Grandoreiro Banking Trojan Resurfaces, Targeting Over 1,500 Banks Worldwide
The infamous Grandoreiro banking trojan has reappeared in a global campaign since March 2024, targeting over 1,500 banks across 60 countries. This resurgence follows a law enforcement takedown in January 2024, signaling a strategic shift from its traditional Latin American focus to a wider global scope. According to IBM X-Force, Grandoreiro has undergone significant enhancements, showcasing ongoing development and increased sophistication. These improvements suggest a more formidable threat as the malware expands its reach, leveraging advanced tactics to evade detection and establish persistence on compromised systems. The campaign relies heavily on phishing attacks, likely supported by a Malware-as-a-Service (MaaS) model, which lowers the entry barrier for cybercriminals. Phishing emails, designed to appear legitimate, prompt recipients to click malicious links, leading to the download of a ZIP archive containing the Grandoreiro loader executable. This loader employs various evasion techniques, including file size inflation and sandbox detection, to bypass security measures. Once installed, it establishes persistence through the Windows Registry and connects to Command and Control (C2) servers using a reworked Domain Generation Algorithm (DGA). The malware’s new capabilities include exploiting Microsoft Outlook to harvest data and spread further phishing emails, broadening its attack surface and impact.
Phishing Frenzy with Malware-as-a-Service (MaaS)
The new Grandoreiro campaign leverages large-scale phishing attacks, supported by a Malware-as-a-Service (MaaS) model. This approach enables cybercriminals to rent access to the malware and its distribution network, making it accessible to less skilled attackers. Phishing emails, designed to look legitimate, often impersonate trusted government entities pertinent to the target’s location. These emails usually prompt recipients to click on a malicious link to view an invoice or make a payment. This tactic effectively deceives users into downloading the malware, initiating the infection process. The new Grandoreiro campaign leverages large-scale phishing attacks, supported by a Malware-as-a-Service (MaaS) model. This approach enables cybercriminals to rent access to the malware and its distribution network, making it accessible to less skilled attackers. Phishing emails, designed to look legitimate, often impersonate trusted government entities pertinent to the target’s location. These emails usually prompt recipients to click on a malicious link to view an invoice or make a payment. This tactic effectively deceives users into downloading the malware, initiating the infection process.
Deceptive Downloads and Evasion Techniques
PDF Icon Trick
Clicking on the link in the phishing email takes the victim to a seemingly innocuous image of a PDF icon. This action triggers the download of a ZIP archive containing the Grandoreiro loader executable.
Bypassing Anti-Malware Scanners
The loader is designed to bypass security measures by artificially inflating its file size to over 100 MB. This excessive size can trick some anti-malware scanners into overlooking it as a potential threat.
Sandbox Detection and Geolocation Checks
The loader employs several evasion techniques, including sandbox detection mechanisms to avoid execution in security testing environments. Additionally, it performs geolocation checks and verifies the presence of antivirus software. Systems located in specific countries (e.g., Russia, Czech Republic) or those lacking antivirus protection are skipped, avoiding detection by security researchers or honeypots.
Establishing Persistence
After successfully bypassing these evasion techniques, the Grandoreiro loader establishes persistence on the compromised system by embedding itself within the Windows Registry. This strategic move ensures that the malware automatically launches each time the system restarts, maintaining its presence and functionality without user intervention. This persistence mechanism is crucial for the malware’s long-term operations, allowing it to continually execute its malicious activities and communicate with its Command and Control (C2) servers whenever the infected system is active.
