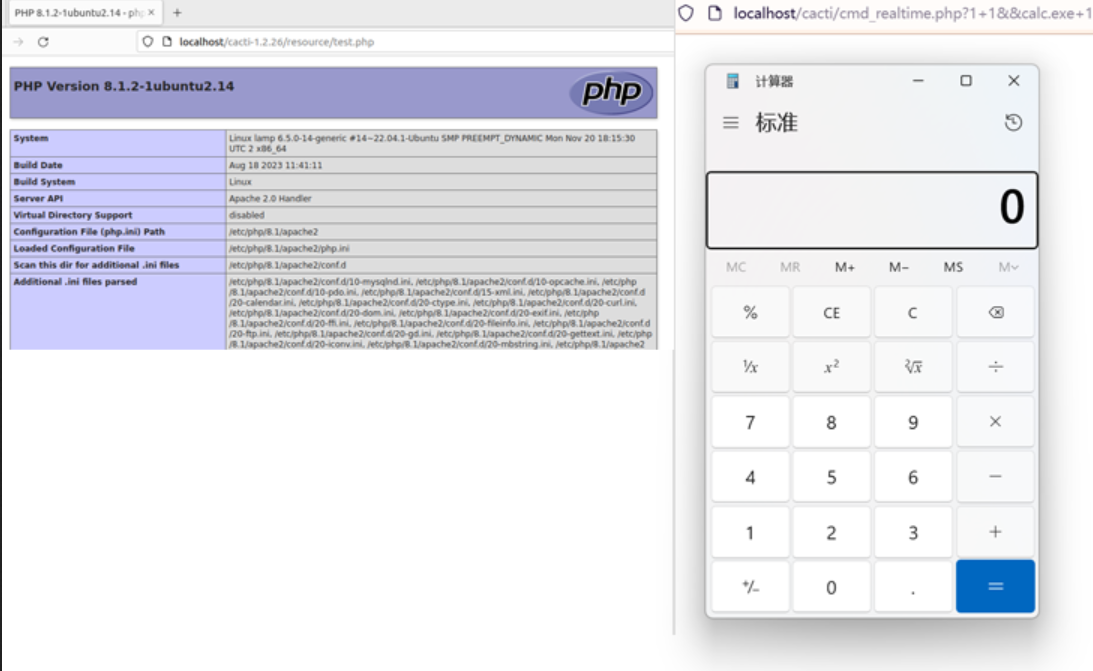
- CVE-2024-29895 – Command Injection
- CVSS Score:0
- Unauthenticated users can exploit this flaw to execute arbitrary commands on the server when the PHP option “register_argc_argv” is enabled.
- CVE-2024-31445 – SQL Injection in api_automation.php
- CVSS Score:8
- Authenticated users can leverage this vulnerability to escalate privileges and achieve remote code execution through SQL injection.
- CVE-2024-31459 – File Inclusion in lib/plugin.php
- CVSS Score: N/A
- This flaw in the “lib/plugin.php” file, when combined with SQL injection vulnerabilities, facilitates remote code execution.
Detailed Summary
- CVE-2024-25641: The critical vulnerability CVE-2024-25641, with a CVSS score of 9.1, concerns an arbitrary file write issue in Cacti’s “Package Import” feature. This flaw enables authenticated users possessing the “Import Templates” permission to execute arbitrary PHP code on the web server. Consequently, remote code execution becomes feasible, posing a severe threat to system security. This vulnerability underscores the importance of thorough security measures in network monitoring frameworks like Cacti. It highlights the potential consequences of unauthorized access and exploitation of system functionalities. Mitigation efforts must prioritize patching this vulnerability promptly to prevent unauthorized code execution. Cacti users should remain vigilant and take proactive steps to safeguard their systems against potential exploits. Understanding the nature of this vulnerability is crucial for implementing effective security measures.
- CVE-2024-29895: The critical CVE-2024-29895 vulnerability, rated at a CVSS score of 10.0, involves command injection in Cacti. This flaw permits unauthenticated users to execute arbitrary commands on the server. Exploiting the “register_argc_argv” option in PHP, attackers can gain unauthorized access and execute commands with significant repercussions. The severity of this vulnerability underscores the urgent need for mitigation measures. Unauthorized command execution poses serious risks to system integrity and data security. Prompt action is imperative to patch this vulnerability and prevent potential exploits. Mitigation efforts should focus on securing the affected functionality to mitigate the risk of unauthorized command execution. Cacti administrators must remain vigilant and implement robust security measures to protect against such vulnerabilities. Understanding the intricacies of this exploit is crucial for effective vulnerability management.
