Kimsuky Hacking Group Employs Social Engineering via Facebook Messenger
A new social engineering attack by the North Korea-linked Kimsuky hacking group has been identified. Unlike their typical email-based spear-phishing tactics, this operation uses fake Facebook accounts to target victims. The hackers engage individuals through Facebook Messenger, ultimately aiming to deliver malware. This strategy marks a shift in Kimsuky’s approach, highlighting their adaptability and the growing threat of social media as a vector for cyber attacks. The use of Messenger allows the attackers to build trust and bypass traditional email security measures, making the campaign more effective and insidious. This development underscores the need for heightened vigilance and robust cybersecurity measures across all communication platforms.
Attack Strategy
Creation of Fictitious Facebook Accounts: The threat actors behind this campaign created Facebook accounts with fake identities, pretending to be public officials involved in North Korean human rights. This tactic is intended to build credibility and trust with their targets, who are mainly activists in the North Korean human rights and anti-North Korea sectors. By posing as credible figures, the attackers aim to more effectively engage and deceive their intended victims.
Engagement via Facebook Messenger: After establishing fake identities, the attackers use Facebook Messenger to reach their targets. This marks a shift from traditional email-based spear-phishing, leveraging the social media platform for initial contact. The new approach enables direct engagement with victims, enhancing the attackers’ ability to deceive and gain trust.
Execution of the Multi-Stage Attack
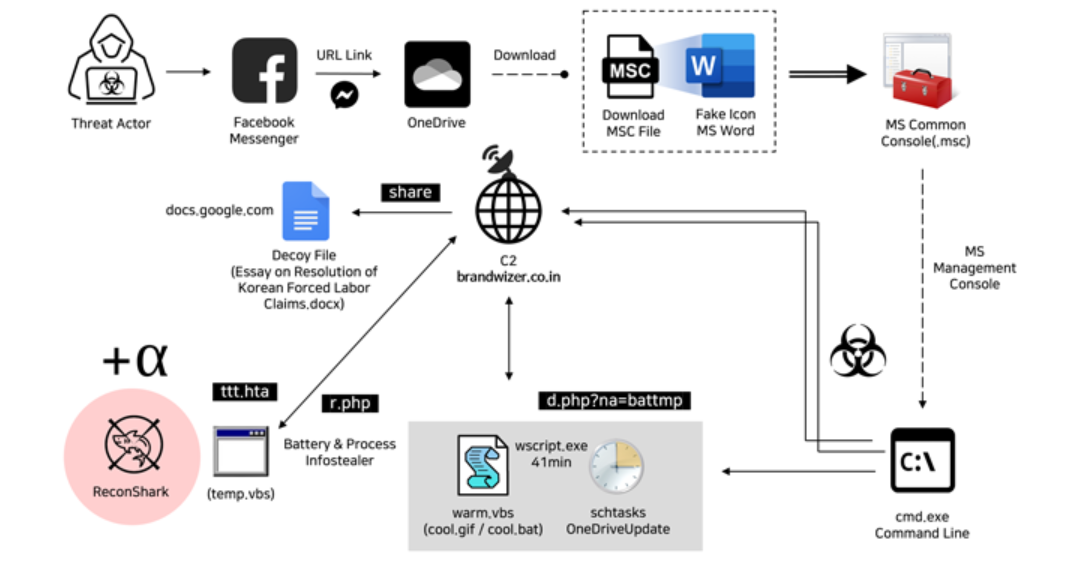
Delivery of Decoy Documents: The attackers send decoy documents to their targets via OneDrive. These files, named “My_Essay(prof).msc” and “NZZ_Interview_Kohei Yamamoto.msc,” pose as essays or content related to significant political events, such as a trilateral summit involving Japan, South Korea, and the U.S. The “NZZ_Interview_Kohei Yamamoto.msc” document was uploaded to VirusTotal on April 5, 2024, from Japan, suggesting potential targeting of individuals in Japan and South Korea. This indicates a sophisticated level of targeting by the attackers, tailoring their approach to specific geopolitical contexts. The use of OneDrive for hosting the decoy documents adds another layer of complexity to the attack, leveraging cloud storage services to distribute malware. By disguising the malicious files as seemingly legitimate documents, the attackers increase the likelihood of successful infiltration.
Use of MSC Files: In their attack, Kimsuky utilizes MSC files (Microsoft Common Console), an uncommon document format intended to bypass detection measures. These files are camouflaged with a Word document icon to appear benign at first glance. This tactic aims to deceive users into opening them unsuspectingly. MSC files are chosen strategically for their obscurity, making them less likely to be flagged by traditional security systems. By adopting this unconventional approach, Kimsuky enhances the stealthiness of their operation. The disguise as a Word document icon further adds to the files’ perceived legitimacy, increasing the chances of successful infiltration. This demonstrates the group’s sophistication in employing novel techniques to achieve their objectives.
