Ransomware Attacks Targeting VMware ESXi Infrastructure
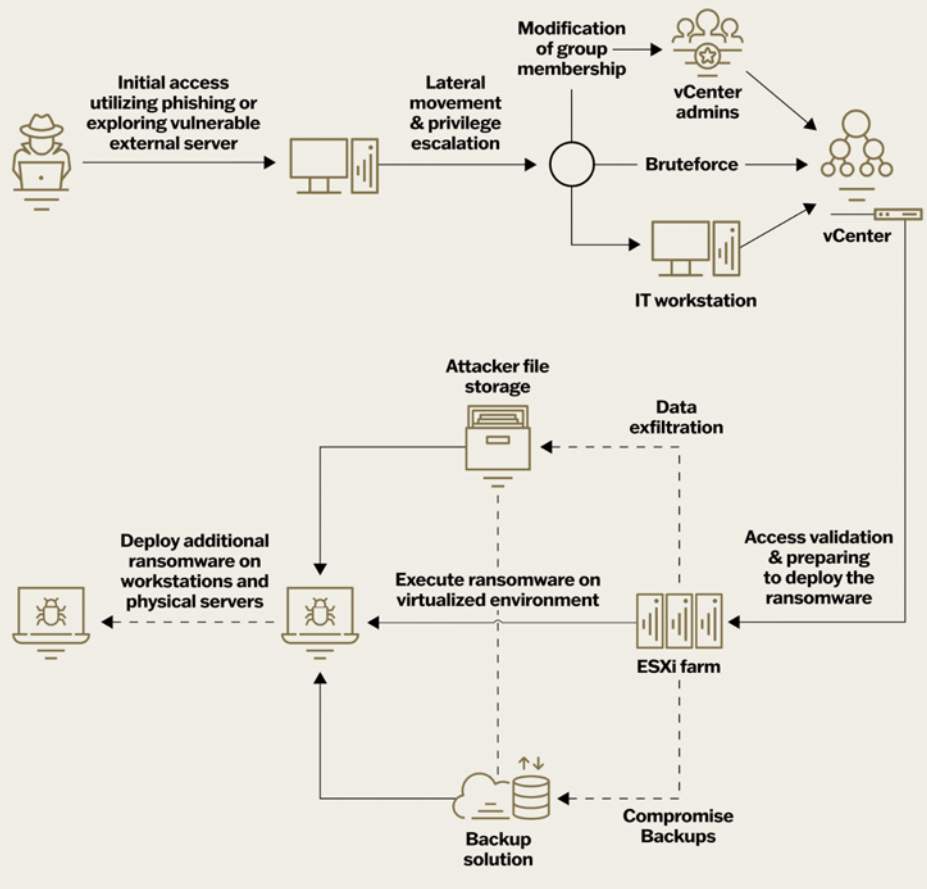
Recent findings reveal a troubling trend: ransomware attacks on VMware ESXi infrastructure follow a consistent pattern regardless of the variant used. The attack methodology typically begins with initial access through phishing, malicious downloads, or exploiting vulnerabilities in internet-facing assets. This is followed by privilege escalation, often via brute-force attacks, to obtain ESXi host or vCenter credentials. Attackers then validate their access to the virtualization environment and deploy the ransomware. They disrupt backups by deleting or encrypting them and changing passwords to hinder recovery efforts. Next, data is exfiltrated to external locations such as Mega.io or Dropbox. The ransomware is then executed, targeting the “/vmfs/volumes” folder of the ESXi filesystem, and the attack propagates to non-virtualized servers and workstations. To mitigate these risks, organizations should implement comprehensive monitoring and logging, develop robust and secure backup mechanisms, enforce strong multi-factor authentication, regularly update and securely configure their systems, and use network segmentation to limit lateral movement within the network. Understanding these attack patterns and applying these security measures can significantly enhance the protection of VMware ESXi infrastructures from ransomware threats.
The Attack Sequence
Initial Access:
Threat actors typically gain initial access through:
- Phishing Attacks: Leveraging deceptive emails to trick users into divulging credentials or downloading malicious files.
- Malicious File Downloads: Using infected files disguised as legitimate software.
- Exploitation of Vulnerabilities: Targeting known weaknesses in internet-facing assets.
Privilege Escalation
Once initial access is achieved, attackers:
- Brute-force Attacks: Attempt to crack passwords for ESXi hosts or vCenter.
- Credential Harvesting: Utilize other methods to obtain administrative credentials.
Infrastructure Validation and Ransomware Deployment:
- Validate Access: Ensure they have the necessary permissions within the virtualization environment.
- Deploy Ransomware: Position the ransomware for execution within the ESXi infrastructure.
Disruption of Backup Systems:
To complicate recovery efforts, attackers:
- Delete or Encrypt Backups: Remove or encrypt backup systems.
- Change Passwords: Modify passwords to prevent access to backup systems.
Data Exfiltration:
Before encrypting data, attackers often:
- Exfiltrate Data: Transfer data to external locations such as Mega.io, Dropbox, or private hosting services.
Ransomware Execution
The core ransomware attack involves:
- Encrypting ESXi Filesystem: Specifically targeting the “/vmfs/volumes” folder, critical to the ESXi infrastructure.
Propagation to Other Systems
Finally, the attack broadens its impact by:
- Infecting Non-Virtualized Systems: Spreading the ransomware to servers and workstations beyond the virtualization environment.
Ongoing Campaigns and Threats
- Malicious Ads and Typosquatting
Since early March 2024, Rapid7 has warned about campaigns using:
- Malicious Ads: Distributed on search engines.
- Trojanized Installers: For WinSCP and PuTTY, spread via typosquatted domains.
These counterfeit installers drop the Sliver post-exploitation toolkit, leading to the deployment of ransomware, including Cobalt Strike Beacon.
- BlackCat and Nitrogen Malware
These activities show similarities with previous BlackCat ransomware attacks that used:
- Malvertising: As an initial access vector.
- Nitrogen Malware: Part of a recurring campaign.
- Targeting IT Teams
The campaign mainly affects IT personnel, who are more likely to download these compromised files, providing threat actors with an elevated foothold and complicating analysis of their activities.
Emergence of New Ransomware Families
Notable New Ransomware Families: Recent months have seen the rise of new ransomware families such as:
- Beast
- MorLock
- Synapse
- Trinity
MorLock Group’s Tactics
The MorLock group has been aggressively targeting Russian companies, encrypting files without exfiltration, and demanding large ransoms.
Ransomware Attack Trends
Decline in Global Attacks
According to NCC Group, global ransomware attacks in April 2024 saw a 15% decline, from 421 to 356 attacks.
Changes in Prominent Threat Actors
- LockBit’s Decline: LockBit’s dominance ended due to a law enforcement takedown.
- Play and Hunters Rise: Play became the most active threat group, followed by Hunters.
Mitigation Strategies
To defend against these sophisticated attacks, organizations should implement the following measures:
- Monitoring and Logging: Ensure comprehensive monitoring and logging to detect unusual activities early.
- Robust Backup Mechanisms: Develop and maintain robust backup strategies, ensuring backups are secure and regularly tested.
- Strong Authentication: Enforce strong authentication measures, including multi-factor authentication, to protect access credentials.
- Environment Hardening: Harden the virtualization environment by:
- Regularly updating and patching software.
- Configuring systems securely.
- Minimizing exposed services.
- Network Restrictions: Implement network segmentation and restrictions to limit lateral movement within the network.