- CVE-2024-31445: The SQL injection vulnerability, with an 8.8 CVSS score, is located within api_automation.php. It allows authenticated users to escalate privileges and execute remote code, posing a substantial risk to system integrity. Exploiting this flaw enables unauthorized access and potential compromise of sensitive data. The severity of this vulnerability underscores the urgency for mitigation. Mitigation efforts should prioritize patching the affected functionality to prevent unauthorized privilege escalation. Proactive measures are essential to mitigate the risk of exploitation and protect system integrity. Understanding the nature and implications of this vulnerability is critical for effective remediation. Organizations must take decisive action to address this security threat promptly.
- CVE-2024-31459: This file inclusion flaw in “lib/plugin.php” presents a security concern with an undetermined CVSS score. It has the potential to compound security risks by enabling remote code execution. When coupled with SQL injection vulnerabilities, the consequences of this exploit become more severe. The risk is further heightened due to the ability to execute arbitrary code remotely. Understanding the interplay between file inclusion and SQL injection vulnerabilities is crucial for assessing the overall security posture. Mitigation efforts should address both vulnerabilities comprehensively to prevent potential exploits. Administering timely patches and implementing robust security measures are essential steps in mitigating this security risk. Organizations must remain vigilant and proactive in addressing such vulnerabilities to safeguard their systems effectively.
Version Affected and Remediation
Significantly, 10 of the 12 identified vulnerabilities affect all Cacti versions, including those up to 1.2.26. These flaws have been successfully addressed in version 1.2.27, launched on May 13, 2024. It’s crucial for users to swiftly upgrade to the newest release to reduce the risk of exposure to potential threats. This emphasizes the importance of staying current with software updates to maintain a secure environment. Users must prioritize updating their instances to mitigate the vulnerabilities effectively. Failure to do so could leave systems vulnerable to exploitation. Timely updates are a fundamental aspect of maintaining the security posture of Cacti deployments. Organizations should ensure that their systems are regularly patched to safeguard against emerging threats.
Historical Context
The recent security upgrades in Cacti build upon prior critical vulnerabilities. In 2023, CVE-2023-39361, a SQL injection flaw with a CVSS score of 9.8, posed substantial risks of privilege escalation and code execution. Additionally, CVE-2022-46169, disclosed early in 2023, was actively exploited, underscoring the necessity for robust security measures. These incidents emphasize the continuous threat landscape facing Cacti deployments. Implementing comprehensive security protocols is vital to safeguarding against emerging threats and ensuring the integrity of network monitoring systems. Cacti users must remain vigilant and proactive in addressing vulnerabilities to mitigate potential risks effectively. Upgrading to the latest versions, monitoring for anomalies, and implementing stringent access controls are essential steps in fortifying Cacti installations against exploitation. By staying abreast of security advisories and promptly applying patches, organizations can bolster their defenses and uphold the reliability of their network infrastructure.
Recommendations
Given the availability of proof-of-concept (PoC) exploits for these vulnerabilities, users are strongly advised to prioritize the update of their Cacti instances to the latest version. Additionally, implementing stringent access controls, conducting regular security assessments, and staying informed about emerging threats are essential practices to bolster the security posture of Cacti deployments.
- Update to Cacti Version 1.2.27: Immediately upgrade existing installations to the latest version, 1.2.27, released on May 13, 2024, which includes patches for all identified vulnerabilities.
- Disable “register_argc_argv” in PHP: Set the PHP option “register_argc_argv” to Off in php.ini to mitigate the risk of command injection for unauthenticated users.
- Restrict User Permissions: Review and adjust user permissions within Cacti to limit access to critical functionalities such as template importing, reducing the attack surface for potential exploits.
- Implement Web Application Firewall (WAF): Deploy a WAF to monitor and filter incoming traffic, detecting and blocking attempts to exploit known vulnerabilities.
- Regular Security Audits: Conduct periodic security audits of Cacti installations, scanning for vulnerabilities and applying updates promptly to stay protected against emerging threats.
- Input Validation and Sanitization: Implement stringent input validation and data sanitization techniques to prevent injection attacks such as SQL injection and command injection.
- Monitor and Analyze Logs: Maintain comprehensive logs of system and application activities, monitoring for suspicious behavior or unauthorized access attempts, and take appropriate action if anomalies are detected.



