Foxit PDF Reader Flaw Exploited by Hackers to Deliver Diverse Malware Arsenal
Threat actors are exploiting a design flaw in Foxit PDF Reader to deliver various malware, including Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm. This vulnerability permits the execution of harmful commands via deceptive security warnings. Unlike Adobe Acrobat Reader, Foxit PDF Reader is susceptible to this exploit, enabling malware to bypass typical sandbox and antivirus detection methods.
The flaw involves a sequence of misleading prompts: the first pop-up asks users to trust the document, with “OK” as the default option. Clicking “OK” triggers a second warning with “Open” set as the default, which then executes a command to download and run a malicious payload hosted on Discord’s CDN.
Threat actors exploit this design flaw and human behavior patterns, making users more likely to click through the prompts without reading them. Check Point researchers have identified PDF files with military themes that, when opened in Foxit PDF Reader, fetch downloaders that install malware for data exfiltration, including screenshots.
These campaigns blend in with normal traffic by using legitimate platforms like Discord, Gitlab, and Trello for payload delivery. The persistent exploitation and low detection rates highlight the need for enhanced user awareness and security measures. Foxit is expected to release a fix in version 2024.3.
Technical Details of the Exploit
Security Warning Manipulation
The exploit exploits Foxit PDF Reader’s flawed handling of security warnings. Users are first prompted to trust a document with “OK” as the default option. Clicking “OK” brings up a second warning where “Open” is the default, leading to unintended command execution. This deceptive sequence can easily mislead users into running malicious commands unknowingly. This flaw allows attackers to bypass detection methods focused on Adobe Acrobat Reader, deploying malware like Agent Tesla, AsyncRAT, and more via payloads hosted on Discord’s CDN. Human behavior is exploited as users often click through prompts without reading them. Check Point researchers identified PDFs that, when opened in Foxit, installed malware to exfiltrate data, including screenshots. Foxit plans to fix this issue in version 2024.3, underscoring the need for better user awareness and security measures.
Command Execution and Payload Delivery
When the user confirms the second prompt, the exploit triggers a command to download and execute a malicious payload hosted on Discord’s CDN. This method blends malicious activities with legitimate network traffic, making it harder for security systems to detect. By exploiting this flaw in Foxit PDF Reader, attackers can bypass traditional detection methods, allowing malware to be delivered covertly. This approach leverages the trust in familiar platforms and typical user behavior to spread malware more effectively, highlighting the need for heightened vigilance and improved security measures.
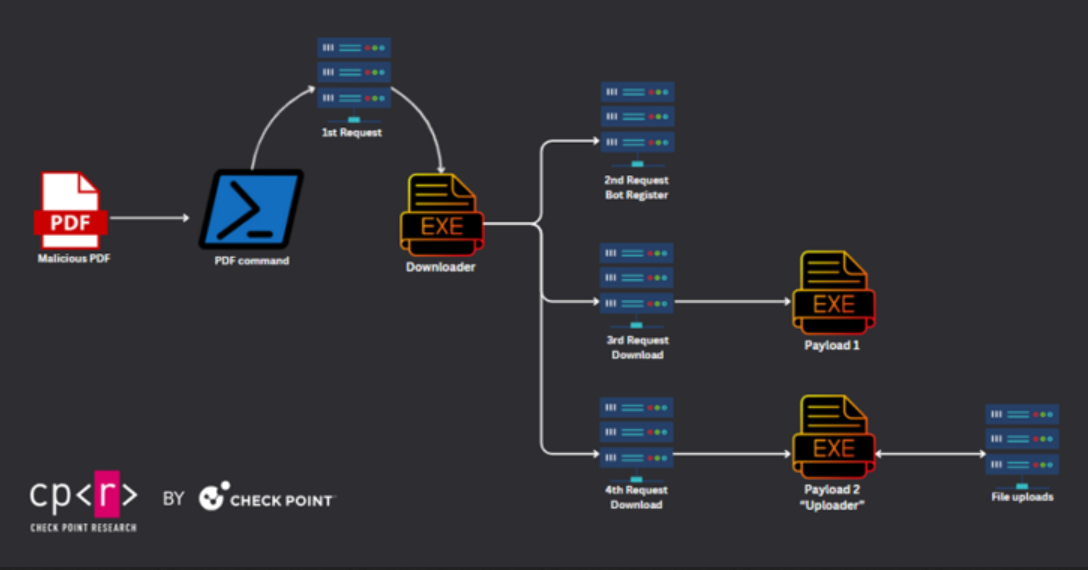
Case Studies of Exploited Campaigns
Espionage Campaign by DoNot Team
Check Point identified a military-themed PDF that, when opened in Foxit PDF Reader, executed a downloader to retrieve two executables. These executables collected and uploaded sensitive data, including documents, images, archives, and databases, to a C2 server. The campaign, attributed to DoNot Team (aka APT-C-35 and Origami Elephant), also deployed a third payload to capture and upload screenshots from infected hosts.