Activation of the Attack Sequence
When a victim opens the MSC file and consents to using Microsoft Management Console (MMC), they are presented with a console screen containing a Word document. Launching this document activates the attack sequence:
- A connection is established with an adversary-controlled server (“brandwizer.co[.]in”).
- A document hosted on Google Drive (“Essay on Resolution of Korean Forced Labor Claims.docx”) is displayed to the victim.
- Background instructions are executed to set up persistence and collect information such as battery status and running processes.
Data Exfiltration and Command-and-Control
- Collection of Information: Data collected, such as IP addresses, User-Agent strings, and timestamps from HTTP requests, is sent to the command-and-control (C2) server for exfiltration. This server also has the capability to deliver appropriate payloads when required. This process facilitates the extraction of sensitive information from compromised systems. The exfiltration of data to the C2 server enables the attackers to maintain control and gather intelligence from their targets. The server’s functionality extends beyond data retrieval to include the delivery of relevant payloads, enhancing the attackers’ operational capabilities. This integrated approach streamlines the attack process, allowing for efficient data collection and dissemination.
- Overlapping TTPs: Genians have detected similarities in tactics, techniques, and procedures (TTPs) between the current attack and previous Kimsuky operations, notably those associated with ReconShark malware, as outlined by SentinelOne in May 2023. This analysis suggests a consistent modus operandi employed by Kimsuky across multiple campaigns. The identification of overlapping TTPs provides valuable insights into the group’s operational patterns and tactics. It indicates a degree of continuity in Kimsuky’s approach to cyber operations. Such findings enable cybersecurity experts to better understand and anticipate the group’s behaviors, enhancing defenses against future attacks.
Importance of Early Detection
- Challenges in Detection: Spear-phishing continues to be the predominant method for advanced persistent threat (APT) attacks in South Korea. Nevertheless, there is a rising trend of covert attacks through social media channels. These attacks, due to their tailored approach, pose challenges for conventional security monitoring and frequently remain undisclosed, even when victims recognize them. The increase in social media-based attacks highlights the evolving tactics of cyber adversaries. Detection of such personalized threats requires enhanced cybersecurity measures and heightened awareness. Organizations must adapt their security protocols to counter these emerging threats effectively.
- Necessity of Early Detection: Early detection of these tailored threats is paramount. Given the sophistication and personalized nature of the attacks, heightened vigilance and advanced security measures are imperative to mitigate the associated risks. It’s crucial to remain vigilant and implement proactive security measures to counteract these social engineering campaigns effectively. Enhanced awareness and rapid response mechanisms are necessary to thwart such targeted cyber threats. By bolstering defenses and maintaining a proactive stance, organizations can minimize the impact of these sophisticated attacks.
Remediation Steps
- User Awareness and Training: Educate users, especially those in high-risk sectors such as human rights and activism, about the dangers of social engineering attacks. Training should include recognizing fake social media profiles and suspicious messages.
- Enhanced Verification Processes: Implement verification processes for social media interactions. Encourage employees to verify the identity of new contacts independently before engaging with them, especially if the interaction involves sharing or opening documents.
- Use of Advanced Threat Detection Tools: Deploy advanced threat detection tools that can identify and flag unusual file types and behaviors, such as MSC files disguised as Word documents. These tools should be capable of real-time monitoring and alerting.
- Regular Software Updates and Patching: Ensure that all systems, including Microsoft Management Console, are regularly updated and patched to protect against known vulnerabilities that could be exploited by attackers.
- Email and Social Media Security Solutions: Utilize security solutions that extend beyond email to cover social media platforms. These solutions should include capabilities for monitoring and detecting phishing attempts and malicious links shared via social media.
- Implement Multi-Factor Authentication (MFA): Enforce the use of multi-factor authentication for all accounts, especially those with access to sensitive information. MFA provides an additional layer of security, making it more difficult for attackers to gain unauthorized access.
- Network Segmentation and Access Controls: Segment your network to limit the spread of malware if an initial infection occurs. Implement strict access controls to ensure that only authorized personnel have access to critical systems and sensitive data.
- Incident Response Plan: Develop and regularly update an incident response plan specifically tailored to address social engineering and malware attacks. Ensure that all team members are familiar with their roles and responsibilities during an incident.
- Regular Backups and Data Recovery Testing: Conduct regular backups of critical data and test the data recovery process frequently. This ensures that you can quickly restore systems and data in the event of a successful attack.