Command and Control (C2) Connectivity
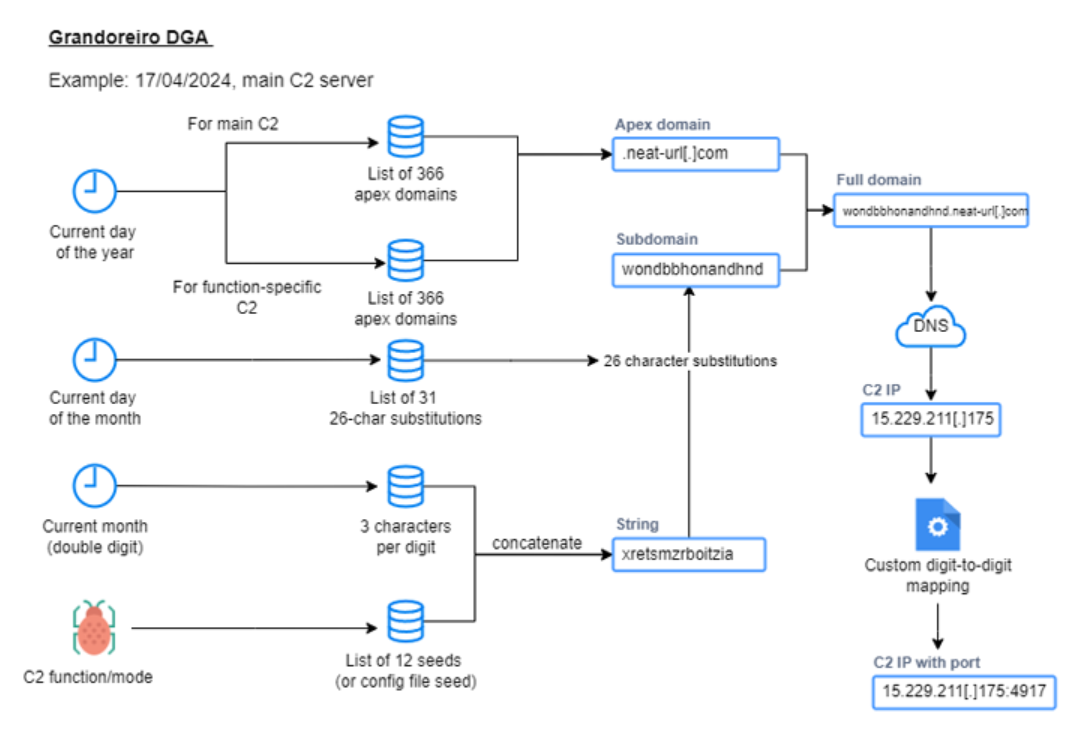
The Grandoreiro loader employs a reworked Domain Generation Algorithm (DGA) to dynamically generate and connect to Command and Control (C2) servers. This advanced technique complicates the efforts of security researchers and network defenders to track and block malicious traffic, as the C2 server addresses continuously change. By frequently altering these addresses, the malware avoids detection and takedown, maintaining a resilient connection with its control infrastructure. This dynamic C2 connectivity ensures that the attackers can consistently issue commands, receive stolen data, and update the malware, thereby sustaining their malicious activities over an extended period.
Expanded Arsenal with Email Spamming
Remote Control and File Operations
Once Grandoreiro connects to the C2 server, it receives further instructions, activating a range of malicious capabilities. These capabilities enable attackers to take remote control of the infected system, steal files, deploy additional malware, and manipulate system settings. This comprehensive control allows the attackers to conduct extensive malicious activities, from data theft to system sabotage, significantly increasing the threat’s impact and persistence. The malware’s versatility and control make it a potent tool for cyber criminals, capable of executing various harmful operations on compromised systems.
Microsoft Outlook Exploitation
A notable new feature of Grandoreiro is its module that harvests data from Microsoft Outlook. This module uses the Outlook Security Manager tool to interact with the local Outlook client without triggering security alerts from the Outlook Object Model Guard. By doing so, it can stealthily gather email addresses and contact lists. The stolen data is then used to launch additional phishing campaigns, spreading the malware further and creating a ripple effect of infections. This capability significantly broadens the attack surface, allowing Grandoreiro to propagate rapidly through compromised email accounts.
Remediation steps:
- User Awareness and Training: Educate users about phishing tactics and red flags. Train them to identify suspicious emails, verify sender legitimacy, and avoid clicking on unknown links or opening attachments from untrusted sources. Consider simulating phishing attacks to test user awareness and effectiveness of training programs.
- Layered Email Security: Deploy a combination of email security solutions including:
- Spam Filtering: Implement robust spam filtering solutions at the gateway level to block a significant portion of phishing emails before they reach user inboxes.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Enforce DMARC to prevent unauthorized emails from spoofing your organization’s domain.
- Email Security Awareness Training (ESAT): Complement technical controls with regular ESAT programs to enhance user awareness and ability to identify phishing attempts.
- Endpoint Security: Equip all devices with up-to-date endpoint security software featuring real-time protection capabilities. These solutions should include:
- Anti-Malware: Continuously updated anti-malware engines can detect and block the initial download and execution of Grandoreiro or similar trojans.
- Behavior-Based Detection: Employ endpoint security solutions that utilize behavior-based detection techniques to identify and block malicious activities even if the specific malware strain is unknown.
- Application Whitelisting: Implement application whitelisting to restrict software execution to only authorized programs, preventing unauthorized applications like Grandoreiro from running on your systems.
- Web Security: Enforce web security measures to prevent users from accessing malicious websites that might host the trojan or its components:
- Web Filtering: Utilize web filtering solutions to block access to known malicious websites and domains associated with Grandoreiro or other banking trojan campaigns.