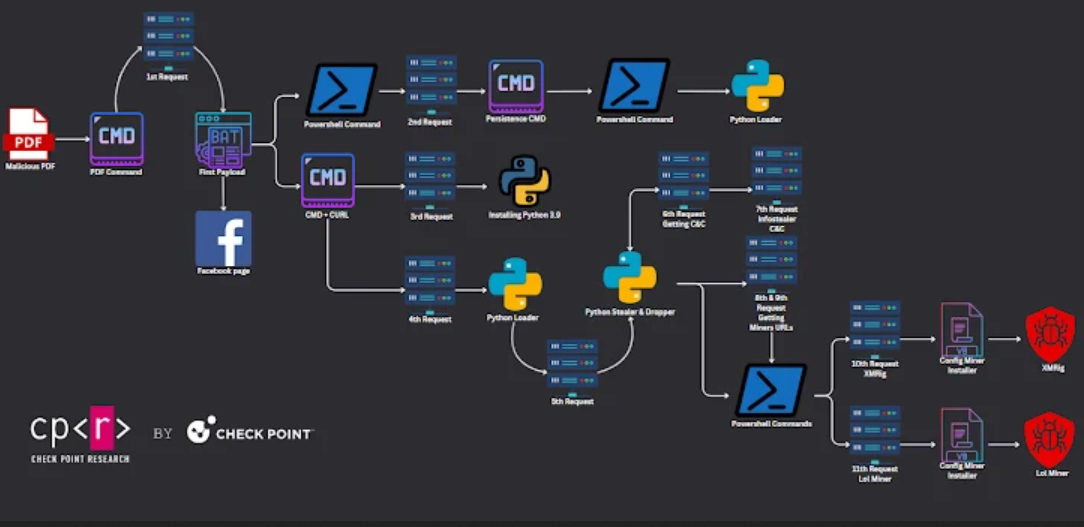
Cryptocurrency Mining and Credential Theft
Another instance employed a multi-stage process to deploy a stealer and cryptocurrency miners, including XMRig and lolMiner. The initial Python-based stealer extracted credentials and cookies from Chrome and Edge browsers. The miners were retrieved from an active Gitlab repository created by a user named topworld20241 on February 17, 2024.
Information Stealer via Discord CDN
A separate campaign utilized Discord CDN to deliver Blank-Grabber, an open-source information stealer archived on GitHub as of August 6, 2023. This method involved booby-trapped PDF files distributed through Facebook, illustrating the threat actors’ use of social media for malware dissemination.
Advanced Infection Pathways
Remcos RAT Campaign
An elaborate infection chain was identified involving the delivery of Remcos RAT. The attack began with a malicious PDF containing a hyperlink to an attachment hosted on Trello, which led to a secondary PDF embedded with malicious code. The infection process progressed through several stages, utilizing LNK files, HTML Application (HTA), and Visual Basic scripts before finally deploying Remcos RAT. This multi-step approach demonstrates the complexity and sophistication of the attack, designed to evade detection and ensure successful malware installation.
Threat Actor Profiles
- Silentkillertv and Silent Tools: The Remcos RAT campaign was attributed to a threat actor known as silentkillertv, who advertises malicious tools via a Telegram channel named silent_tools. Active since April 21, 2022, the channel promotes crypters and PDF exploits targeting Foxit PDF Reader.
- Use of PDF Builder Services: Threat actors have been using various .NET- and Python-based PDF builder services to create malware-laced PDF files. These services include Avict Softwares I Exploit PDF, PDF Exploit Builder 2023, and FuckCrypt. DoNot Team has specifically used a .NET PDF builder available on GitHub.
Abuse of Legitimate Platforms
The exploitation campaigns highlight the persistent abuse of legitimate platforms like Discord, Gitlab, and Trello by threat actors. This tactic allows them to evade detection by blending malicious activities with normal network traffic. By using trusted platforms, attackers can distribute malware more effectively while avoiding traditional security measures. This approach underscores the need for enhanced monitoring and security protocols to detect and mitigate such sophisticated threats.
Remediation Steps for Foxit PDF Reader Exploit
- Update Foxit PDF Reader: Ensure that all instances of Foxit PDF Reader are updated to the latest version as soon as the fix (version 2024.3 or later) is released. Regularly check for updates and apply them promptly to protect against newly discovered vulnerabilities.
- Educate Users on Security Prompts: Conduct training sessions for users to make them aware of the risks associated with clicking “OK” on security warnings without fully understanding the implications. Emphasize the importance of reading prompts carefully before taking action.
- Implement Application Whitelisting: Use application whitelisting to control which programs are allowed to run on your systems. This can help prevent unauthorized or malicious executables from being launched by the PDF reader or any other application.
- Enhance Email and Web Filtering: Strengthen email and web filtering mechanisms to detect and block malicious PDF files. This includes configuring email gateways to scan attachments for known threats and using web proxies to block access to malicious content delivery networks like Discord CDN.
- Deploy Endpoint Detection and Response (EDR) Solutions: Utilize EDR tools to monitor and analyze endpoint activities for suspicious behaviors, such as unauthorized command executions or unusual network traffic patterns. EDR solutions can provide real-time detection and response capabilities to mitigate threats.
- Restrict Macro and Script Execution: Configure Foxit PDF Reader and other applications to restrict the execution of macros, scripts, and embedded commands unless absolutely necessary. This can be achieved by adjusting security settings within the application and using group policies.
- Monitor and Analyze Network Traffic: Implement network monitoring tools to analyze traffic for signs of data exfiltration or communication with known command-and-control servers. Set up alerts for unusual outbound connections, particularly to platforms commonly abused by threat actors, such as Discord, Gitlab, and Trello.



